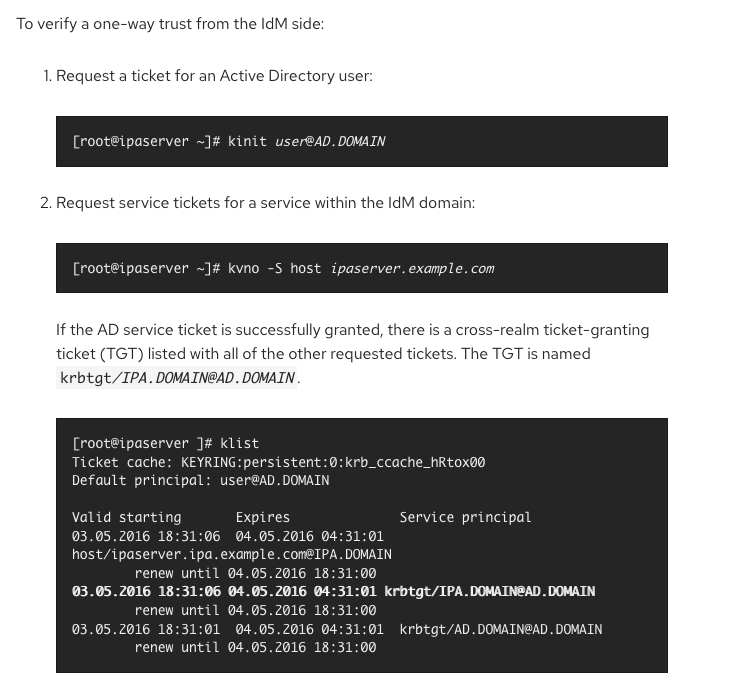
Yes, at the time it only supported syncing users if I remember right. I assume that’s not changed.
Yeah, I just want a one-way trust where IPA sees and trusts the AD users and I can give them privileges so I can have one login across both. IPA would essentially be slaved to the AD. I won’t make any users in IPA.
For me, the trust appears to work, and I can id an AD user on the IPA DC, but no AD users appear in the web interface, and I can’t do this (below), which according to the RHEL docs, is something I need to be able to do (kinit works, kvno fails).
Does cockpit manage docker on Ubuntu 18.04 or 19.10?
How is it with KVM VMs?
You should really boycott Chef. Ansible is objectively superior. 
A nice bsd persone on twitter told me this a years ago, and i discovered that using env for boot script wasn’t a good idea … when my system no-longer booted  . I’m pretty sure @SgtAwesomesauce know enough to avoid this, but for other, don’t go with a big “find and replace”, and think about the use-case before replacing the #!
. I’m pretty sure @SgtAwesomesauce know enough to avoid this, but for other, don’t go with a big “find and replace”, and think about the use-case before replacing the #!
I AM SO VERY SMRT
I locked myself out of a CentOS system by improperly editing the sssd.conf when i first set it up. Now this went unnoticed because how it was setup I could login just fine with my own username on the domain till recently my username was changed for some internal testing
I broke in by using the local administrator account, this was happening on our production helpdesk server.
Now if you are curious what was changed:
access_provider = ad
Was changed too
access_provider = simple
When I first set it up, I’ve changed it back to AD and all is good now.
Also for anyone curious as I’ve mentioned using cockpit in here in the past, I have this line saved at all times for when I set up a CentOS server to get cockpit up and running immediately.
sudo yum install -y cockpit cockpit-dashboard cockpit-storaged cockpit-pcp cockpit-packagekit setroubleshoot-server net-tools nano
So it installs all the tools needed to access the cockpit server which is https://localhost:9090, it makes managing SELinux a dream and simplifies in heavily as dealing with it is a huge pain in the ass.
I mainly use it for this. Work over ssh and have the selinux tab opened in a browser to see what’s being denied (in plain english).
On other note about cockpit. It expects admin users to be in the adm and systemd-journal groups, not just wheel.
Hmm… Adding that to my cockpit notes.
Well, that’s the oof of the week.
Actually using the yes command in a script. A first for me… 
This is something i need to see Oo
Onboarding an Edgerouter
OP=/opt/vyatta/bin/vyatta-op-cmd-wrapper
ROUTER_FIRM='https://dl.ui.com/firmwares/edgemax/v2.0.x/ER-e300.v2.0.6.5208554.tar'
RRUN="ssh -i ~/.ssh/${key} ${ADMIN_USER}@192.168.1.1"
${RRUN} "yes | ${OP} add system image ${ROUTER_FIRM}
${OP} reboot now"
huh I forgot about that when I needed it in a thing, ended up digging through docs for obscure environment variables…
Definitely beats writing an expect script for one yes/no prompt.
Damn what a brutal fucking last week. Set up an OpenVPN server, radius server for domain authentication. 2 new domain controllers for 1 ancient accounting server to keep working. A VMware cluster. And so much other shit.
Just to meet a November 15th network migration deadline. Not even close to ready.
Gone through a handle of whiskey this week
Been there. Good luck.
I think I need to re-do the compound
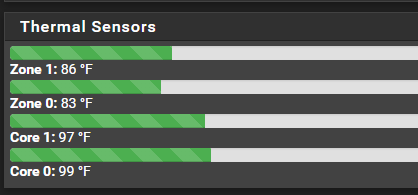
Are you thinking in Celsius?
Worse I derped and was thinking 4 cores but it’s two core.
Spent that past 2 nights configuring routers and switches until 4am but I hit a wall today. So brain dead.