Hi all, I’ve returned with more self-inflicted network problems…
I am happy with my network, but I would really like to be able to log into it when I’m out-and-about. Obviously this calls for some kind of public ip address, maybe some DDNS entries, and an OpenVPN configuration, but here’s the issue: My home network router is behind another router, and that router in turn is the one with the public IP address.
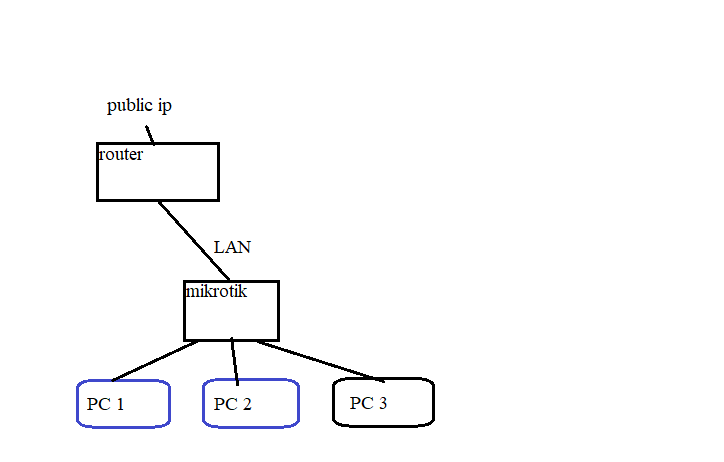
So here’s what I was thinking - the current topology is as shown below:
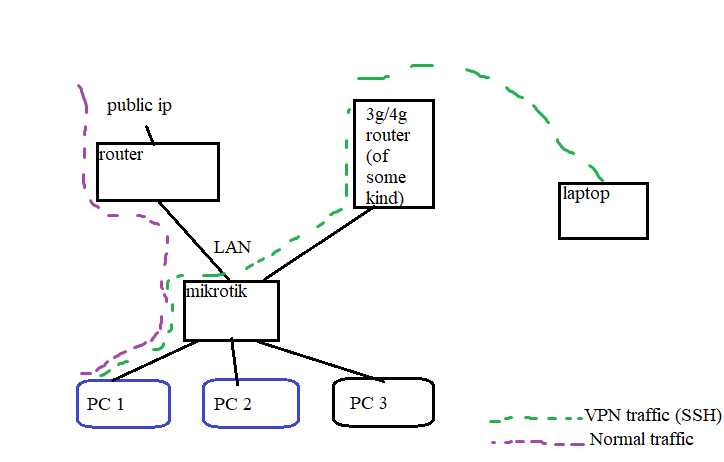
What if, I could add an ultra-cheap, ultra-lame 3g/4g dongle, exclusively for incoming VPN connections? I.e. when I am at my workstation physically, all traffic gets routed through the normal fast terrestrial connection, via the external router.
And if I am somewhere physically outside, I can create a VPN connection, open an SSH session, and obviously that will use up very little bandwidth - whatever is used by me typing characters, and receiving compilation failures via TTY. But while I’m SSH’d in, if I say do wget <whatever>, that wget will get routed as-usual via the fast terrestrial connection. Illustration (if it makes sense):
Anyone have any thoughts on such a setup? The only issue I can see is that these modem providers often NAT the dongle itself, so I’d be back to square one with regards to a public-addressable IP address for the VPN step. But otherwise, the only thing is finding a super-cheap solution, i’m talking probably 1GB/month type deal. if they cost the same as more expensive 3g/4g modems, i might aswell just get a “real” 3g/4g router, and use that as my upstream connection in general.