TLDR: I’m running into an issue where other peers connected to my Wireguard VPN are unable to ping each other.
Current Setup:
Ubuntu
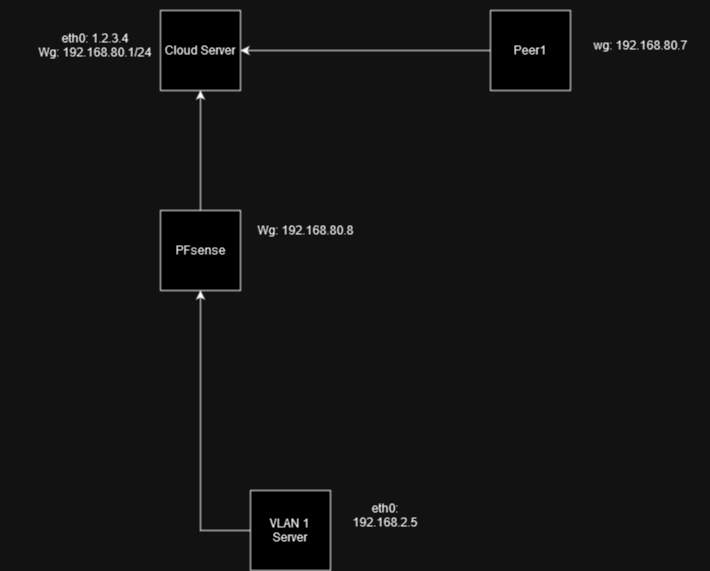
Cloud server as Wireguard server.
eth0: (1.2.3.4)
wg0: 192.168.80.1/24
wg0.conf
[Interface]
ListenPort = 51820
PrivateKey = {PrivateKey}
PostUp = ufw route allow in on wg0 out on eth0
PostUp = iptables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip6tables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PreDown = ufw route delete allow in on wg0 out on eth0
PreDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PreDown = ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
# Peer1
[Peer]
PublicKey = {Public key from Peer1}
AllowedIPs = 192.168.80.7/32, 192.168.2.0/24
# PFsense
[Peer]
PublicKey = {Public Key from PFSense}
AllowedIPs = 192.168.80.8/32, 192.168.2.0/24
PFsense
Pfsense.conf:
# PFSense
[Interface]
PrivateKey = {Private Key}
# Server
[Peer]
PublicKey = {Server public Key}
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 0
“client” to Ubuntu:
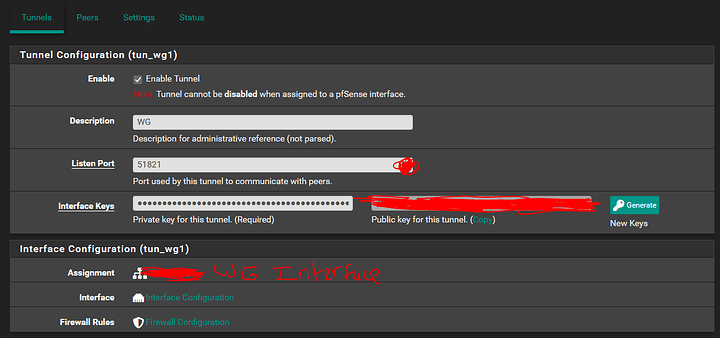
Tunnel Config:
Private/Public Keys generated
Assigned Interface
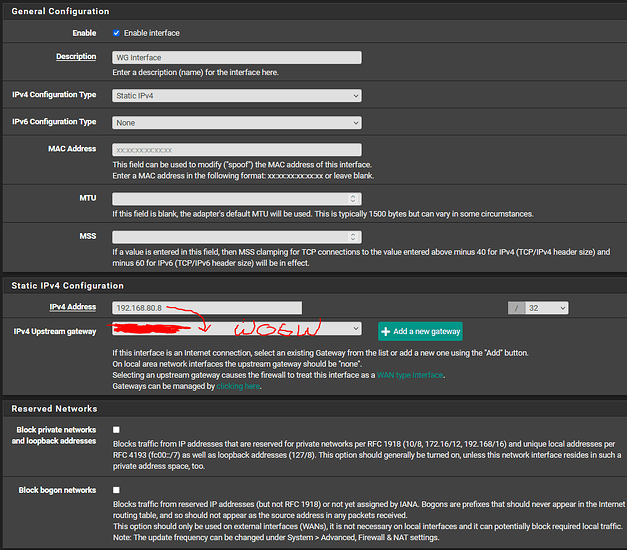
Interface Config:
Static IPv4
No Ipv6
Static IPv4 Config:
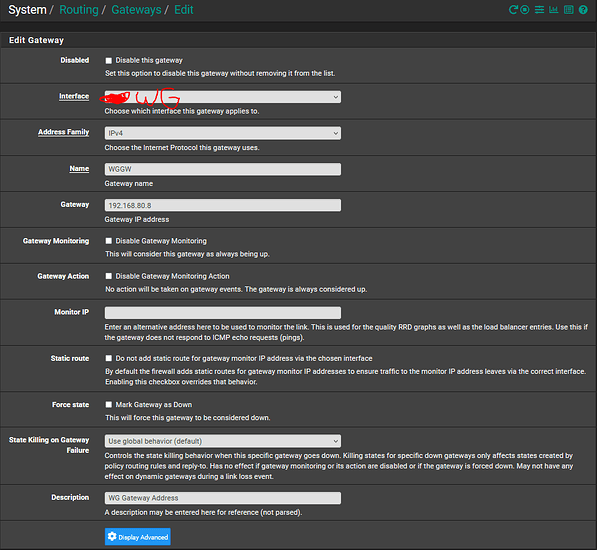
Gateway created: 192.168.80.8/32
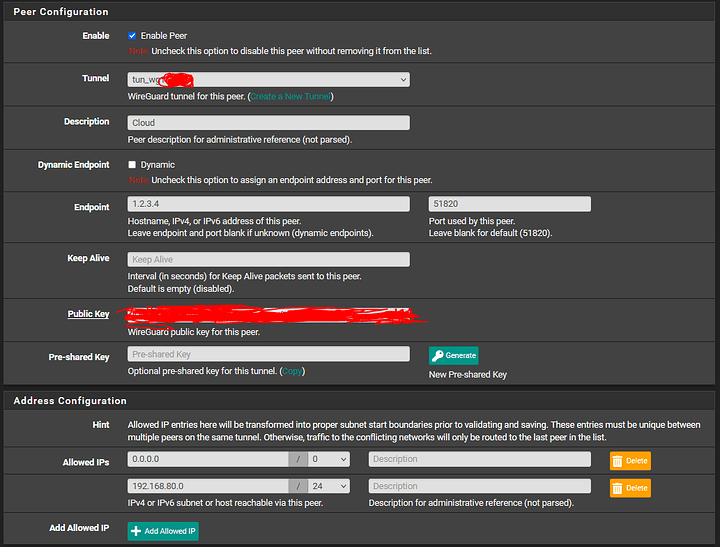
Peer:
Tunnel Assigned
Endpoint (1.2.3.4:51820)
PublicKey: From Ubuntu Server
AllowedIps: 0.0.0.0/0
NAT:
Outbound Hybrid
IPv4+Ipv6
Source: VLAN1
Translation → Address WG address
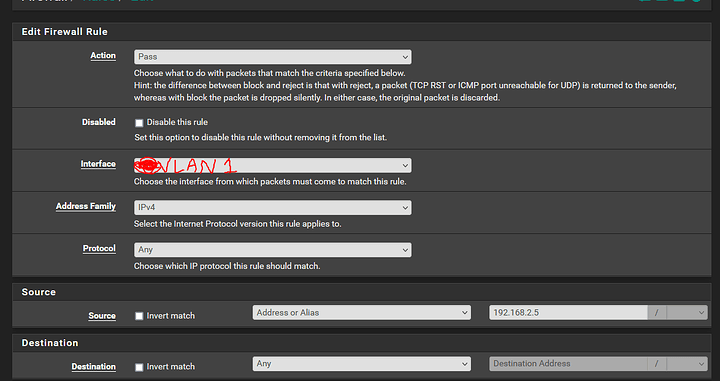
Firewall
Allow one IP on VLAN1 to use VPN connection
VLAN1:
Pass
Interface: VLAN1
Protocol: Any
Source: 192.168.2.5
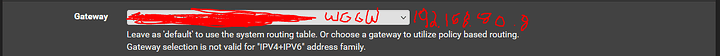
Gateway: WG Gateway (192.168.80.8)
Peer1
Peer1.conf
# Peer1
[Interface]
PrivateKey={PrivateKey}
PublicKey={PubKey}
Addresses= 192.168.80.7/32
# Server
[Peer]
PublicKey={Server Public Key}
Endpoint=1.2.3.4:51820
AllowedIps= 0.0.0.0/0, ::/0
Diagram:
When trying to ping the server on VLAN1 I never get successful packets. Even when trying the PFSense interface (192.168.80.8).
I have a feeling its related to NAT or Firewall rules but I’m not sure what to start at.
Running sudo tcpdump -tttnei wg0 icmp on the Wireguard server I am able to see that the server behind PFSense is able to ping out and get a response but when the peer outside of PFSense reaches out the packets stop at PFSense.
Would it be a correct assumption this could be a firewall problem with PFSense?