Well its because in the pf model its put after the prerouting so it adds loading like crazy. But it wont realistically be a bottleneck till later. Its also just bad practice because its a bit less secure than other targeted rules.
So talking to a networking scrub. how would you do it?
I would take bikky’s swiss army approach.
Assign the device mac’s to a given pool of addresses.
Route that pool as exclusion from the tunnel on LAN and leave floating+WAN rules alone. Thats me. I am not drafting up the specific rule set right now because I am not in the position to do so. Do you understand the concept?
Maybe…
So a ton of networking isn’t the simple asking people on a forum to get easy reply answer I can put in the box type problem. I do not want that to discourage you; instead, it should invigorate you to learn. The way we can do this more systematically is by mapping. Map the idea and concept out. Mapping means listing what you know and do not and figuring out what you need to know to achieve the concept.
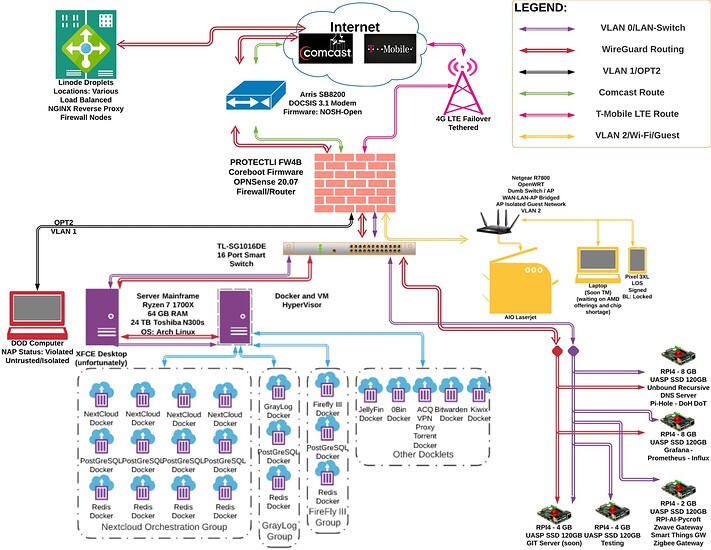
So if you map your network like you have seen on my threads and make an exploration thread or attached thread so people may refer back to it. This additional information would yield more tailored helpful results.
(mines not up to date)
Map Idea above
Also @HaaStyleCat has done some. Check out his threads. He did ones that were far better than mine
See his thread too. These are ongoing processes.
Any ideas how i would do this with a vlan?
A vlan is a “virtual lan” and it’s a layer 2 concept (switching). If your switch has vlan support, you can configure a subnet (layer 3) for each vlan.
So, instead of having 1 subnet per router and switch ports, you can have multiple subnets on 1 switch and 1 router port. Imagine vlans as having another router port and another switch attached to it, but it’s virtual, happening on an already existing port.
Your switch has to support vlans, so after you look for your switch model and “vlan support” we can continue with that. Layer 2 is not that hard.
I probably shouldn’t throw out the layer 2 / 3 concepts at this point, just to avoid a bit of confusion, it’s not a lot of information, but it’s a bit hard to digest. For short though, IP packets get encapsulated in Ethernet frames (another packet basically, kind of like a box in a bigger box) and the Ethernet stuff talks locally using MAC addresses. So computer aa:aa:aa:bb:bb:bb will send the frame to router bb:bb:bb:cc:cc:cc. The router decapsulates the frame, reads the IP source and destination, looks at the routing table to see where it should send the packet next, re-encapsulated the IP packet into a new frame and sends it from MAC address (of the egress / outgoing port) bb:bb:bb:cc:cc:dd to another router (or straight to the target computer if it’s on the subnet on the other router port) with MAC address dd:dd:dd:ee:ee:ee.
When you connect 2 PCs via one Ethernet cable, this is called a broadcast domain. If you connect a PC to another PC via a switch, the broadcast domain expands to every switch port. A broadcast domain is stopped at the first (ingress / incoming) port of a router. VLANs encapsulate and restrict those broadcast domains, so the devices assigned to a VLAN can’t talk to another VLAN, even if they are on the same physical switch, unless they route traffic through the router and back to the other VLAN. Each VLAN has its own subnet.
Hope this was not too confusing. I tried to keep it short.
But, getting a bit muddy here, it is possible to have multiple subnets on a single switch / single vlan, just that you don’t get any security benefit for doing that. You can set 2 IP addresses on an interface and have certain MAC addresses get IPs from a certain subnet and the rest from another subnet, but even though it will be the same switch everything lies on, the different subnets will still have to go through the router, even though the hosts have the same broadcast (layer 2) domains. Yeah, I probably shouldn’t have mentioned this, but I took some time to write this, so I won’t let the comment go to waste. Ask for questions if anything is confusing and come back with the answer regarding vlan support on your switch.
How would I find out about my switch? Specifically the nic is an el cheapo one. a lenovo prebuilt from way back when with a rosewill nic for lan.
Just search you switch model and “vlan support” on any search engine. But it’s likely that if the switch doesn’t have a management IP address on it, it likely is not managed.
I don’t know if this hassle is worth it. I have spent the last three nights up till 4am researching this. On top of that i have been waking up at 8am. All I want is for my tv streaming devices to not be routed through the wireguard vpn. My basic asus router had something called vpn fusion where you could select by mac address if it went through wan (non vpn) or wan (vpn)
Here is my nic…
it does support vlan.
Yeah, best way in this case is to just ensure your devices always get the same IP address (DHCP static mapping) and adding them in a group in OPNSense and route the group straight through the WAN.
That’s just the router, Ii am assuming you are using the asus router as a switch, so that would make it basically a network behind another network. If you have NAT on your asus router, it probably won’t wok. If you don’t, or even better, if your asus router is in Bridge / AP mode, it will work.
Edit: your asus router likely doesn’t have vlan support though, the “work” was about the comment above this one with the dhcp mapping and grouping them in opnsense.
I have the asus router acting as a access point.
As PLL said, what’s the network map?
ISP → opnsense → asus router in AP mode and a couple of wired devices on the asus built-in switch?
ISP >>> opnsense >>> ASUS AP >>>> devices
that is it.
Alright, then forget about VLANs and adding other subnets, you only have 2 ports on opnsense, so 1 subnet to the ISP (WAN) and one subnet on the LAN.
Yep, the only way to avoid your streaming devices to go through your WG tunnel is to route them straight to the WAN. I believe you solved this earlier using floating rules. As long as that works, you should be good to go at this point.
Probably not worth expanding your network to have multiple subnets and vlans at this point in time. Maybe later if you want the added control that you get with splitting your subnets based on their use case (as mentioned above, local services, wifi, guest network, streaming devices, iot subnet etc.). For now, only 1 subnet works for you, you just need to make an exception from certain devices to not go through the WG tunnel, which you already did.
The best part is that, if you add another device to the network that is doing heavy streaming and you don’t want it to go through the VPN, all you’d have to do is add it to the group and you’re gold.
Edit: by expanding the network, I mean adding a managed switch between opnsense and the asus router. That’s when vlans get useful, but you also need different APs for different vlans if you want to use wifi, unless your router supports running multiple SSIDs for each subnet, which is another can of worms I won’t get into. Keeping the network small for now is probably a good idea.
Would it explain all the crashes i was having with my vpn? Whenever I visit l1t site i was getting vpn crashes last night. The Floating rule?
Unlikely. But unlike OpenVPN for me, which crashes once in a month or two, my wireguard on my phone seems to, not necessarily crash, but to need to get reconnected once in a while. I believe this is because I didn’t activate keepalive, to save on battery. Do you have keepalive set on your opnsense wireguard client? set it to 25 seconds if you don’t, it should be fine afterwards (I think).