Adventures in the New Network…and OPNsense.
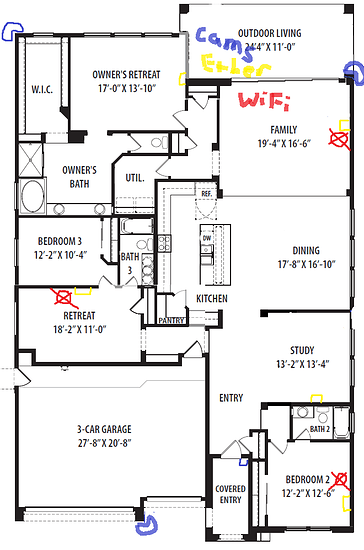
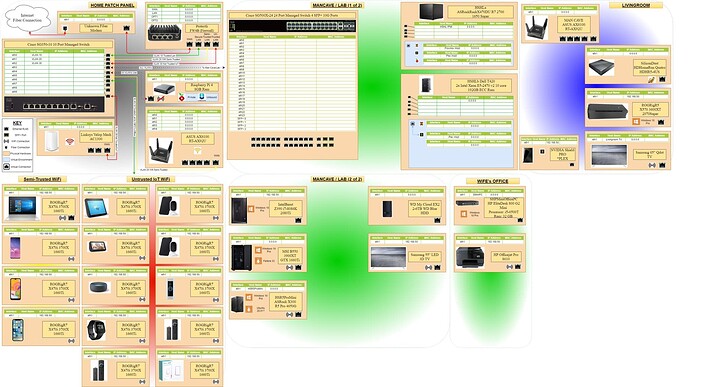
Heres the new network…SO far…
And here’s the office so far. 
I had a ton of help from @ThatGuyB and @PhaseLockedLoop on this one along with a few online sources.
So far I have implemented the firewall successfully. I was banging my head against the wall for a bit because I was being TOO detailed in assigning Static IP’s and information while defining my network via OPNsense.
IE- When setting up a static IP I would also add in the DNS address, Network Name and all kinds of info…this led to problems when I tried to set up DNSmasq to use the firewall as the route for all DNS requests to my pihole device…I lost all internet access also because I never set up the access all rule to allow my devices to connect to the internet on the second network that was not set up automatically… I had DNS errors all over and it was a mess.
The key points that saved me-
1.) Make sure you have the basic rules in place to allow all networks to communicate with each other and the internet on ALL networks (I was setting up 3 and only one was really “configured”)
2.) set up your rules BEFORE you decide to start handing out Static IP’s OR just set the IP and not all the other options till you have it set up how you want (except maybe with DNS NTP etc.
3.) The device I attempted to use to test my rules allowing cross traffic between networks to different devices was a WD Mycloud EX (not the 2 version which is still supported by WD fyi) . Come to find out as a security feature the OS itself does NOT allow that by default UNLESS you activate “Cloud Access” which I can not enable because it is no longer supported with security updates from WD.
The parts that messed me up…
Using rules to allow DNS access on ports 53 and 853 between networks while trying to use a wrongly configured dnsmasq that weren’t connected to the internet vs default rule and static ips with ips for DNS assigned.
Trying to connect to a device that WOULDNT allow the connection!
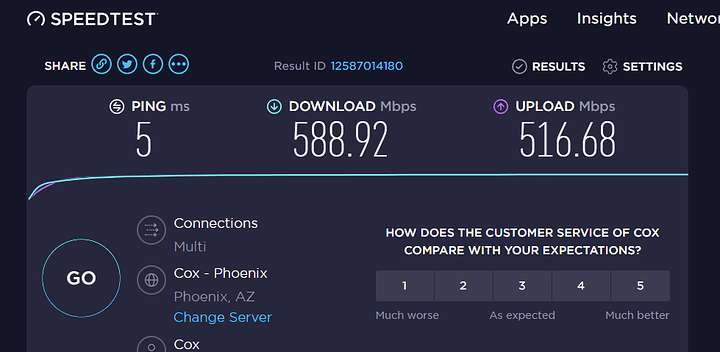
Now that I’m past these few issues it’s been working quite well…
Other interesting facts about firewalls that’s useful setting up rules-
-Invert is a useful option to save on two rules in one… IE block such and such to Inverted destination block all traffic to everywhere BUT the destination. Kinda cool or can be used for source as well. (Thanks @ThatGuyB!!!)
-If it’s a network you need, keep backups of working settings and revert as needed (IE-I used it to make sure the wife had her Plex DVR and Phone access to FB, Pintrest and Instagram)
-ASUS RT-AX92U works great as a wifi 6 AP for wifi, sadly when put in “Mesh” mode without a wired backhaul the wifi 6 band is used for wireless backhaul and not available for device use for connectivity.
-I had more but brain fart I’ll as more as it comes to me…
References- Easy to follow Small Secure (dual-stack) Network Firewall and Infrastructure Series -- Recursive DNS and Adblocking DNS over TLS w/NGINX - #60 by PhaseLockedLoop and Recursive DNS With AD-Blocking Features - Part 1 | Nerd For Tech and https://homenetworkguy.com/
Hope its ok to do external links… 
To do: Need to learn to set up port mode on my Cisco router, and use firewall to create VLAN’s to assign that traffic to ports on the switch. This isnt really needed because I have two mesh networks I can set up with hardware I have ASUS RT-AX92U and a Linksys Mesh system for IoT.
 .
.