Part VIII - Mail server installation and configuration
Install software
Debain comes with exim4 as its default MTA which we want to remove before proceeding.
Enter the following commands.
sudo apt-get remove exim4 exim4-base exim4-config exim4-daemon-light
sudo apt-get purge exim4 exim4-base exim4-config exim4-daemon-light
sudo apt-get autoremove
And now we can install the new software.
sudo apt-get install postfix postfix-mysql dovecot-core dovecot-imapd dovecot-pop3d dovecot-lmtpd dovecot-mysql postgrey opendkim opendkim-tools spamassassin smapc
Select “Internet host” and enter your domain when prompted. In this case it would be planetexpress.net
Configure Postfix
Most of the configuration of postfix is done in the main.cf and master.cf files which live in /etc/postfix
First create a backup directory and make a copy of the orginal files
sudo mkdir /etc/postfix/backup
sudo cp /etc/postfix/main.cf /etc/postfix/backup/main.cf
sudo cp /etc/postfix/master.cf /etc/postfix/backup/master.cf
Editing main.cf
Now edit the main.cf file with
sudo nano /etc/postfix/main.cf
and edit the following areas of the file.
smtpd_banner = planetexpress.net.in-addr.arpa ESMTP $mail_name (Debian/GNU)
# TLS parameters
smtpd_tls_cert_file=/etc/ssl/certs/planetexpress.pem
smtpd_tls_key_file=/etc/ssl/private/planetexpress.key
smtp_tls_CAfile=/etc/ssl/certs/ca-certificates.crt
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
mydestination = $myhostname, Old-Bessie.planetexpress.net, localhost.planetexpress.net, localhost
And then add the entire block below at the bottom of the file.
With the “TLS encryption” section you can change “may” to “encrypt” which means if someone sends you an email in an unencrypted transmission it will be refused. According to the postfix documentation you are not supposed to do this for internet facing servers. My mobile phone providers billing emails (lazy bastards) as an example are blocked for this very reason, hence I am using “may”.
# TLS encryption
smtpd_tls_security_level = may
smtp_tls_security_level = may
smtp_tls_mandatory_ciphers = high
smtpd_tls_loglevel = 1
# Enabling SMTP for authenticated users, and handing off authentication to Dovecot
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
reject_non_fqdn_sender,
reject_non_fqdn_recipient,
reject_unknown_sender_domain,
reject_unknown_recipient_domain,
reject_unauth_pipelining,
reject_invalid_hostname,
reject_non_fqdn_hostname,
reject_rbl_client zen.spamhaus.org,
#check_policy_service inet:127.0.0.1:10023,
#check_policy_service unix:private/policy-spf,
#check_sender_access hash:/etc/postfix/blacklist,
permit
#Handing off local delivery to Dovecot's LMTP, and telling it where to store mail
virtual_transport = lmtp:unix:private/dovecot-lmtp
#Virtual domains, users and aliases
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-mailbox-domains.cf
virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-mailbox-maps.cf
virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias-maps.cf
mysql:/etc/postfix/mysql-virtual-email2email.cf
#The following settings are used by DKIM
#milter_protocol = 2
#milter_default_action = accept
#smtpd_milters = inet:localhost:12301
#non_smtpd_milters = inet:localhost:12301
Some of these lines we will come back to later and uncomment once we configure other components.
Now we are going to create the four files listed under the “Virtual domains, users and aliases” section.
Enter the following command.
sudo nano /etc/postfix/mysql-virtual-mailbox-domains.cf
Enter the following text.
user = mailuser
password = fry
hosts = 127.0.0.1
dbname = mail
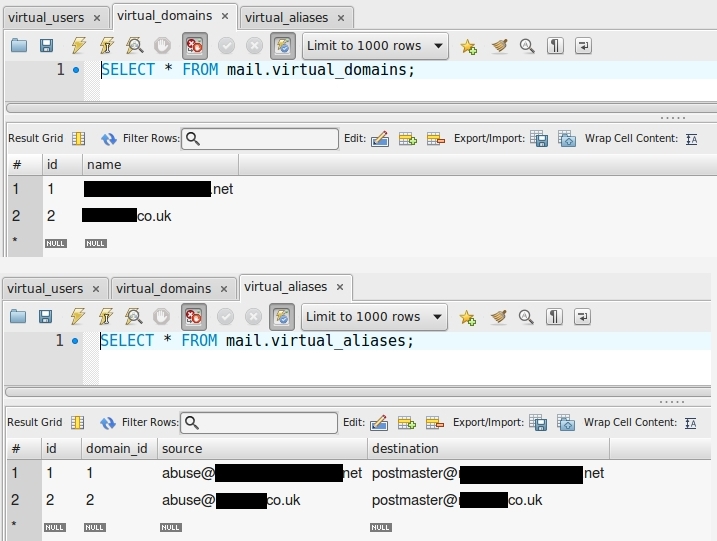
query = SELECT 1 FROM virtual_domains WHERE name='%s'
Exit and save the file.
Enter the following command.
sudo nano /etc/postfix/mysql-virtual-mailbox-maps.cf
Enter the following text.
user = mailuser
password = fry
hosts = 127.0.0.1
dbname = mail
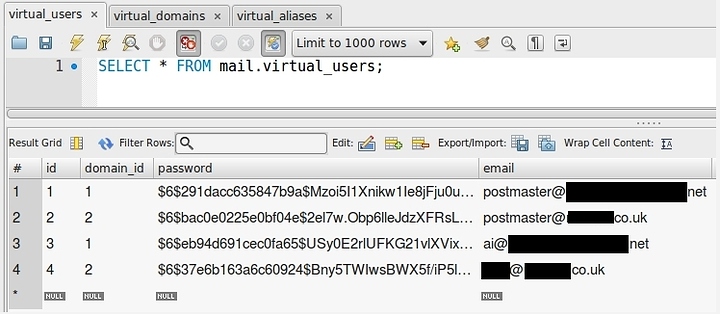
query = SELECT 1 FROM virtual_users WHERE email='%s'
Exit and save the file.
Enter the following command.
sudo nano /etc/postfix/mysql-virtual-alias-maps.cf
Enter the following text.
user = mailuser
password = fry
hosts = 127.0.0.1
dbname = mail
query = SELECT destination FROM virtual_aliases WHERE source='%s'
Exit and save the file.
Enter the following command.
sudo nano /etc/postfix/mysql-virtual-email2email.cf
Enter the following text.
user = mailuser
password = fry
hosts = 127.0.0.1
dbname = mail
query = SELECT email FROM virtual_users WHERE email='%s'
Exit and save the file.
Enter the following command.
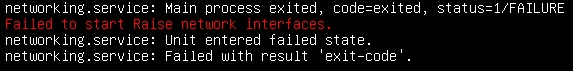
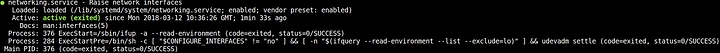
service postfix restart
You should get no errors which means postfix is (probably) happy with the configuration file.
Editing master.cf
Edit the master.cf file with the following command.
sudo nano /etc/postfix/master.cf
Uncomment the following section as shown. Make sure you uncomment the top line! This is something I have missed in the past and felt like a total dumbass. The rest of the file can be left as is.
submission inet n - - - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
-o smtpd_recipient_restrictions=
-o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
smtps inet n - - - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
-o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
-o smtpd_recipient_restrictions=
-o smtpd_relay_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
Exit and save the file.
sudo service postfix restart
If postfix fails to start the first place to look is in the following log files.
/var/log/mail.log
/var/log/syslog
/var/log/mail.info
/var/log/mail.warn
/var/log/mail.err
Configure Dovecot
Enter the following commands to backup the configuration files.
sudo mkdir /etc/dovecot/backup
sudo cp /etc/dovecot/dovecot.conf /etc/dovecot/backup
sudo cp /etc/dovecot/dovecot-sql.conf.ext /etc/dovecot/backup
sudo mkdir /etc/dovecot/conf.d/backup
sudo cp /etc/dovecot/conf.d/10-mail.conf /etc/dovecot/conf.d/backup
sudo cp /etc/dovecot/conf.d/10-auth.conf /etc/dovecot/conf.d/backup
sudo cp /etc/dovecot/conf.d/10-master.conf /etc/dovecot/conf.d/backup
sudo cp /etc/dovecot/conf.d/10-ssl.conf /etc/dovecot/conf.d/backup
Editing dovecot.conf
Enter the following command.
sudo nano /etc/dovecot/dovecot.conf
Edit the text block shown to include the third line.
# Enable installed protocols
!include_try /usr/share/dovecot/protocols.d/*.protocol
protocols = imap pop3 lmtp
Exit and save the file.
Enter the following command.
sudo nano /etc/dovecot/dovecot-sql.conf.ext
In this file there are four sections that need to be changed. In each example an additional section is left in to help you find what you are looking for.
# Database driver: mysql, pgsql, sqlite
driver = mysql
# Examples:
# connect = host=192.168.1.1 dbname=users
# connect = host=sql.example.com dbname=virtual user=virtual password=blarg
# connect = /etc/dovecot/authdb.sqlite
#
connect = host=127.0.0.1 dbname=mail user=mailuser password=fry
# Default password scheme.
#
# List of supported schemes is in
# http://wiki2.dovecot.org/Authentication/PasswordSchemes
#
default_pass_scheme = SHA512-CRYPT
# Example:
# password_query = SELECT userid AS user, pw AS password \
# FROM users WHERE userid = '%u' AND active = 'Y'
#
password_query = SELECT email as user, password FROM virtual_users WHERE email='%u';
Exit and save the file.
Enter the following command.
sudo nano /etc/dovecot/conf.d/auth-sql.conf.ext
Change the userdb section as shown.
userdb {
driver = static
args = uid=vmail gid=vmail home=/var/mail/vhosts/%d/%n
Exit and save the file.
Enter the following command.
sudo nano /etc/dovecot/conf.d/10-mail.conf
In this file there are two sections that need to be changed. In each example an additional section is left in to help you find what you are looking for.
# See doc/wiki/Variables.txt for full list. Some examples:
#
mail_location = maildir:~/var/mail/vhosts/%d/%n
# mail_location = mbox:~/mail:INBOX=/var/mail/%u
# mail_location = mbox:/var/mail/%d/%1n/%n:INDEX=/var/indexes/%d/%1n/%n
# Group to enable temporarily for privileged operations. Currently this is
# used only with INBOX when either its initial creation or dotlocking fails.
# Typically this is set to "mail" to give access to /var/mail.
mail_privileged_group = mail
The rest of the file can be left as is. Exit and save the file.
Enter the following command.
sudo ls -ld /var/mail
You should be returned the following output.
drwxrwsr-x 2 root mail 4096 Month Date Time /var/mail
Create the vmail user with the following commands.
groupadd -g 5000 vmail
useradd -g vmail -u 5000 vmail -d /var/mail
Make the vmail user the owner of the /var/mail folder
chown -R vmail:vmail /var/mail
Enter the following command again
ls -ld /var/mail
You should be returned the following output.
drwxrwsr-x 3 vmail vmail 4096 Month Date Time /var/mail
The vmail user is the account in charge of reading email from the server. Users emails will be stored in sub-folders within /var/mail/vhosts
Enter the following command.
sudo nano /etc/dovecot/conf.d/10-auth.conf
In this file there are three sections that need to be changed. In each example an additional section is left in to help you find what you are looking for.
# Disable LOGIN command and all other plaintext authentications unless
# SSL/TLS is used (LOGINDISABLED capability). Note that if the remote IP
# matches the local IP (ie. you're connecting from the same computer), the
# connection is considered secure and plaintext authentication is allowed.
# See also ssl=required setting.
disable_plaintext_auth = yes
# Space separated list of wanted authentication mechanisms:
# plain login digest-md5 cram-md5 ntlm rpa apop anonymous gssapi otp skey
# gss-spnego
# NOTE: See also disable_plaintext_auth setting.
auth_mechanisms = plain login
#!include auth-system.conf.ext
!include auth-sql.conf.ext
#!include auth-ldap.conf.ext
#!include auth-passwdfile.conf.ext
#!include auth-checkpassword.conf.ext
#!include auth-vpopmail.conf.ext
#!include auth-static.conf.ext
The rest of the file can be left as is. Exit and save the file.
Enter the following command.
sudo nano /etc/dovecot/conf.d/10-master.conf
In this file there are six sections that need to be changed and one that needs to be added (the third block below). In each example an additional section is left in to help you find what you are looking for.
service imap-login {
inet_listener imap {
#port = 143
}
inet_listener imaps {
port = 993
ssl = yes
}
service pop3-login {
inet_listener pop3 {
#port = 110
}
inet_listener pop3s {
port = 995
ssl = yes
}
}
service lmtp {
unix_listener /var/spool/postfix/private/dovecot-lmtp {
mode = 0600
user = postfix
group = postfix
}
unix_listener /var/spool/postfix/private/auth {
mode = 0666
user = postfix
group = postfix
}
unix_listener auth-userdb {
mode = 0600
user = vmail
#group =
}
# Auth process is run as this user.
user = dovecot
service auth-worker {
# Auth worker process is run as root by default, so that it can access
# /etc/shadow. If this isn't necessary, the user should be changed to
# $default_internal_user.
user = vmail
}
Don’t miss the last curly bracket!.
The rest of the file can be left as is. Exit and save the file.
Enter the following command.
sudo nano /etc/dovecot/conf.d/10-ssl.conf
In this file there is two sections that need to be changed. In each example it is the highlighted section that needs to be changed. The additional section is left in to help you find what you are looking for.
# SSL/TLS support: yes, no, required. <doc/wiki/SSL.txt>
ssl = required
# PEM encoded X.509 SSL/TLS certificate and private key. They're opened before
# dropping root privileges, so keep the key file unreadable by anyone but
# root. Included doc/mkcert.sh can be used to easily generate self-signed
# certificate, just make sure to update the domains in dovecot-openssl.cnf
ssl_cert = </etc/ssl/certs/planetexpress.pem
ssl_key = </etc/ssl/private/planetexpress.key
The rest of the file can be left as is. Exit and save the file and restart dovecot.
sudo service dovecot restart
Now at this point we should have a functioning email server. You can try sending and receiving some test emails.
The following commands will output your alterations to the default configurations.
sudo postconf -n
sudo dovecot -n
But we still have much to do…