Trying to figure out how to get my wireguard clients to talk over the ipsec tunnel I previously set up between my two pfsense firewalls. The firewalls themselves and everything on their LAN’s can talk over the IPSec tunnel, but wireguard clients can’t. Not sure how to add a “route” to pfsense to do that
Give the wireguard IPs different than the subnet used on LAN or the Site-to-Site tunnels.
The biggest question I have in all of this is why are you trying to wireguard through ipsec? Would it not be sufficient to just wireguard without it?
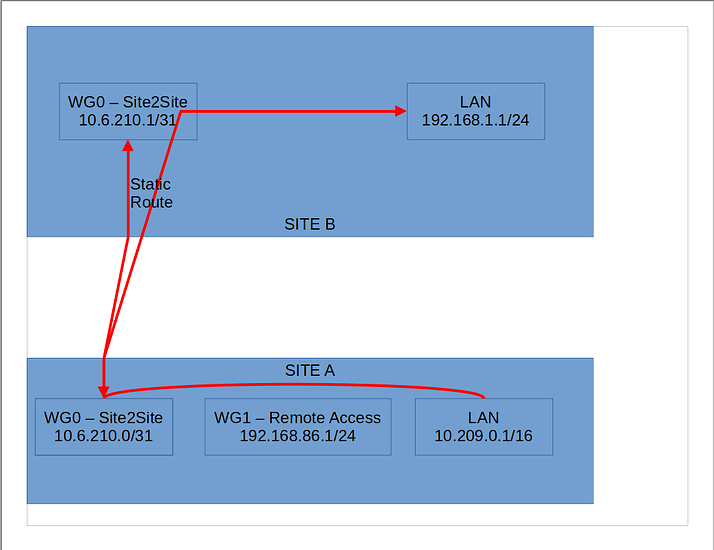
Wireguard is used for remote clients, like my laptop. It’s run off Site A
IPSec is the tunnel between the two firewalls
Site A LAN: 192.168.1.0/24
Site A IPSec IP: 10.6.6.1
Site B LAN: 10.209.0.0/16
Site B IPSec IP: 10.6.6.2
Wireguard Tunnel Network: 192.168.86.0/24
IPSec Tunnel Network: 10.6.6.0/31
Since Site A & B are already connected via IPSec, why not set up static routes in PFSense to direct 10.209.x.x traffic through the tunnel?
In a setup similar, I use Wireguard as the tunnel from Site A to Site B.
Site A LAN: 192.168.1.0/24
Site A Wireguard IP: 10.72.1.1
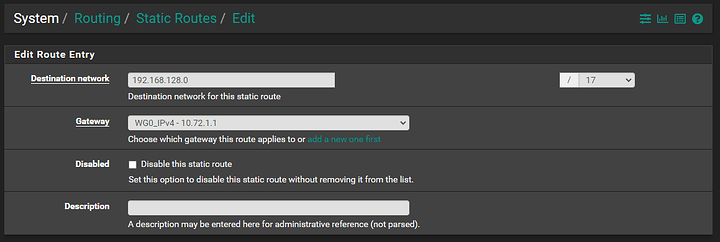
Site B LAN: 192.168.128.0/17
Site B Wireguard IP: 10.72.1.2
Since I need access to Site B LAN from Site A, in pfsense you can set up a static route to direct all traffic to that LAN through the tunnel so it reaches the destination:
Site B’s internet uplink is gigabit, Site A has absolutely abysmal upload speed which I want to avoid using if possible.
As it is RN the wireguard peer on site B isn’t working right so I’m using site A’s peer for now
ideally I’d want all traffic going through site B, but there’s a lot of it that i’d rather have only go out site a’s WAN
I realize I could do all this with wireguard tunnels but they’ve been less reliable for site to site in my experience
Point still stands, why not toss wireguard if you already have an IPsec connection ready to use.
I’ve tested it and wiregard just performs better than IPSec *for mobile clients
How would I set up a static route so that my wireguard peers on one wireguard interface can talk through the other one?
I can’t seem to figure out how to do this in pfsense
Before you setup a static route, is wireguard confirmee working?
yes wireguard is confirmed to be working well
The site to site works, devices on either side’s LAN can talk to each other, using the static route from the site to site gateway
however the wireguard remote access clients are restricted to only one site’s LAN
On the remote clients, add peering for both sites, you need to create two tunnels from one device.
Ignore up top.
Try setting the allowedips for remote clients to site B’s LAN
Something like
AllowedIPs = 10.209.0.0/16, 192.168.1.1/24, 192.168.86.1/24
Is that compatible with this?
AllowedIPs = 0.0.0.0/0
There’s no point in specifying more specific routes when 0.0.0.0/0 is present anyway.
I haven’t tested it, but it will probably just route everything over the tunnel.
ahh, since you’re routing everything, then what I said is pointless.
At this point I am unsure of why it isn’t working. I would probably start looking at the firewalls next to make sure you aren’t blocking traffic from one interface to another.
As far as I can tell there’s no firewall rules blocking traffic. Both wireguard interfaces have rules passing ALL traffic, I even added a floating rule between them and it still doesn’t work…
I even tried adding specific rules in the firewall to pass traffic explicitly between LAN/WG on site B and between s2s/remote on site a
I don’t know HOW to do this sort of routing in pfsense but I don’t think there’s anything stopping this from working…
ALL wireguard interfaces have ONLY ONE RULE and that is to pass all traffic. According to documentation, pfsense should be routing traffic between them, and yet it is not…
traceroute 192.168.1.1 ✔
traceroute to 192.168.1.1 (192.168.1.1), 30 hops max, 60 byte packets
1 192.168.86.1 (192.168.86.1) 7.531 ms 7.426 ms 7.357 ms
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 *^C
I may need to add a NAT rule but I don’t know what exactly it would need to work