In our company we get tested from time to time for phishing attacks and we are well versed in spotting the fakes. Most of the time over 90% of people have no problems passing.
Few days ago, however, almost everyone fails the test, and I believe poor design by Microsoft is to blame.
So here is the setup:
Our company has a domain name example.com and emails are formatted as [email protected], standard stuff so far.
The attacker (the guys who test) go ahead and register example.co for 5$ (dot co, not com) and they sign up for a month of Proton Mail premium at 6$. This subscription allows for custom domains, so they setup DNS, SPF, DKIM, and all the other goodies to make the addresses as legit as possible.
Next up they make a fake email [email protected] and prep a phishing message, some dumb PDF looking image linking to URL shortener with the idea of users thinking “oh, the CEO is sending us a Holiday greeting in a PDF, I’m going to click it”, but instead of a Holiday card they get a drive-by download.
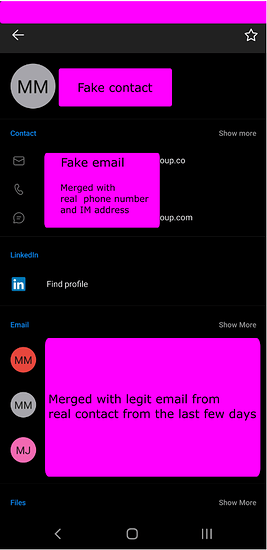
The trouble is, Outlook (web version, desktop, Android, and maybe others) is trying to be helpful and it treats the two addresses as the same contact by default. The fake address [email protected] is auto merged with the legit CEOs address [email protected].
On mobile it is literally identical to the real thing unless you go 3 levels deep to check out the contact itself, and even then, it is very convincing as Outlook just assumes that the fake email belongs to the real CEO. It is a clustefuck, I know - see the screenshot.
We concluded that Outlook is literally facilitating spear phishing by auto spoofing similar looking addresses. We reported this behavior to Outlook team and trough Microsoft vulnerability thingy, and received the “you can go fuck yourself, here is a link to learn how not to get phished” answer.
Are we the crazy people here?