Sounds like I should just do a fresh install then. Thanks
No need to do a full reinstall, just do a reinstall of systemd-boot.
I don’t think his issue is systemd-boot. His issue is that after he installed Pop!_OS on another drive he can no longer boot into the Windows drive even when he selects the drive Windows is installed on from the motherboard’s boot menu. Still think he should try Window’s boot repair utility from the Window’s install media first.
The issue is if he had other drives installed at some point sometimes for some reason Windows will move it’s bootloader to a different drive in the system other than the one Windows is installed on. Happens due to updates and I have no idea what Windows does during updates that causes this bug to happen. Have had it happen to several of my machines and sometimes only discovered it when I took my storage drive out to quickly move a bunch of data to only find my machine no longer booted without the storage drive installed. Not 100% sure all the things he’s done with the system recently when he did the Pop!_OS install since he hasn’t elaborated.
Soooo…
I just god a popup that my Disk Space is running low, and checking FIlelight to see where the hell it went, it turns out my /var/log is getting close to 10gig now…
Well, that’s one thing, but then I also checked journal -b --reverse and I am getting literall hundreds of thousands of log messages like this:
Nov 02 23:00:19 localhost.localdomain audit[579316]: AVC avc: denied { unlink } for pid=579316 comm="sssd_ssh" name=>
Nov 02 23:00:19 localhost.localdomain audit[579317]: AVC avc: denied { unlink } for pid=579317 comm="sssd_nss" name=>
Nov 02 23:00:19 localhost.localdomain sssd_nss[579317]: Starting up
Nov 02 23:00:19 localhost.localdomain sssd_ssh[579316]: Starting up
Nov 02 23:00:19 localhost.localdomain rsyslogd[1128]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjour>
Nov 02 23:00:19 localhost.localdomain audit[1128]: AVC avc: denied { unlink } for pid=1128 comm="in:imjournal" name=>
Nov 02 23:00:19 localhost.localdomain rsyslogd[1128]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjour>
Nov 02 23:00:19 localhost.localdomain audit[1128]: AVC avc: denied { unlink } for pid=1128 comm="in:imjournal" name=>
Nov 02 23:00:19 localhost.localdomain rsyslogd[1128]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjour>
Nov 02 23:00:19 localhost.localdomain audit[1128]: AVC avc: denied { unlink } for pid=1128 comm="in:imjournal" name=>
Nov 02 23:00:19 localhost.localdomain rsyslogd[1128]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjour>
Nov 02 23:00:19 localhost.localdomain audit[1128]: AVC avc: denied { unlink } for pid=1128 comm="in:imjournal" name=>
Nov 02 23:00:19 localhost.localdomain audit[579310]: AVC avc: denied { unlink } for pid=579310 comm="sssd_nss" name=>
Nov 02 23:00:19 localhost.localdomain audit[579312]: AVC avc: denied { unlink } for pid=579312 comm="sssd_ssh" name=>
Nov 02 23:00:18 localhost.localdomain audit[579315]: AVC avc: denied { unlink } for pid=579315 comm="sssd_pam" name=>
Nov 02 23:00:18 localhost.localdomain audit[579314]: AVC avc: denied { unlink } for pid=579314 comm="sssd_sudo" name>
Nov 02 23:00:18 localhost.localdomain sssd_nss[579310]: Starting up
Nov 02 23:00:18 localhost.localdomain sssd_ssh[579312]: Starting up
Nov 02 23:00:18 localhost.localdomain audit[579311]: AVC avc: denied { unlink } for pid=579311 comm="sssd_pam" name=>
Nov 02 23:00:18 localhost.localdomain audit[579313]: AVC avc: denied { unlink } for pid=579313 comm="sssd_sudo" name>
Nov 02 23:00:18 localhost.localdomain audit[579309]: AVC avc: denied { read } for pid=579309 comm="sssd_be" name="in>
Nov 02 23:00:18 localhost.localdomain audit[579309]: AVC avc: denied { read } for pid=579309 comm="sssd_be" name="in>
Nov 02 23:00:18 localhost.localdomain audit[579309]: AVC avc: denied { read } for pid=579309 comm="sssd_be" name="pa>
Nov 02 23:00:18 localhost.localdomain audit[579309]: AVC avc: denied { read } for pid=579309 comm="sssd_be" name="pa>
Nov 02 23:00:18 localhost.localdomain sssd_be[579309]: Starting up
And no, I’m not joking about hundreds of thousands. I stopped scrolling at line 70.000 and that was an hour ago…
Any idea what the hell this even is or why it’s failing? Is it failing to start whatever it is because the disk is getting full and filling the log because of it?
Just while typing this, it filled another 5 MB…
edit:
seems this has been going on a couple days…
[tarulia@localhost]~% ls /var/log -lh | grep "G "
-rw-------. 1 root root 1.5G Nov 2 23:34 messages
-rw-------. 1 root root 2.1G Oct 30 16:11 messages-20211024
-rw-------. 1 root root 1.9G Nov 1 01:41 messages-20211031
And for the journal:
[tarulia@localhost]~% ls /var/log/journal/45a1b5f2623c470f8974756d48b6e068 -lh
total 4.1G
-rw-r-----+ 1 root systemd-journal 80M Oct 30 00:02 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000060943d-0005cf83130d0471.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 02:18 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000061c7dc-0005cf84fb16f452.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 04:33 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000062ff48-0005cf86e2c7c10c.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 06:49 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000064377e-0005cf88c6189c2b.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 09:05 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000006565a5-0005cf8aacb8587f.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 11:21 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000066943b-0005cf8c90da2728.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 13:37 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000067c203-0005cf8e775643ec.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 30 15:52 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000068f04a-0005cf905cffdd91.journal
-rw-r-----+ 1 root systemd-journal 112M Oct 30 23:07 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000006a1e8c-0005cf9242104120.journal
-rw-r-----+ 1 root systemd-journal 112M Oct 30 23:08 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000006bdce0-0005cf9855bb7be4.journal
-rw-r-----+ 1 root systemd-journal 112M Oct 30 23:09 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000006db5a3-0005cf985963fe3d.journal
-rw-r-----+ 1 root systemd-journal 112M Oct 30 23:45 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000006f96b0-0005cf985c7f19a2.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 02:01 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000714c81-0005cf98dd094172.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 03:17 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000727e39-0005cf9ac3f40a06.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 05:33 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000073b158-0005cf9ca9269c69.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 17:56 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000074e2f2-0005cf9e9128f0bc.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 20:13 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007615d1-0005cfa8f14e5b5a.journal
-rw-r-----+ 1 root systemd-journal 80M Oct 31 22:29 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007747ba-0005cfaadb2487b8.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 00:46 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007879b4-0005cfacc317a796.journal
-rw-r-----+ 1 root systemd-journal 88M Nov 1 01:43 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000079ab9a-0005cfaeac5c7860.journal
-rw-r-----+ 1 root systemd-journal 104M Nov 1 01:44 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007b3de1-0005cfaf7734b6e0.journal
-rw-r-----+ 1 root systemd-journal 112M Nov 1 01:45 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007d13c9-0005cfaf7b1f35f0.journal
-rw-r-----+ 1 root systemd-journal 112M Nov 1 01:46 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000007ef6af-0005cfaf7e32e40f.journal
-rw-r-----+ 1 root systemd-journal 88M Nov 1 03:59 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000080db71-0005cfaf813fa9b3.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 06:15 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000082118d-0005cfb15d97fdc5.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 08:31 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008343e3-0005cfb343668f8a.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 10:47 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000847324-0005cfb52abd7508.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 13:00 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000085a0cf-0005cfb710f0a9d7.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 15:16 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000086d560-0005cfb8ecbec432.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 17:31 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008803f6-0005cfbad1689ada.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 19:46 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008934ed-0005cfbcb44421f4.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 1 22:02 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008a638a-0005cfbe9a12d9fa.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 00:19 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008b958e-0005cfc07efde7ab.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 02:35 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008cc750-0005cfc268789ac7.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 04:51 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008df8b9-0005cfc4508b764d.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 07:07 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000008f268d-0005cfc6372af6de.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 09:23 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000905474-0005cfc81d0a4d16.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 11:36 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000918231-0005cfca02f08157.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 13:50 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000092b6c9-0005cfcbddfbfcaa.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 16:06 system@6e6d1adefe5848eda346d9f0ebb3c6f1-000000000093e87a-0005cfcdbd75b59e.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 18:22 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000951831-0005cfcfa2a221a0.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 20:37 system@6e6d1adefe5848eda346d9f0ebb3c6f1-00000000009646ff-0005cfd18a02987b.journal
-rw-r-----+ 1 root systemd-journal 80M Nov 2 22:52 system@6e6d1adefe5848eda346d9f0ebb3c6f1-0000000000977e96-0005cfd36d3856a5.journal
-rw-r-----+ 1 root systemd-journal 72M Nov 3 00:35 system.journal
-rw-r-----+ 1 root systemd-journal 24M Oct 29 21:45 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000005f1f78-0005cf813fa46684.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 00:02 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000006096bc-0005cf8316da6168.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 02:18 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000061e751-0005cf852da1b0ed.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 04:33 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000063004b-0005cf86e489996d.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 06:49 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000644824-0005cf88e0e7a7ab.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 09:05 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000065805f-0005cf8ad7b017d2.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 11:21 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000066ae1f-0005cf8cba7c4b08.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 13:37 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000067d97f-0005cf8e9d488ae5.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 15:52 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000068f445-0005cf90636ffb50.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 23:07 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000006a32f8-0005cf9262e0e54d.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 23:08 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000006c1abe-0005cf9856353815.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 23:09 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000006dbfcc-0005cf985977f1d5.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 30 23:45 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000006ffc66-0005cf985d27d4a8.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 02:01 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000071516e-0005cf98e50e83ec.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 03:17 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000728858-0005cf9ad43af061.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 05:33 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000073b911-0005cf9cb5ab1bc8.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 17:56 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000007509b0-0005cf9ecf24e832.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 20:13 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000076274d-0005cfa90d57ee62.journal
-rw-r-----+ 1 root systemd-journal 8.0M Oct 31 22:29 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000774ad1-0005cfaae026b0ec.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 00:46 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000787b8a-0005cfacc5ddb1cd.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 01:43 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000079aeac-0005cfaeb16ebd15.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 01:44 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000007b92d8-0005cfaf77cccc56.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 01:45 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000007d3660-0005cfaf7b5c7cad.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 01:46 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000801dcd-0005cfaf80114816.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 03:59 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000080f0ba-0005cfaf96f289b4.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 06:15 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000008272d1-0005cfb1f81220a4.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 08:31 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000835a85-0005cfb367ce02dd.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 10:47 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000855fc9-0005cfb6a8001db3.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 13:00 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000085bcfc-0005cfb73e59a8bc.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 15:16 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000086e466-0005cfb904a80369.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 17:31 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000880a04-0005cfbadb03caa0.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 19:46 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000894f48-0005cfbcdeba6ae8.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 1 22:02 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000008a7a66-0005cfbebec15196.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 00:19 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000008b9e33-0005cfc08cdd86c8.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 02:35 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000008d76d1-0005cfc381c8599d.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 07:07 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000008f3bd5-0005cfc6591c40be.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 09:23 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000090783d-0005cfc856c11916.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 11:36 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000091de4e-0005cfca97208942.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 13:50 user-1000@e9fe74733a294831b0ff8e44725576c2-000000000092bbd9-0005cfcbe61d1fac.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 16:06 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000009405f1-0005cfcdeccd6d04.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 18:22 user-1000@e9fe74733a294831b0ff8e44725576c2-00000000009519a2-0005cfcfa4ea4b35.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 20:37 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000965883-0005cfd1a6308611.journal
-rw-r-----+ 1 root systemd-journal 8.0M Nov 2 22:52 user-1000@e9fe74733a294831b0ff8e44725576c2-0000000000977eac-0005cfd36d5ea031.journal
-rw-r-----+ 1 root systemd-journal 16M Nov 3 00:35 user-1000.journal
you’ll notice that the system logs are huge and I have no idea what happened there since the only config I changed recently was something related to pulseaudio. I mean 400MB of logs in 4 minutes is seriously impressive. What the actual hell?
Tried the utility you mentioned, didn’t work. Just went ahead and reinstalled Mint and Win10 on one drive at a time
This doesn’t address your underlying problem, but…
I imagine you don’t need that. It’s an old rsyslog file which I suppose the systemd journals subsume. On Ubuntu it’s been turned off in /etc/rsyslog.d/50-default.conf by being commented out for years now.
You’ve somehow invoked the wrath of SELinux.
Your copy/paste truncated the messages to 120 columns, so it’s hard to tell what the problem is.
You can use audit2allow to fix those errors: 10.3.8. Allowing Access: audit2allow
That’s sort of what I thought? The only thing I did with SEL recently was turning it off and on for this discussion above 
Maybe the editing the config to disable it initially messed with it, although I restored it to what it was 
Yeah I noticed that just before I went to bed so I didn’t fix it, well, here’s from the Terminal in Fullscreen, so it’s not getting bigger then that 
-- Logs begin at Sat 2021-10-30 09:16:54 CEST, end at Wed 2021-11-03 11:45:18 CET. --
Nov 03 11:45:18 localhost.localdomain NetworkManager[1236]: <info> [1635936318.3751] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:18 localhost.localdomain NetworkManager[1236]: <info> [1635936318.3745] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:17 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:17 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:17 localhost.localdomain audit[8946]: AVC avc: denied { unlink } for pid=8946 comm="sssd_nss" name="nss" dev="dm-0" ino=1048930 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:17 localhost.localdomain sssd_nss[8946]: Starting up
Nov 03 11:45:17 localhost.localdomain audit[8945]: AVC avc: denied { unlink } for pid=8945 comm="sssd_ssh" name="ssh" dev="dm-0" ino=1048888 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:17 localhost.localdomain sssd_ssh[8945]: Starting up
Nov 03 11:45:17 localhost.localdomain audit[8944]: AVC avc: denied { unlink } for pid=8944 comm="sssd_pam" name="pam" dev="dm-0" ino=1048901 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:17 localhost.localdomain audit[8943]: AVC avc: denied { unlink } for pid=8943 comm="sssd_sudo" name="sudo" dev="dm-0" ino=1048898 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive>
Nov 03 11:45:15 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:15 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:15 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:15 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:15 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:15 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:15 localhost.localdomain audit[8942]: AVC avc: denied { unlink } for pid=8942 comm="sssd_nss" name="nss" dev="dm-0" ino=1048930 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain sssd_nss[8942]: Starting up
Nov 03 11:45:15 localhost.localdomain audit[8941]: AVC avc: denied { unlink } for pid=8941 comm="sssd_ssh" name="ssh" dev="dm-0" ino=1048888 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain sssd_ssh[8941]: Starting up
Nov 03 11:45:15 localhost.localdomain audit[8935]: AVC avc: denied { unlink } for pid=8935 comm="sssd_nss" name="nss" dev="dm-0" ino=1048930 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8937]: AVC avc: denied { unlink } for pid=8937 comm="sssd_ssh" name="ssh" dev="dm-0" ino=1048888 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8940]: AVC avc: denied { unlink } for pid=8940 comm="sssd_pam" name="pam" dev="dm-0" ino=1048901 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8939]: AVC avc: denied { unlink } for pid=8939 comm="sssd_sudo" name="sudo" dev="dm-0" ino=1048898 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive>
Nov 03 11:45:15 localhost.localdomain audit[8936]: AVC avc: denied { unlink } for pid=8936 comm="sssd_pam" name="pam" dev="dm-0" ino=1048901 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain sssd_nss[8935]: Starting up
Nov 03 11:45:15 localhost.localdomain sssd_ssh[8937]: Starting up
Nov 03 11:45:15 localhost.localdomain audit[8938]: AVC avc: denied { unlink } for pid=8938 comm="sssd_sudo" name="sudo" dev="dm-0" ino=1048898 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive>
Nov 03 11:45:15 localhost.localdomain audit[8934]: AVC avc: denied { read } for pid=8934 comm="sssd_be" name="initgroups" dev="dm-0" ino=1049281 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8934]: AVC avc: denied { read } for pid=8934 comm="sssd_be" name="initgroups" dev="dm-0" ino=1049281 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8934]: AVC avc: denied { read } for pid=8934 comm="sssd_be" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8934]: AVC avc: denied { read } for pid=8934 comm="sssd_be" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain sssd_be[8934]: Starting up
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="initgroups" dev="dm-0" ino=1049281 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="initgroups" dev="dm-0" ino=1049281 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain sssd[8933]: Starting up
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { write } for pid=8933 comm="sssd" name="nss" dev="dm-0" ino=1048930 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain audit[8933]: AVC avc: denied { read } for pid=8933 comm="sssd" name="passwd" dev="dm-0" ino=1049036 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=file permissive=0
Nov 03 11:45:15 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:15 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:15 localhost.localdomain systemd[1]: Starting System Security Services Daemon...
Nov 03 11:45:15 localhost.localdomain audit[1]: SERVICE_STOP pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=sssd comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'
Nov 03 11:45:15 localhost.localdomain audit[1]: SERVICE_START pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=sssd comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'
Nov 03 11:45:15 localhost.localdomain systemd[1]: Stopped System Security Services Daemon.
Nov 03 11:45:15 localhost.localdomain systemd[1]: sssd.service: Scheduled restart job, restart counter is at 162.
Nov 03 11:45:15 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:15 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:14 localhost.localdomain audit[1]: SERVICE_START pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=sssd comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=failed'
Nov 03 11:45:14 localhost.localdomain systemd[1]: Failed to start System Security Services Daemon.
Nov 03 11:45:14 localhost.localdomain systemd[1]: sssd.service: Failed with result 'exit-code'.
Nov 03 11:45:14 localhost.localdomain systemd[1]: sssd.service: Main process exited, code=exited, status=1/FAILURE
Nov 03 11:45:14 localhost.localdomain sssd_be[8911]: Shutting down (status = 0)
Nov 03 11:45:14 localhost.localdomain audit[8932]: AVC avc: denied { unlink } for pid=8932 comm="sssd_pam" name="pam" dev="dm-0" ino=1048901 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:14 localhost.localdomain sssd[8910]: Exiting the SSSD. Could not restart critical service [sudo].
Nov 03 11:45:14 localhost.localdomain audit[8931]: AVC avc: denied { unlink } for pid=8931 comm="sssd_sudo" name="sudo" dev="dm-0" ino=1048898 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive>
Nov 03 11:45:14 localhost.localdomain NetworkManager[1236]: <info> [1635936314.7453] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:14 localhost.localdomain NetworkManager[1236]: <info> [1635936314.7446] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:11 localhost.localdomain rsyslogd[1113]: imjournal: rename() failed for new path: '/var/lib/rsyslog/imjournal.state': Permission denied [v8.2010.0 try https://www.rsyslog.com/e/0 ]
Nov 03 11:45:11 localhost.localdomain audit[1113]: AVC avc: denied { unlink } for pid=1113 comm="in:imjournal" name="imjournal.state" dev="dm-0" ino=1049159 scontext=system_u:system_r:syslogd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=fil>
Nov 03 11:45:10 localhost.localdomain audit[8923]: AVC avc: denied { unlink } for pid=8923 comm="sssd_ssh" name="ssh" dev="dm-0" ino=1048888 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:10 localhost.localdomain audit[8922]: AVC avc: denied { unlink } for pid=8922 comm="sssd_nss" name="nss" dev="dm-0" ino=1048930 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:10 localhost.localdomain sssd_ssh[8923]: Starting up
Nov 03 11:45:10 localhost.localdomain sssd_nss[8922]: Starting up
Nov 03 11:45:10 localhost.localdomain NetworkManager[1236]: <info> [1635936310.8753] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:10 localhost.localdomain NetworkManager[1236]: <info> [1635936310.8747] policy: set-hostname: current hostname was changed outside NetworkManager: 'localhost.localdomain'
Nov 03 11:45:10 localhost.localdomain audit[8921]: AVC avc: denied { unlink } for pid=8921 comm="sssd_pam" name="pam" dev="dm-0" ino=1048901 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive=0
Nov 03 11:45:10 localhost.localdomain audit[8920]: AVC avc: denied { unlink } for pid=8920 comm="sssd_sudo" name="sudo" dev="dm-0" ino=1048898 scontext=system_u:system_r:sssd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=sock_file permissive>
I’ll check that, thanks
Hm but they still seem to be used in some capacity, seeing as the files are new 
You can pipe systemd commands to cat to prevent the truncation to your terminal width. eg.
journalctl -xe | cat
OK so I went through those docs, and as far as I can see, the cause is the same for all of the logs:
Was caused by:
Missing type enforcement (TE) allow rule.
You can use audit2allow to generate a loadable module to allow this access.
Going further I get this:
[tarulia@localhost]~% sudo audit2allow -a
#============= NetworkManager_t ==============
allow NetworkManager_t unlabeled_t:file unlink;
#============= accountsd_t ==============
allow accountsd_t unlabeled_t:file read;
allow accountsd_t unlabeled_t:sock_file write;
#============= alsa_t ==============
allow alsa_t unlabeled_t:file { read unlink };
#============= chkpwd_t ==============
allow chkpwd_t unlabeled_t:file read;
allow chkpwd_t unlabeled_t:sock_file write;
#============= cupsd_t ==============
allow cupsd_t unlabeled_t:file { read unlink };
allow cupsd_t unlabeled_t:sock_file write;
#============= policykit_auth_t ==============
allow policykit_auth_t unlabeled_t:file read;
allow policykit_auth_t unlabeled_t:sock_file write;
#============= policykit_t ==============
allow policykit_t unlabeled_t:file read;
allow policykit_t unlabeled_t:sock_file write;
#============= sssd_t ==============
allow sssd_t unlabeled_t:file read;
allow sssd_t unlabeled_t:sock_file { unlink write };
#============= syslogd_t ==============
allow syslogd_t unlabeled_t:file unlink;
#============= systemd_tmpfiles_t ==============
#!!!! This avc can be allowed using the boolean 'domain_can_mmap_files'
allow systemd_tmpfiles_t unlabeled_t:file map;
The doc suggests opening a bugreport with RedHat, but I’m not sure how useful that is seeing as F33 is pretty much EOL and I’m probably going to reinstall soon-ish anyway.
They also suggest posting the resulting rule to the mailing list for review, but I think I’m going to skip that too as this is hopefully just temporary 
edit:
That seems to have done it, although I have no idea what it really did and that bothers me a bit. SEL from the outside looks just like a black hole of insanity and I’m not sure what those policies really do… but anyway, all gonna be good if/when I reinstall…
I don’t know if this is really related to Linux, but still I’m gonna try here:
I deployed the linuxserver.io Nextcloud image because it’s a bit less hassle than the vanilla one when it comes to setup.
But there’s something that’s bothering me: I can’t see in the Docker logs everything that’s going on in the container such as successful log in, access to linked files and all sorts of stuff.
It’s not the Nextcloud logs, those work just fine and log as usual.
I’ve had a couple issues with this image and the guys that mantain it are not really answering me anymore on Discord so you’re my hope to get to the bottom of this. Thanks!
There might be an option in the docker container, like -e log_level=7 or something like that, to increase the log verbosity. Does the container offer a manual? Or the container that this is derived from? Also keep in mind I’m not a Docker guru, I’ve only used like 2 or 3 docker images.
I don’t like throwing people under the bus, but the linuxserver io images are not documented at all. I’ve been on their Discord and they finally got back to me about the logs. Well made, but you gotta pressure them to get some infos.
They’re in a weird folder and are not exposed to Docker. They’re the access logs that are substituted with the s6 init logs they use to initialize the various parts of their image.
I’m always curious about such scenarios… if they use s6 or other inits inside an OCI container, then why make it OCI and not LXC… it bamboozles me.
IIRC you need to install gnome-tweaks. Normally the settings should have speed/acceleration but I’ve seen for some devices it won’t (or it has more than one for the same device wth!?) Normally gnome-tweaks will have the needed bits but the fact you have to install that separately is insane. gnome is a kitchen sink DE and IMO should have all this stuff all the time presented to the user. Even with all the extras it’s pales in “overwhelming” compared to KDE heh.
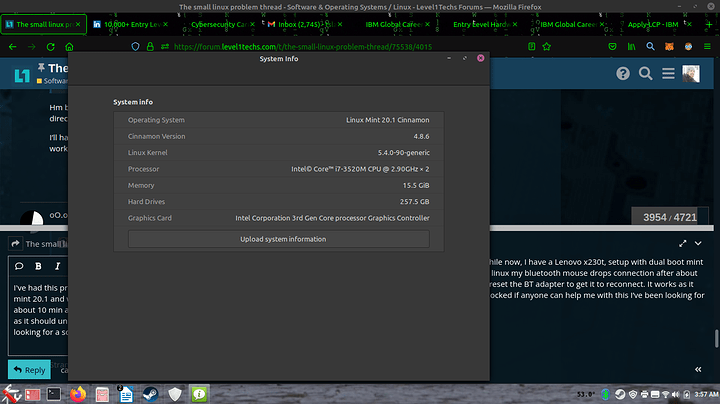
I’ve had this problem for quite a while now, I have a Lenovo x230t, setup with dual boot mint 20.1 and win 10. Problem is under linux my bluetooth mouse drops connection after about 10 min and then I need to disable reset the BT adapter to get it to reconnect. It works as it should under windows. I will be shocked if anyone can help me with this I’ve been looking for a solution for over a year now.
If the following helps then your USB BT adapter is going to sleep to save energy and not waking up properly:
sudo modprobe usbcore autosuspend=-1- unplug and replug your USB BT adapter
(The effect of the command persists until you reboot your machine.)
If it helps, and you wish to make it permanent, you can add usbcore.autosuspend=-1 to the GRUB_CMDLINE_LINUX_DEFAULT line in /etc/default/grub.
Note that the above disables autosuspend on ALL USB ports/devices. If your BT adapter is the only thing connected, this may be fine. If you have other things connected, the added power draw may be undesirable on a laptop. (Keep in mind that things like built-in cameras — if you have one — are probably also USB devices.)
THE POINT of the above is merely to quickly and easily work out whether or not “USB Power Management” is the cause of the problem.
Hey guys,
what is best practise for NFS mount options on wsize and rsize and other tweaks nowadays? For my home network, no databases or so. What are you using?
it’s not a USB BT adapter it’s either on the MOBO or connected through mPCIe as part of the WiFi adapter and the Wifi never drops at the same time that the BT dose or at all for that matter. So there is really no way for me to plug/unplug my BT adapter. I just checked this is what my BT adapter looks like.
Thanks for the image.
That card (Foxconn 60Y3303) is implemented as a USB device:
https://www.thinkwiki.org/wiki/Bluetooth_Daughter_Card_(BDC-4)
So it is still subject to the same Power Management controls as devices you would physically plug into an external USB port.