Doing this
My instructions dont really differ to much from building from source? I guess I should ask for clarification on what you need?
https://wiki.lineageos.org/devices/crosshatch/build
Its the only way to actually sign the ROM and make it into a factory image
Hacking there script up to work with the lineage OS Build
However you can just build it and skip signing and relocking the BL. thats the easiest route and honestly just fine
Well I have found the staged Pixel 4a device tree here and the proposed wiki entry on their gerrit so that’s good for the general build. Your comments on relocking the BL and using the Titan M chip for that is what caught my eye most.
Its a very difficult procedure and is tailored on a device per device basis my crosshatch wont work for your sunfish. However I can give you a brief idea of what you need to do
Ill adapt slightly from my process and the build docs. To generate keys for sunfish you should follow a similar process:
mkdir -p keys/codename
cd keys/crosshatch
../../development/tools/make_key releasekey '/CN=LineageOS/'
../../development/tools/make_key platform '/CN=LineageOS/'
../../development/tools/make_key shared '/CN=LineageOS/'
../../development/tools/make_key media '/CN=LineageOS/'
../../development/tools/make_key networkstack '/CN=LineageOS/'
openssl ecparam -name secp384r1 | openssl pkcs8 -topk8 -scrypt -out avb.pem
../../external/avb/avbtool extract_public_key --key avb.pem --output avb_pkmd.bin
cd ../..
See I use EC keys because its supported on the Titan M and WAY more efficient on ARM but I dont know what phone to phone changes google has made you know? Its why Im hesitant to be exact but I hope this helps
signify -G -n -p keys/crosshatch/factory.pub -s keys/crosshatch/factory.sec
Of course I take the scripts from graphene and encrypt the keys. You can also make your own and automate the process
script/encrypt_keys.sh keys/crosshatch
Then follow the rest of the guide to turn the lineageOS image into a factory image. This is a step devs dont take on lineage because its hard enough to develop as it is
When i took this route I updated once every few months. The build takes a while an a serious amount of RAM. (24 GB in my case).
It will just swap out but that slows it down further.
Genning deltas is important too.
Also you have to commit to Signed root which means no android pay and stuff. Things that worked under magisk wont. You have to accept this trade off.
But yeah my process was similar to this. I hope it sheds light how much you kind of have to do your own foot work to get it working on a device per device basis. Every device has an ARM trusted zone. If you can figure it out for a one plus I think there is a bounty for that on XDA. I dont have the time for one plus. LOL
@SgtAwesomesauce only slightly relevant to you since I mentioned signing builds you make. See convo history. You might be able to figure it out for the OP7 if you deem it worth your time.
Disclaimer. This was my own hack. I dont provide support LOL YMMV
but building on the knowledge is welcome 
hell yeah series 6 is out.
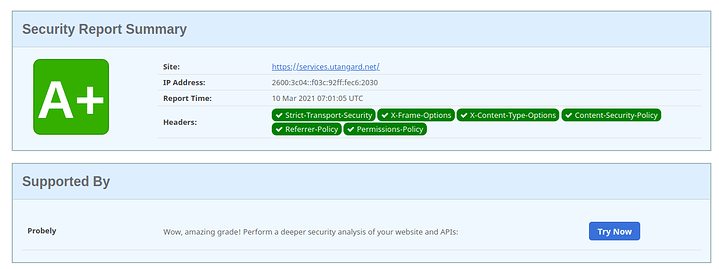
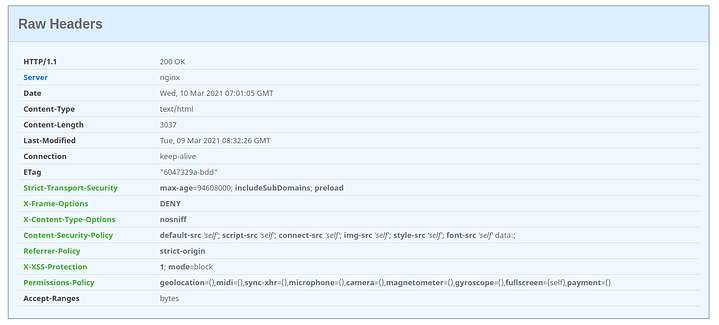
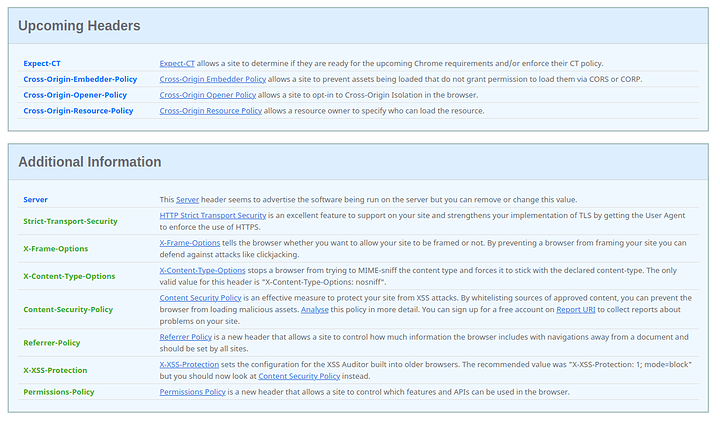
Security headers… Set them!
Links to Infrastructure Series and Blogs"
Blog: Phaselockedloopable- PLL's continued exploration of networking, self-hosting and decoupling from big tech
Series 1: Infrastructure Series -- Native Dual Stack IP4+IP6
Series 2: Infrastructure Series -- Wireguard Site to Site Tunnel
Series 3: Infrastructure Series -- Recursive DNS and Adblocking DNS over TLS w/NGINX
Series 4: Infrastructure Series -- NGINX Reverse Proxy and Hardening SSL
Series 5: Infrastructure Series -- Taking DNS One Step Further - Full DNS Server infrastructure
Series 6: Infrastructure Series -- HTTP(S) Security Headers! You should use them! [NGINX]
I made a simple landing page. No JS no fancy stuff. Might delete at some point
I love simple websites. What has ever been wrong with just static content. JS is critically overrated 
On another note though, your background image is 14MB, and the response contained no cache headers… Might want to compress the image, and add HTTP caching headers?
Js is bloat
Makes his own with a 14mb background image
Nice
ROFL… I had to make up for it somewhere. Gotta smack them data caps
Its mostly a troll … ill change it … when I get a good image. Problem is thats most of my images. hell my phone cameras images are like 16 on JPG… lol… so Im just at the point where I guess im desensitized to that
O’Reilly publishes a book called “Javascript: The good parts”.
It contains 176 pages.
At least the book isn’t bloated. 
You can compress images to be much smaller with very little noticeable loss of quality.
Yeah, and most of the front end task runners like gulp and grunt have plugins which do it automatically while watching for changes.
Let’s base our build process on javascript also! 
I am going to be so lost doing this, but I have my resources and google to help me…LOL If I get 4 or 5 references deep and lose my place I may raise my hand and ask for help.
I would like to get away from big tech and also harden the home network. More for fun rather than paranoia (its not paranoia if they ARE watching you) lol. I also want to learn about these processes. I’m fairly well versed in VM creation and operation. Instead of having different hardware I may attempt this virtually.
I also have another issue of the infrastructure of my network I think will effect how I do this. I have 3 Wifi nodes. ASUS RT-AX92U wifi 6 router/nodes for a mesh network. This means some devices are not hardwired to eachother. One that acts as my router which has a number of features I need to investigate along this guide to see if I can implement them such as https for the home network. I have to see if VLANs passthrough this device or not. I also have 2 managed cisco switches I can use for VLAN’s I may attempt to use.
I also need to learn network adapter teaming and see if I can activate that on my router/nodes because I believe it is a feature for my LAN. Then activate it on both the Ryzen server (MAIN) and the test server Dell Poweredge T420. Once this is better understood, and working I will attempt a 10G network with my servers through my switch.
So, thank you so much for all of this documentation for reference and as a guide for people to review.
if you scroll up wendell mentions 2.5G or 5G ethernet being a cheaper endeavor if you dont want to go full 10GBE…
My upgrade a decade from now will probably be 40 GBE and wifi standard at the time hopefully an open board somewhere like I have.
I stuck with all open source at first for a meme but it became a thing and actually way nicer than I thought
Thank you for this. I currently have a Cisco SG500X-24 24-Port GB with 4-Port 10-GB Stackable Managed Switch - Cisco I picked up for cheap. (Discovered a faulty fan connector throwing codes do rigged it in true @GigaBusterEXE fashion with external USB fans. I’ll post pictures sometime. It has 4 SPF+ 10G ports. I’m sure I can find something reasonable to use. I only plan to connect my two servers and possibly a gaming PC for game downloads from a steam cache I hope to create.
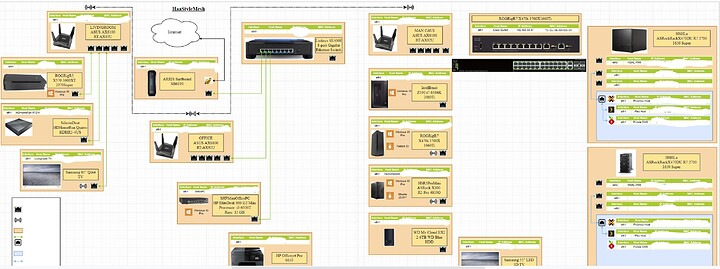
Here is a general map of the network.
Alot of that needs to be updated. This is a work in progress because i want to switch from the default net structure once I learn more about how to do it properly.
I guess my big question is should I plan on a firewall device pre my first ASUS RT-AX6100 RT-AX92U Router OR can I route traffic through one of my other servers to protect it? Also, The Pi services IE Pi-hole and OpenSense, can they be ran on a server as well? Can I use the managed servers in some way to help secure the network? I dont think WRT will work on my nodes/router… can I use any of my other devices to make up for this functionality? Virtualize it?
I attempted to look up the RT-AX92U and I cant find if it is able to passthrough VLAN tags and traffic if that’s another way I can secure the network traffic.
I know these are very general questions and I may not be using the correct terminology, but I am just planning at this point and LEARNING. I am still doing a lot of reading.
I appreciate the amazing write-ups again, and I’m still planning. I’ll attempt some more education before I attempt too much to try to ask more educated questions. Sorry to waste your time.
Not wasting my time at all. I’m just mobile and in the mountains so my answers are limited to my phone and how much I can write texting lol.
So this depends on how complicated you want to get. There are devices called trunk firewalls where you dedicate a port on your switch to trunkating all data up and down that way for your firewall or you may place it inline
Here is the key, you do not want your routers/mesh doing ANY network address translation or NATing. Does that make sense?
You want the firewall device to handle all the routing, NAT etc. Making the APs just dumb mesh APs
If that makes sense to you. Otherwise tell me where I lost you.
Makes sense. I just wonder how much horse powers needed… also the network structure is FAR from ideal as I have to use 3 wifi aps because my wife won’t let me run ethernet cables in the walls. I have a image of it some where… yeah it’s in a above post. That’s a general outline… I will be adding in 10G in the office between 2 servers and a pc.
Just wanted to see how you feel about this wifi/mesh node. Its what I use as a router/node throughout my house (I have 3). I chose it because it was wifi-6 and uses that as the backhaul band to connect the AP’s because I do not have hardline ethernet through the house.