Okay so from what I understand you should have three interfaces on pfsense. WAN, LAN and WIFI (or OPT1, or whatever you want to call it, but I'll refer to it as WIFI here).
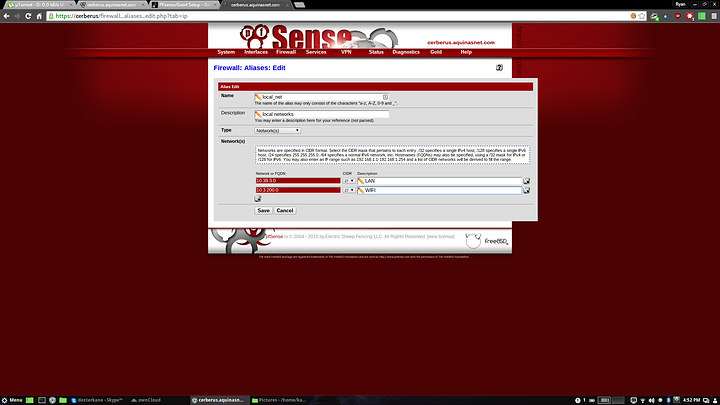
The LAN network is 10.39.3.0/27 with an interface address of 10.39.3.1
The WIFI network is 10.3.200.0/27 with an interface address of 10.3.200.2
If I've got that wrong then you should be able to substitute the correct info in, but that's what I'll be using for this explanation.
There's a couple of things you want to keep in mind when making firewall rules. The first is that the rules are processed first match top to bottom. So that means that traffic is cheacked against each rule from the top of the page down and as soon as it finds a rule that matches then that rule takes effect. So you can have overlapping rules but the first one will be the only one which counts.
The other thing to remember is that the rules are always from the perspective of the pfsense box. This means that inbound traffic is traffic entering one of the pfsense interfaces and outbound is traffic leaving. For example if you're talking about you internet download traffic then on the WAN interface this is inbound traffic as it is entering the WAN interface, but on the LAN interface this is outbound traffic as it is leaving the LAN interface. So when you write firewall rules the source address is always something connected to the interface and the destination address is either pfsense or something on a different interface.
By default pfsense blocks everything so you need to create rules to allow traffic between interfaces. The LAN interface will have a default allow any rule but new interfaces (like your WIFI interface) will not, so by default your wifi devices will have access to nothing. So the default action is to block but for the rules I'm going to show you we will change that and make the default action to allow, the same as it is on the LAN interface. I find this way a little easier to understand and work with but you can do it either way.
The first thing you want to do it create some aliases. Aliases are awesome and I recommend you use them for all your firewall rules. You can use them to create a group of IPs, ports or networks but they're also good for naming a single IP, network or port. So it makes it much easier to see what your rules do.
The first alias you want to make is for the static IPs of the devices on your wifi network which you want to allow access to your LAN network. To create aliases go to firewall>aliases.
I've called the alias wifi_allow but you can call it whatever you like. Choose hosts as the type and add each static IP bellow. Now when you make the firewall rules you only have to make one rule for this alias rather than a rule for each IP.
You can also make a similar alias for LAN IPs if you want to allow access only to certain IPs. But if you want to allow access the the whole network then you don't need to worry about it.
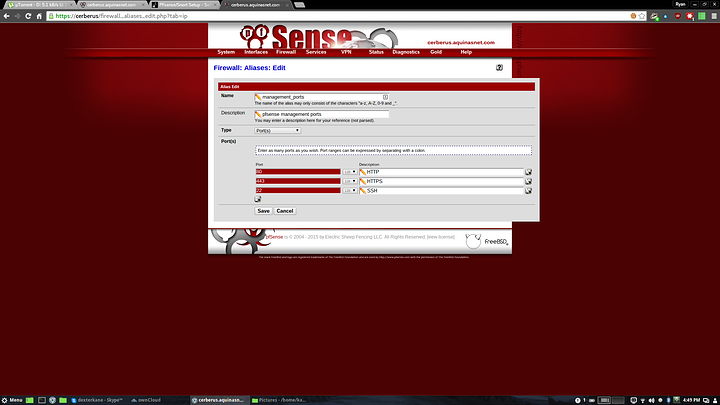
The next alias you'll need is a port alias, which I've called management_ports
This alias will be used in a rule for added security, which I'll explain when we get to it.
Another alias that I find useful but which won't be used in these rules is a local network alias. This is an alias of all your local networks and can come in handy for some rules.
I've set up these rules on my pfsense machine on an interface called TEST, but in your case it will be WIFI or whatever you decide to call it.
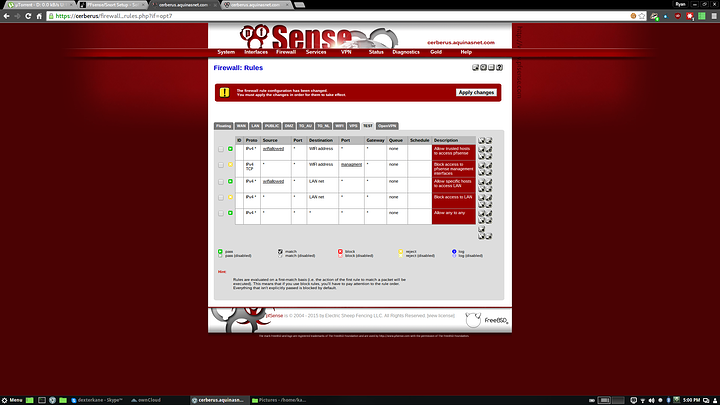
From top to bottom the rules are:
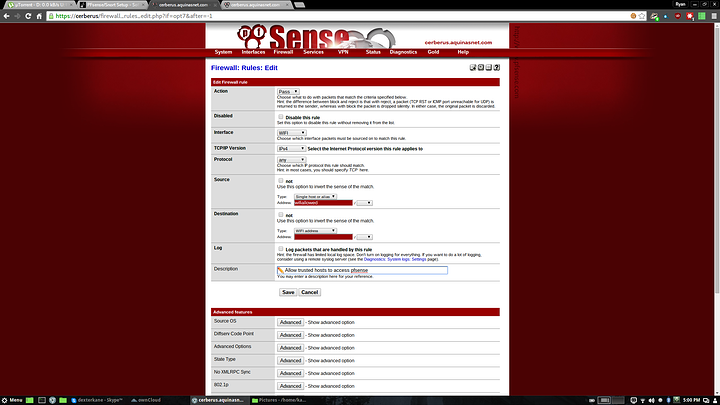
1. Allow access from the wifi_allowed alias (your static IPs of trusted devices) to pfsense (so you can access the webui)
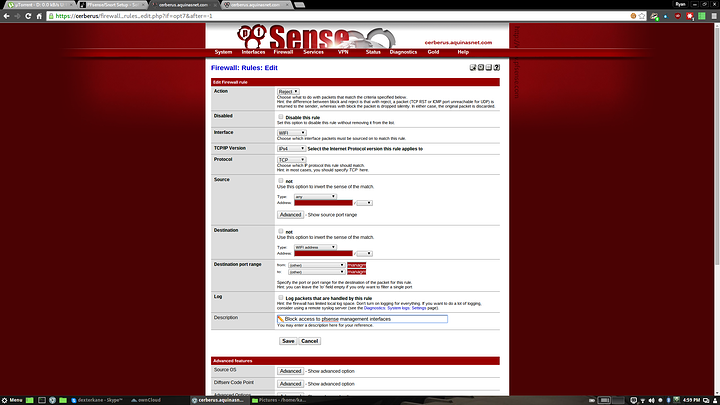
2. Reject access from any to the pfsense management ports (80 443 and 22). This rules prevents unauthorised IPs from accessing the webui or SSH while allowing them to access DHCP, NTP, DNS etc.
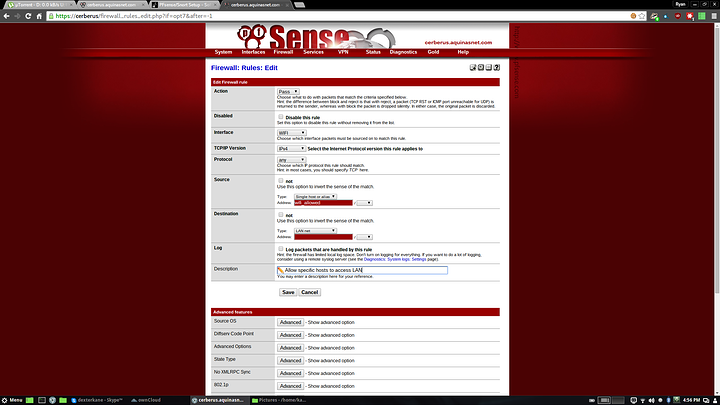
3. Allow access from the wifi_allowed alias to the lan network.
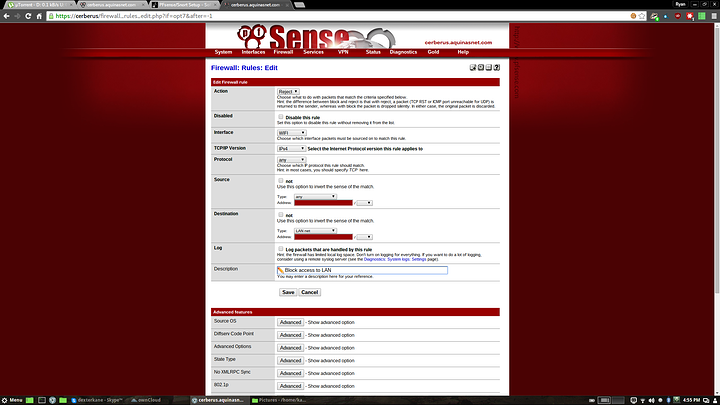
4. Reject access from any to the LAN network. Because of the above rule only the static IPs in the wifi_allowed alias will have access to the LAN and everything else will be rejected.
5. Allow any to any. This will allow access to everything not explicitly blocked by the above rules. You need this rule to alow internet access.
You can remove the first rule and just use the LAN address of pfsense to access the webui, as this will be allowed by the rule allowing access to the LAN network. But it is handy to have access from both interfaces incase you accidently lock yourself out.
The reason I use reject rather than block for internal networks is that it makes the network more responsive. When you try to access something which has a reject rule the connection terminates immediately whereas with a block rule it will have to time out. Blocking is useful for rules on your WAN address as some argue that it adds security by making it hard to tell if there is something at the address or not (block gives no response while reject tells the client that access is denied). If you'd rather use block rules you can.
You can make similar rules on your LAN interface if you like or just use the default allow any to any rule.
Bellow I will give an explanation of how to configure each rule, starting from the bottom as new rules are added to the top (you can move them around if you need to).
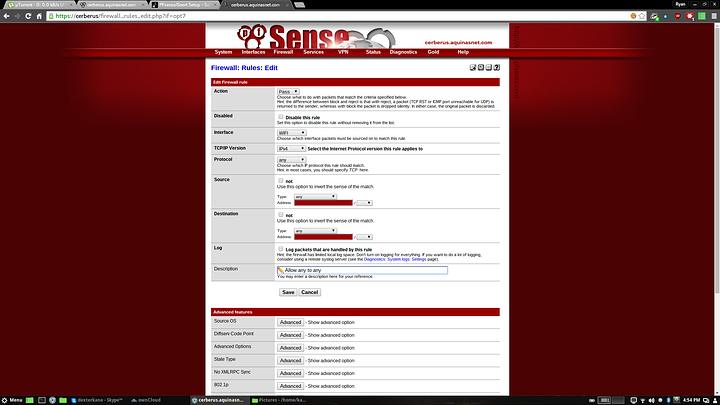
The allow any rule. Set action to pass, the protocol to any, the source to any and the destination to any
The reject LAN rule. Set action to reject, the protocol to any, the source to any and the destination to LAN net. You can also set it to network and manually input the LAN subnet, but the LAN net option will be the same.
The allow LAN rule. Set action to pass, the protocol to any, the source to single host or alias and use wifi_allowed (or whichever alias name you chose) and the destination to LAN net
The reject pfsense rule. Set action to reject, the protocol to TCP, the source to any the destination address to WIFI address (you can also choose single host or alias and use the wifi interface address here (10.3.200.2)), and the destination port to other and the alias management_ports (or whatever you called it). This rule blocks ports 80, 443 and 22 on the pfsense interface. If you wanted to make this rule stricter you could create an alias of both interface addresses fro pfsense (10.39.3.1 and 10.3.200.2) and use that instead of WIFI address. This will block access to both the LAN and WIFI interface addresses. In this case it makes no difference as access is already denied, but in a more complex configuration you may want to do it.
And finally the allow pfsense rule. Set action to pass, protocol to any, source to single host or alias using the wifi_allowed alias, and destination to WIFI address.
Hope you made sense of all that, getting your head around firewall rules can be a little tricky at first but once you understand the logic of it it's fairly straight forward.