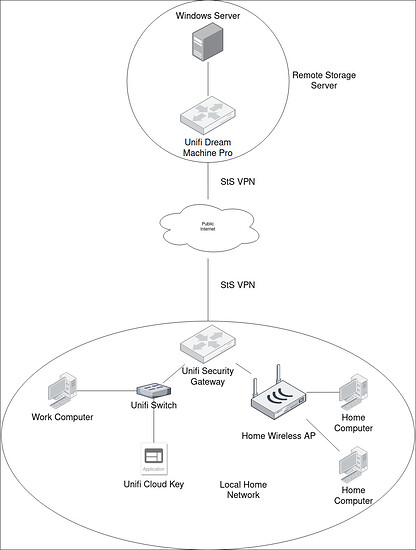
So I am trying to connect a home network in Washington with a network in North Dakota. The customer wants me to bridge them together with ubiquity network gear which I am unfamiliar with. Currently there is a Windows server hosting a vpn connection but he wants ubiquity to handle it so that it is separate. He has a dream machine in North Dakota and he sent me a cloud key, switch, and something else I don’t remember what it is off the top of my head. What is the path forward here? I spent a little bit of time trying to find some helpful documentation but I feel like I am beating my head against the wall. Anyone have some experience doing this?
Site-to-site vpn is probably where you want to start your research.
It should be achievable on the dream machine
So I guess the question is will the cloud key do that? I don’t really understand the ubiquity ecosystem that well.
The guy just bought a bunch of stuff and handed it to me with no instructions without consulting me beforehand so it is a little frustrating trying to figure out what the plan was here. And the Ubiquity stuff is not as “Plug and play” as they would have you believe in my experience with it so far.
I wouldn’t be able to answer that. Also i am not entirely sure why he gave it to you.
What does the cloud key even do?
Most Ubiquiti unifi network devices don’t host their own user configuration UI, and they don’t store long term statistics - instead they pull configuration and report state to “a controller” over http. Cloud key, is a small computer-on-a-dongle-ish device that’s just barely powerful enough to run a controller (e.g. a couple of arm cores and a bit of ram - controller is basically a java app using mongodb for storage).
Prior to the first version coming to market, folks used to buy raspberry pis to run a controller, or they’d run a controller somewhere on the internet and would then go through the process of “adopting” each new device to this controller (e.g. by ssh-ing with default password into the device and invoking set-inform script on the controller) . If your controller is on the same L2 network as your new device, adoption is easier, as the controller can discover new devices (or vice versa) than need to be configured, so there’s not even a need to ssh.
The controller then becomes the “single pane of glass” where you end up monitoring and managing all devices on your network. It’s super convenient for wifi where you have multiple access points and want them all to have the same wifi settings.
It’s not required to be permanently running for the network to run, but having some logs and graphs stored centrally is often useful (and that requires the controller to be running).
Could something else be a USG / Unifi Security Gateway - basically a router?
So it is a security gateway, a 4 port switch, and the cloud key. I have to go back to the site next week and I will be a little better informed now. So as I understand it the security gateway should do the site to site vpn and act as a router, then I connect it to the switch and the cloud key for it all to jive correctly?
I will just put the home router in AP mode and use the USG as the WAN connected router for everything. Then only route the UniFi switch traffic through the VPN.
Your diagram looks about right… work computer could be on one LAN that’d have access to work server over VPN, and the home stuff would be on another LAN that’s just going straight to through to the internet.
If you have the equipment with you, you can set everything up at your place and then just physically install it at the persons home?
Tom from @lawrencesystems maybe has something useful to you on their YouTube channel - there’s a bunch of folks making YouTube videos on how they set up Ubiquiti network stuff.
Also, maybe you and/or the person buying this stuff should look into tailscale and zerotier - it’s perfect when you have two computers that just need a secure network between them.
+1 for Lawrence systems, those guys helped me achieve an open Nat for my family’s Xbox One’s on our pfsense network
Yeah, I should have just taken it all with me. The biggest thing has just been trying to figure out how the UniFi stuff all works together and how to get it to integrate with his existing network. I feel like this whole process would have been easier if 1. He had brought me into the process beforehand and 2. If the entire setup was UniFi from top to bottom. Regardless I appreciate the help and I think I have a plan now on how to move forward.
If the home wireless network has UniFi wireless, he might be expecting you to power the home wireless AP from the unifi switch.
USG’s don’t have wifi built in, but the unifi switches often have PoE.
A lot of people get their toe in the door to UniFi becuase their home wifi coverage is crap and a U-AP Lite will cover the whole house by itself.
Just be mindful if this is the case, the diagram might change slightly to have the AP go into the switch.
I don’t recall if the USG can be powered by PoE, but this may be so - it supports input from 9-24v, and the supplied PSU is 12v. Sorry, I didn’t have time to dig through the datasheet!
Just for your info - I have been involved in previous employment where a firm has deployed these into employees homes to monitor what they’re doing on the Internet at home.
They give you content level filtering.
They don’t give you SSL decryption or anything, but if this becomes the default router on the network it can see and filter everything this employee is doing at home. And that their family are doing. Duty of care and all that.
USG doesn’t have a POE in, there’s various cheap gigabit + barrel jack 12V POE splitters if you wanted to save a power socket (I use “revotech” ones from Amazon to power my SBCs and other non-POE gear, but there’s other brands selling the same thing)
The wireless AP is just a netgear consumer router he has been using for his home wifi.
Some Netgears feature a VPN client.
Thanks, It’s been a while since I’ve touched one.
Went back today and spent 11hrs troubleshooting and provisioning the USG and Cloud Key then trying to get the StS vpn going. No dice on the vpn. Didn’t get home until 11pm and ended up very frustrated. I feel like I am missing something but after all the time and effort put in I am wanting to call it quits before I sink more into getting the UniFi stuff to work. Especially frustrating because it is supposed to be “simpler” than traditional networking gear but so far has been way more trouble than it’s worth.
Figured out at least part of the issue today. The ISP is a local cooperative Wi-Fi and the customer is behind a router or NAT that is causing the ubiquity USG to have all sorts of problems because it doesn’t have a public IP address.
Not even IPv6?
Tailscale at least uses STUN and ICE, it’s using wireguard underneath.
You might want to try that on your site and ask the customer to install the other end, regardless of USG L2TP stuff.