@SgtAwesomesauce Its all hear. Commence AI
odin:~ # zpool status
pool: OnePoint21GigaWatts
state: ONLINE
config:
NAME STATE READ WRITE CKSUM
OnePoint21GigaWatts ONLINE 0 0 0
raidz2-0 ONLINE 0 0 0
sdb ONLINE 0 0 0
sdc ONLINE 0 0 0
sdd ONLINE 0 0 0
sde ONLINE 0 0 0
sdf ONLINE 0 0 0
sdg ONLINE 0 0 0
errors: No known data errors
odin:~ # zfs list
NAME USED AVAIL REFER MOUNTPOINT
OnePoint21GigaWatts 464K 14.1T 44.0K /mnt/OnePoint21GigaWatts
OnePoint21GigaWatts/encrypted 42.0K 2.00T 42.0K /mnt/OnePoint21GigaWatts/encrypted
OnePoint21GigaWatts/media 42.0K 4.00T 42.0K /mnt/OnePoint21GigaWatts/media
OnePoint21GigaWatts/nextcloud 42.0K 8.00T 42.0K /mnt/OnePoint21GigaWatts/nextcloud
odin:~ # zfs get all OnePoint21GigaWatts | grep compress
OnePoint21GigaWatts compressratio 1.00x -
OnePoint21GigaWatts compression zstd local
OnePoint21GigaWatts refcompressratio 1.00x -
odin:~ #
I fuckin love ZFS… heck yeah on the fly ztsd any day
odin:~ # zfs get all OnePoint21GigaWatts | grep checksum
OnePoint21GigaWatts checksum sha512 local
odin:~ #
@SgtAwesomesauce this filesystem is awesome
What do you use to tell drives apart? Do you have them in drive trays with LED indicators, or label the SATA cables, or … ? So like if your ZFS finds errors on one you know which one to replace?
Lol the sata port tag. Drive 1 is at the bottom. Drive 6 is at the top
Slowly I will have all my information coming out as small wiki posts. LOL
BLOCK YOUTUBE ADS
So blocking ads via the manifests alternative lookups is not too bad, Can confirm it works though
#➤ [documents] nslookup manifest.googlevideo.com
Server: 10.31.82.3
Address: 10.31.82.3#53
Non-authoritative answer:
Name: manifest.googlevideo.com
Address: 172.217.12.14
Name: manifest.googlevideo.com
Address: 2607:f8b0:400f:801::200e
#➤ [documents]
pi-hole hosts
[eric@baldr ~]$ sudo cat /etc/hosts
[sudo] password for eric:
# Static table lookup for hostnames.
# See hosts(5) for details.
172.217.1.14 manifest.googlevideo.com
2607:f8b0:400f:801::200e manifest.googlevideo.com
[eric@baldr ~]$
No more ads
According to reddit this is your process. It definitely works
Extend it further. Create your own list
echo "" > youtube-domains.txt
echo "" > youtube-filtered.txt
echo "" > youtube-ads.txt
curl "https://api.hackertarget.com/hostsearch/?q=googlevideo.com" > youtube-domains.txt
cat youtube-domains.txt | cut -d, -f1 > youtube-filtered.txt
sed '1d' youtube-filtered.txt > youtube-ads.txt
Just place that in the /srv/pihole folder
Map to localhost/nameofpiholeadstext.txt
Voila. Update gravity can pull it from itself
Cron tasked it to do this every night
I just want to preface to everyone that without the extensive help from @Novasty and @SgtAwesomesauce some of the more technical aspects of some of this would have taken me greatly longer
Credit is due where Credit is due 
Engaging translation matrix…
Translation: harass them if things go wrong.

I think something was lost in the translation /S  honestly some of those issues are dumb. I hate how things break in stupid ways.
honestly some of those issues are dumb. I hate how things break in stupid ways.
I also hate semicolons
You got a lotta hate buddy
Hey what can I say… I got alotta hate so im dishing it out, gotta give back some how /s
I filled the gaps in my journal I wont need much to keep it going and adapt from here but jesus christ does webshit break a lot. We are just desensitized to it
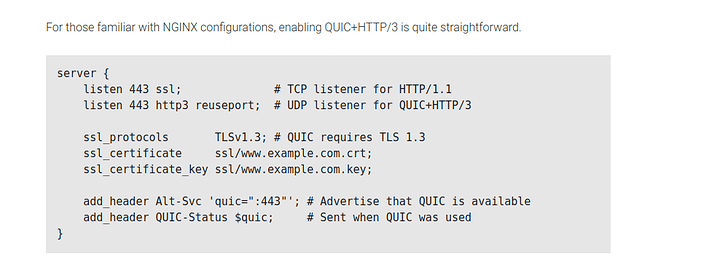
just wait until I implement this when nginx updates  since my nginx is always bleeding edge
since my nginx is always bleeding edge
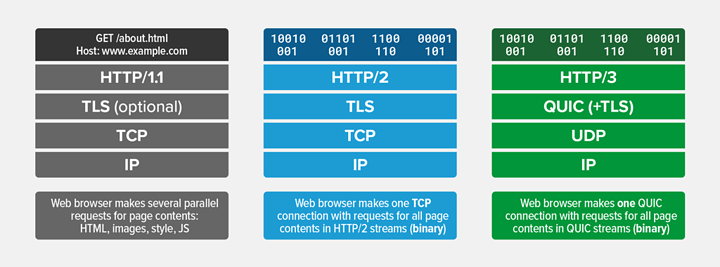
I actually cant believe we are going to see the downfall of TCP (soon ™ ). Everything is going to binary encapsulation.
holy shit dude we could all optionally turn it on without hurting our existing configuration
we just have to advertise its available on what we know would work with it. So chrome and mozilla and android browser can go brrrrr (sorry ios)
I guess you could also do add_header Alt-Svc ‘HTTP/2=":443"’; as well
Why didnt I know about this. I will experiment this weekend. I like having options available for all. No reason to stay on a downgraded protocol if the client can support a new one and no reason to break HTTP/1.1 either
I fucking love these russian devs. The one thing the motherland did right other than wodka
Forgot to add this to the blog directory here:
Infrastructure Series -- Recursive DNS and Adblocking DoT w/NGINX
Yet another drop from my journal
I really am just making it electronic
Series 4: Infrastructure Series -- NGINX Reverse Proxy and Hardening SSL
A good amount of hardening and round robin multiple nginx load balancing can do pretty well
Checkout the rate limitng you can do. That and having a load balancer makes this more effective.
Im doing this now. Im also adding a second droplet for round robin load balancing and both will be optimized according to the docs for high loads
It makes taking it down harder. I dont need CF for that
error_log /var/log/nginx/$confName$port.log info;
That can really help store data you need to detect it too!
See my thread: (its long. Also go to the second post for my updated config) that might answer your questions
Infrastructure Series -- Recursive DNS and Adblocking DoT w/NGINX
Infrastructure Series -- Recursive DNS and Adblocking DoT w/NGINX - #16 by PhaseLockedLoop
I havent updated it for my DoH and DoT changes yet. The pihole setup is a simple filter. The unbound does all of the work. Ive also setup auth zones and hardened the DNSSEC of the unbound. I disabled DNSSEC on the pi to the unbound because there is no point since its local.
Use unbound + DNSSEC not pihole to unbound with DNSSEC. The lookup only matters on the unbound
My network itself is totally open I have a blog post lol: Phaselockedloopable- PLL's continued exploration of networking, self-hosting and decoupling from big tech
It is worrisome but thats the realization of an open source backend. Chromium can be forked and degoogled by anyone and its a better engine. FAR better code
Failure in leadership on the project tbch
Its fine thats why ive moved this discussion to my blog. LOL. See the top of this post