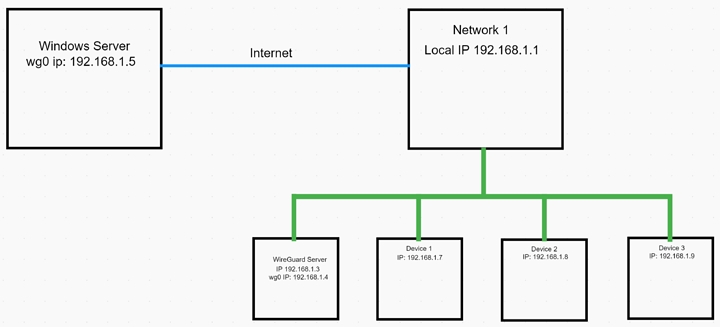
My company is setting up a frontend for an HVAC network. We have been given our own VLAN for our equipment, but the client does not want the web server on their network and will not allow any incoming connections. My boss has been working with there IT for a while trying to com up with a solution. I figured I would try to come up with my own solution to help out and if I got something working I would show him. So I started messing with wireguard. I set up a test network that mimics how the network will be set up.
I have wireguard set up on both the windows server and the wireguard server and I can ping both ways. I can also ping anything on network 1 from the windows server, but I can’t ping the windows server from any device on network 1. I need devices 1-3 to be able to talk to the windows server and vice versa. wireguard configs below any help would be appreciated.
Wireguard Server Config:
[Interface]
Address = 192.168.1.5/32
SaveConfig = true
PrivateKey = WG_SERVER_PRIVATE_KEY_GOES_HERE
[Peer]
PublicKey = WINDOWS_SERVER_PUBLIC_KEY_GOES_HERE
AllowedIPs = 192.168.1.4/32
Endpoint = 10.0.1.70:51820
PersistentKeepalive = 25
I also ran the following iptables commands on the wireguard server
iptables -A FORWARD -i wg0 -j ACCEPT
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
Windows Server Config:
[Interface]
PrivateKey = WINDOWS_SERVER_PRIVATE_KEY_GOES_HERE
ListenPort = 51820
Address = 192.168.1.4/32
DNS = 1.1.1.1
[Peer]
PublicKey = WG_SERVER_PUBLIC_KEY_GOES_HERE
AllowedIPs = 0.0.0.0/1, 128.0.0.0/1