First, some background. You can skip that if you’re just here to unbrick your cameras, and understand a few things about how they are put together.
Hikvision – What do new buyers need to know?
Hikvision is a huge manufacturer. They make cameras under a lot of brand names. You may be buying Hikvision, and not even know it. Sadly, a lot of other IP cameras have inferior build quality, but better software.
In general, my opinion of Hikvision hardware is that it is really quite good. I have also extensively used
*Wyze cameras
*Ubiquti cameras
*Grandstream
*Reolink
*Amcrest
It is my opinion that Hikvision hardware is superior, but the other cameras are less dangerous. Particularly disappointing is Ubiquti cameras because the company apparently gets what they need to do for a good security camera experience, but they completely fall short on long-term reliability and build quality. They’re nearly good enough but fall short in just a few key areas (imho).
Conversely, it is nearly impossible to permanently kill a Hikvision camera. It is easy to brick one with a failed firmware update, and it is not well-documented how to recover. Hence this guide.
That said, Hikvision is taking the tiger by the tail, a bit. If you prefer a little less international intrigue and/or having the Rawling Virus in-a-jar on your network, I might recommend Reolink or Ubiquiti in a pinch.
Important: Hikvision Cameras labeled “EOL” are extremely problematic with regard to firmware versions and updates. ALWAYS ALWAYS check that a Hikvision camera you are buying new is not EOL and has recent firmware. For example, it is still possible to buy 2CD2085FWD-I 8 megapixel H265 PoE Hikvision cameras on Amazon. Do not do that unless you like pain and suffering; the current firmware versions are bugged and this version of that camera sucks. It was replaced by 2CD2085G-I (are you as frustrated reading these camera models as I am writing them down?)
Cloud camera services are for chumps. Don’t be a chump.
Hikvision Background
Hikvision (Pronounced High-Kay-Vision. Yes, really) is short for Hangzhou Hikvision Digital Technology Co, LTD. partially state-owned Chinese manufacturer and supplier of video surveillance equipment for civilian and military purposes, headquartered in Hangzhou, China.
The vision for robust camera equipment, and the implementation, is massively impressive. The hardware truly is incredible as it is able to, in real time, do face detection, people counting, detect and flag unattended baggage or packages, identify animals and much more.
The software, on the other hand, is not to idealistic American standards. It is apparent the software was not built with hardening or security in mind. The main problem is that the software is a bit opaque and the known security issues in the past have been jaw-droppingly bad.
However, the cameras do include a very well-documented SDK for software development. They also offer industry standard functionality such as web sockets and RTMP.
Even though they are a security nightmare they can, in some respects, be a great platform for video capture (3840x2160x20 fps for the models featured in this video).
Software Security
Hikvision is kinda sorta on the US blacklist. Is the security insecure because it has backdoors from China, or is it just dangerously insecure because it was not coded to any kind of software engineering standards? It’s not clear on that point. But it is absolutely imperative that, if you use this equipment, that it is not on the internet (even behind NAT).
In an ideal world there would be open firmware for these cameras, ideally from some third party. Some noted security researchers have really put a lot of work into trying to tear these down, and some have lamented that the boot sequence on these cameras seems incredibly obfuscated and needlessly complex. Why go to all the trouble given the past security weaknesses?
Some notable security lapses from discovered in the past:
It’s unclear if this is a feature or a bug, but it is possible to use SSH to get a bash prompt. (Normally these cameras restrict ssh to the ‘psh’ shell, which only allows a limited set of commands).
ssh root@hikvisioncam /bin/sh
ssh root@hikvisioncam /bin/bash
YMMV on this one because newer firmwares kill that.
Hikvision is aware of their security reputation to the extent that they pay for Google ads whenever you search for “hikvision vulnerability”
The guide is a genuinely helpful guide for securing and configuring your Hikvision gear; they do want you to have secure gear to the extent that the criminals-du-jour are not exploiting the camera hardware to mine cryptocurrency or participate in DDoS attacks.
Why hack security cameras? In addition to the ability to stream video (and sometimes audio) for operational insight into the environment of the camera, typical Hikvision IP cameras have fairly powerful CPUs in them – they are ARM-based and typically fairly powerful. They do a lot of processing right on the camera which means that whether you deploy 10 or 100 cameras, the “backend” storage requirements tend to be pretty modest.
Almost all of these cameras feature an on-board microSD slot. If you intend to use local storage with the cameras, I highly recommend getting extremely high endurance microSD cards, designed for surveillance apps, which are only just starting to become marketed as such in the west.
Hikvision Cameras, How do they work, for recovery?
This was not well documented, and would have helped me save countless hours from the start, in helping a regional product distributor root-cause customer returns and camera failures.
In firmwares before about 5.0.0 (this will vary hugely, more on that in a moment) ALL older Hikvision cameras were factory set at 192.0.0.64 and were programmed to try to load firmware from TFTP via 192.0.0.128 – even new Hikvision cameras will try to do this if they’re really, really screwed up.
Later, some of the documentation and newer firmware refer to 192.168.1.64 this is the default IP address of the camera on newer firmwares (~~5.0+)
The default TFTP server it tries to connect to in that case is 192.168.1.128
The TFTP server is a non-standard one however. Hikvision publishes a TFTP update tool, but it is buggy and does not work well on anything other than Windows XP.
Instead, I recommend this Python script put together by Scott Lamb:
If you are not familiar with what TFTP is, it is a trivial file transfer protocol. It is not built for speed, or redundancy, or reliability. Neither is the Hikvision update process. TFTP, and these IP addresses, are the cornerstone of being able to recover these cameras quickly and properly. You will waste a lot of time if you do not perform the firmware recoveries/updates from a hard-wired computer with a manually configured IP address.
Be aware that different regions (US, UK, Netherlands, EU, China/Asia Pacific) all have slightly different firmwares AND slightly different camera builds. It can be super annoying finding the right camera, and the right region, to download the correct version of the firmware.
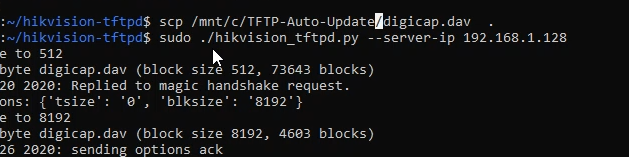
All you have to do is copy the correct digicap.dav file that corresponds to your exact camera to the tftp directory and then run the hikvision_tftp.py file to start the tftp server.

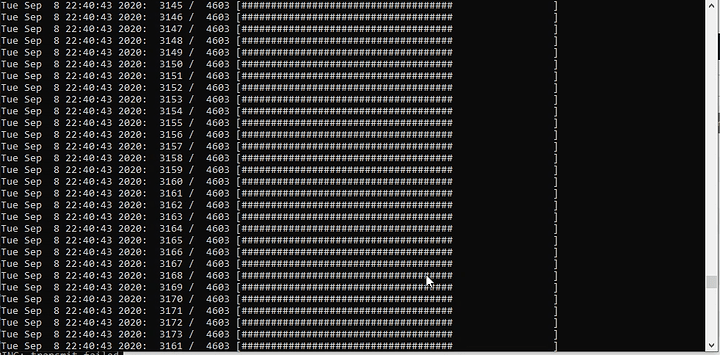
It provides a lot of verbose output when it is working correctly (unlike Hikvision’s program), including a helpful progress indicator:
You must used a wired connection for this to be a reliable operation. TFTP is not a robust protocol, and neither is the Hikvision implementation.
Booting The Camera
During the camera bootup sequence, a “primary” block of flash in the boot loader establishes ethernet link and sets the camera IP to 192.168.1.64* and tries to contact 192.168.1.128 to tftp its firmware file. (On every boot. Don’t even have to hold the reset button…) The camera web gui has a few checks to prevent firmware downgrades, but the TFTP sequence may permit downgrades. It seems as though some regions of flash cannot be overwritten and you can get into weird situations.
It is possible to corrupt your newer-firmware camera so badly that it will revert to the old school 192.0.0.64 → 192.0.0.128 – if that happens you should try to load the firmware again from that interface.
The box that the camera original came in tells you the exact firmware version that it ships with. This can be useful for getting to a “known good” starting position.
No matter what camera you have (except the 7+ year old ones) the firmware filename will be digicap.dav but the contents are highly specific to both the camera model and global region where it was sold (in some, but not all, cases).
In the YouTube video, I showed how to recover the 2CD2085G-I and it’s evil twin brother, the 2CD2085FWD-I using the hikvision TFTP python script (linked above) and the method I used to find the right firmware for the 'FWD (basically, binary search on the netherland’s website).
In this case, the failure of that particular camera was a head-scratcher. It means the distributor’s supplier must have improperly substituted a case of cameras meant for the Netherlands for US distribution.
Further Troubleshooting
If, upon setting your IP addresses correctly, you see no activity and the camera seems dead there are two options. The first is to use wireshark to observe the network and see what you can see:
sudo tcpdump -i eth0 -vv -e -nn ether proto 0x0806
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
16:21:58.804425 28:57:be:8a:aa:53 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 172.9.18.80 tell 172.9.18.100, length 46
16:22:00.805251 28:57:be:8a:aa:53 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 172.9.18.80 tell 172.9.18.100, length 46
This is a bit outside the scope of this document. In this case, this is some fabulously ancient Hikvision firmware using 172.9.18.80 IP addresses instead of 192.0.0.64 – but this is equipment so old it isn’t worth fixing IMHO
The second option is to attach a cable to the serial console. As these cameras run Linux under the hood, they do output to a built-in serial console. This may involve soldering or building a special console cable with a header such as:

This is not for the feint of heart, but it is a fun exercise. Happy hacking! Honorable mention toward that “Let’s do some custom open firmware for this killer hardware!”