Ok so I have a pair of Lely a4 milking robots, about 4 years old. Here’s a video if you want to see what they do https://www.youtube.com/watch?v=En5IQYw75mc
This thread is the story of how I persistently prodded the system until it (sort of) delivered the functionality I wanted, and a request to you, dear viewer, for any advise you might have on achieving the last 5%
When we bought these robots I was disappointed that it didn’t come with tools to let you do stuff remotely, like clear errors, reboot the robot etc. So naturally I installed Kali linux, plugged my laptop into the robot LAN, and fired up NMAP.
Starting Nmap 7.40 ( https://nmap.org ) at 2019-02-25 12:08
Eastern Standard Time
Nmap scan report for 10.4.1.102
Host is up (0.0019s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
5900/tcp open vnc
6000/tcp open X11
8080/tcp open http-proxy
MAC Address: 00:12:FF:01:A4:0C (Lely Industries N.V.)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 1 hop
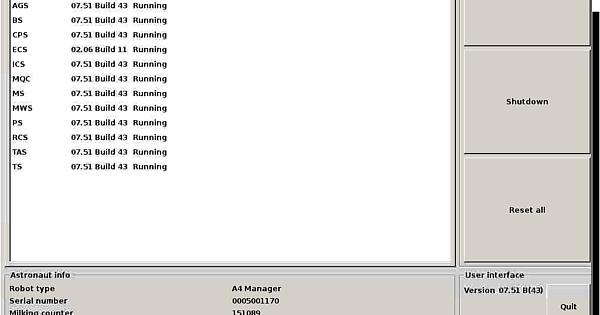
So this is interesting… It has a VNC port open. Fire up VNC:
Very nice! Unsecured VNC! It shows the same stuff as the touchscreen on the robot.
On the other hand. Bummer! It seems to be view only
 I can’t do stuff, just watch.
I can’t do stuff, just watch.
But what’s that? An open X11 port on 6000?
This is where I start to get out of my depth. I really don’t understand the X11 client/server model. Is it backwards, is it forwards? Do clients listen with open ports? Do servers display stuff on screens? I have no idea.
What I DO know is if i type:
export DISPLAY=10.4.1.102
xterm
Then the xterm window shows up on the robot screen 
So clearly this port 6000 is also unsecured!
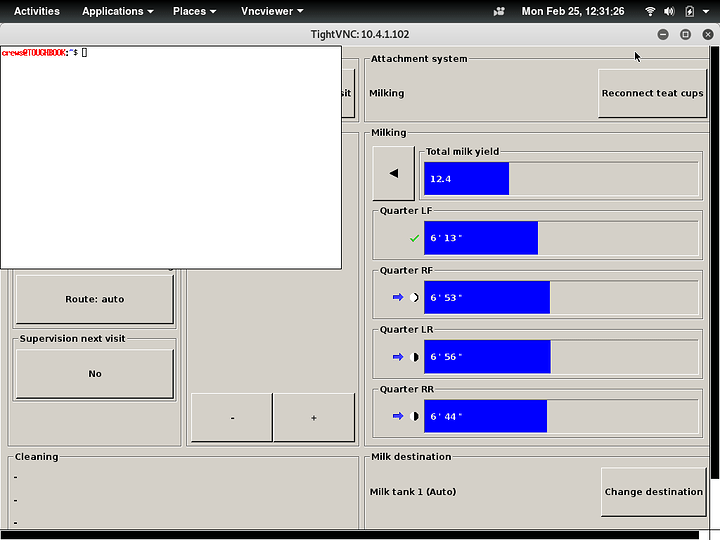
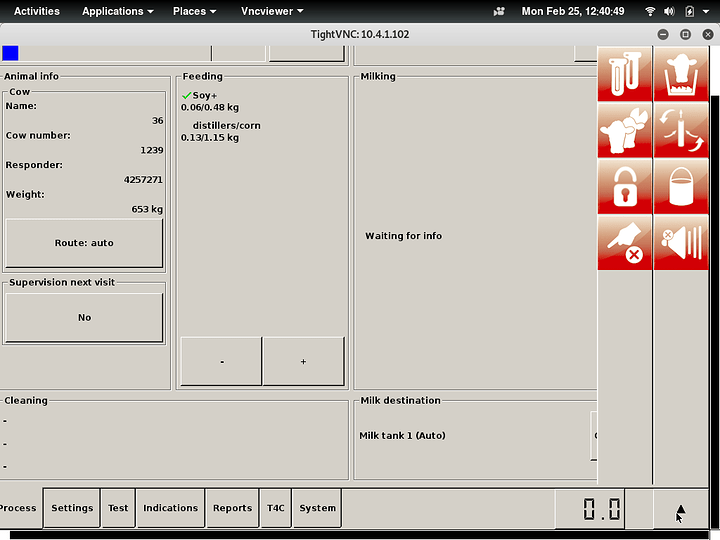
At this point I spent days trying to understand what was going on. I can capture the frames from the robot screen using xwd(which is pretty cool) and I eventually discovered a pretty neat utility called ‘xdotool’ which allows me to send keystrokes, mouse movement and mouse click over the network to port 6000. We’re in like Flynn! If I “xdotool click 1” while the mouse is over the button in the bottom right, the actions menu comes up, and I can initiate a cleaning cycle, put the robot into or out of operation, or divert that cow’s milk to a holding pail to be fed to calves (red buttons on the right)
If you’ve made it this far, thanks for reading! And if you know how X11 works please enlighten me as to how this functionality is possible, and if there is a slightly less ‘bodged’ way to do this.
Ideally what I’d like to do is ‘connnect to the x session’ if such a thing is possible. Exactly like how you would VNC into a machine. It kind of seems to me this is exactly what X was designed to do?
Bonus points:
You may have noticed there’s also an ssh port open. About that:
It appears to accept password logins, and I have tried all the obvious ones. I’m 99% sure it is running a hella old version of openssh that probably has documented vulnerabilities but again that’s out of my wheelhouse unfortunately. It has been a while since I tried the ssh but I seem to recall having to allow an encryption method that isn’t even supported normally anymore.
Bonus bonus:
There’s a single open USB port on the thing, so naturally I plugged in a keyboard and pressed Ctrl+alt+F3
And yes! it gets me a login screen, but again I have no idea the credentials 
Any feedback would be greatly appreciated!
Calf tax: