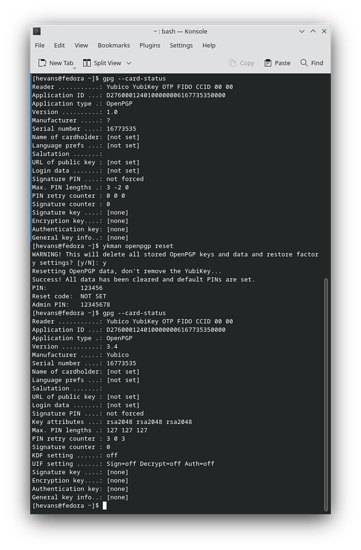
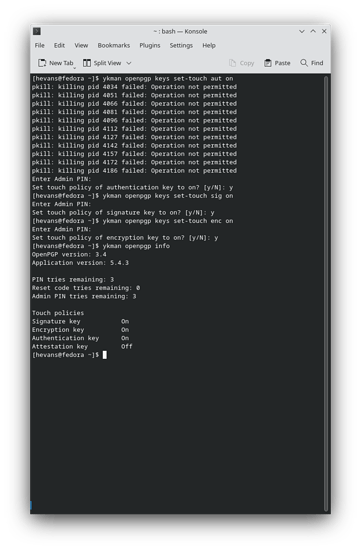
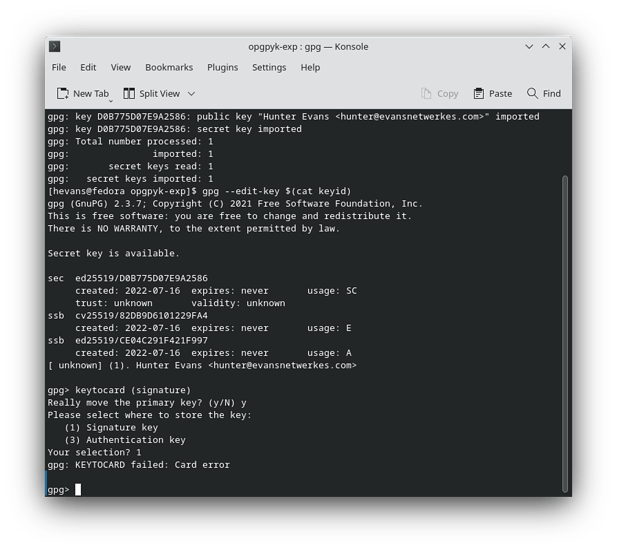
We can also try to reset the openpgp storage area on the card
ykman openpgp reset
If that doesn’t work the manual directions are as follows
Insert the YubiKey into a USB port.
Open Command Prompt (Windows Users) or Terminal (Mac / Linux).
To check the PIN/Admin PIN reset status, enter the GPG command: gpg --card-status. If you receive the response “gpg --card-status” fails, terminate gpg-agent and gpg-connect-agent processes, then try again, or you can reboot.
Run gpg-connect-agent --hex
If PIN retry counter from step 2 is greater than 0, enter the command: scd apdu 00 20 00 81 08 40 40 40 40 40 40 40 40
Repeat the above command until one of the following occurs:
YubiKey 4/5 Series device reports “D[0000] 69 83”
If Admin PIN retry counter is greater than 0, enter the GPG command: scd apdu 00 20 00 83 08 40 40 40 40 40 40 40 40
Repeat the above command until one of the following occurs:
YubiKey 4/5 Series device reports “D[0000] 69 83”
To terminate card, run the GPG command: scd apdu 00 e6 00 00
You should see “D[0000] 90 00” (if already terminated, you should receive “D[0000] 69 85”).
To reactive card, run the GPG command: scd apdu 00 44 00 00
You should see “D[0000] 90 00” (if card hasn’t been terminated, you should receive “D[0000] 69 85”).
Close or exit the command prompt or terminal window, and then remove and re-inser the YubiKey device.
Terminate gpg-agent and gpg-connect-agent processes (or restart), then run the GPG command: gpg --card-status
Confirm the PIN Retry counter is as follows:
“3 0 3” on a a YubiKey 4/5 Series device
Once we are in that spot kill the gpg agents again or reboot and unplug/replug the key and you should be able to write to this again