@TheCakeIsNaOH I have a [probably] stupid question about security.
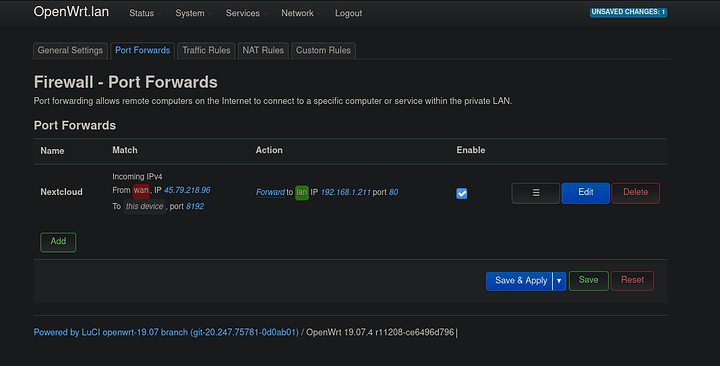
So I got my Nextcloud instance installed on a home “server” (it is just a Rock64 running Armbian Buster) and Nginx on my Linode properly proxies to my home network. Due to my 10mbps upload speed it is very slow, but tbh it’s okay with me. Is it a security flaw during the data transfer between my home network and the Linode? Is there a way I can mitigate this? I have the following port forward set up on my home router:
And that greatly increases the security of my home’s port forward, but I am still worried about the data transferred between my home and the Linode proxy. Also here is my Nginx proxy configuration on my Linode:
#HTTPS Port 443 Configuration
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name cloud.linuxdragon.dev;
location / {
proxy_pass http://68.35.32.227:8192;
proxy_redirect Host off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Url_Scheme $scheme;
}
location /.well-known/carddav {
return 301 $scheme://$host/remote.php/dav;
}
location /.well-known/caldav {
return 301 $scheme://$host/remote.php/dav;
}
# SSL Configuration
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;" always;
ssl_certificate /etc/letsencrypt/live/linuxdragon.dev/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/linuxdragon.dev/privkey.pem;
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
}
# HTTP Port 80 Configuration
server {
if ($host = cloud.linuxdragon.dev) {
return 301 https://$host$request_uri;
}
server_name cloud.linuxdragon.dev
listen 80;
return 404;
}
Also the machine behind my home network is running Apache and the apache vhost is not configured for SSL at all.