Pics and More Information
Here is an architectural overview of the drone, from 3DR (the folks that made it).
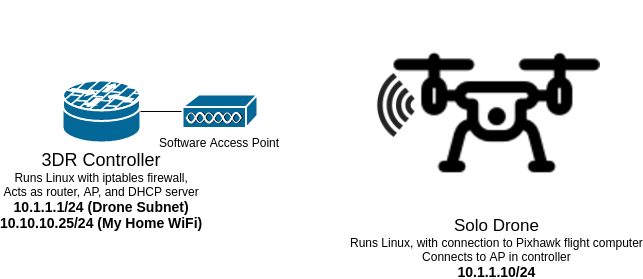
The drone and the controller both run 3DR’s customized version of Yocto Linux (don’t know much about embedded Linux stuff so sorry if I am butchering terms) and communicate over IP. The controller acts as an AP as well as a DHCP server, and the drone is the client (with a static DHCP reservation).
Traditionally, to use the app to view the video feed, or to adjust other parameters on the drone, you have to connect to the isolated wifi network between the controller and the drone (10.1.1.0/24). That’s a little inconvenient because it’s got no internet, so if you’re doing developer type stuff where you need Google you have to keep swapping networks unless you have a computer with two Wifi cards.
So the wifi card in the controller is capable of being both an AP and a client at the same time, making the Linux machine in the controller a simple router. This is really handy because it means you have internet while using the drone, but strikes me as dangerous from a security perspective. By default, when you set up this router feature, it doesn’t do NAT, it just routes. If it did NAT, it could be leveraged like a one-way valve, but since it just forwards traffic between the drone network and the main wifi network, it seems to be rather dangerous to me. The Solo and the controller both have a default root password, and while I could change that, it wouldn’t fix everything. The UDP port that talks to the Solo’s Pixhawk flight controller (using MAVLink protocol) has no authentication or security to my knowledge. So basically anyone with access to the drone at an IP level has a decent chance of being able to take control.
I want to use the controller (since it’s being a router anyway) to keep the drone network off limits to outside resources, while still allowing access to the internet from within the drone network. Since it’s Linux, it has iptables on it,so my initial thought was to use the stateful module and just deny any NEW connections into the drone network. That should effectively make the one-way check valve I’m going for. But I can’t do that (unless someone here is a ninja) because it seems it’s missing the module that adds the stateful features to iptables. Whenever I try that, it tells me there isn’t a chain with that name.
So I guess what I’m asking is…how do I secure this thing with a fairly primitive iptables install? Or is the only safe option to make another, separate wifi network (I have UBNT APs, so that is an option, but kind of an ugly one) and keep the drone on that, and then use pfSense to keep it safe? I could do that, but I’d rather have security at the last hop between the drone network and the proverbial wild west, if possible.
Pics
There’s not a whole lot of this security thing you can see in pics. On the outside it looks like a stock 3DR Solo, although it is running Open Solo instead of the outdated factory firmware. (For those that aren’t aware, the gist is 3DR made the drone, then made some bad business decisions and ended up going under, but when they went under they open sourced all the code, so it is still being maintained by members of the ArduPilot community).
And here is a rough diagram of the logical network behind all this: