When I set up OpenVPN on PfSense I get an interface for every server and client configured. I can choose to assign these and set up rules for them and there is also an entry in the fw Rules for OpenVPN but I don’t see any interface statistics or if configuration for it, I can configure rules and NAT but what is it for since all the OpenVPN configs also get their own if?
So each interface that appears is for a client. (The PfSense box connecting to another server).
Whilst the OpenVPN one is for the PfSense box acting as a server (clients connecting to PfSense).
So unless you are remotely connecting via an OpenVPN server running on the PfSense box, you will see no statistics against the rules.
But I have two OpenVPN servers (one is remote access and is site to site) and they each get interface ovpns1 and ovpns2 while clients get ovpnc1, c2… cN.
If I assign these interfaces it lets me get if statistics but OpenVPN never shows any stats, it can’t even be selected for stats in the GUI afaik.
Oh, so you’re after statistics that OpenVPN is spitting out?
If so, that’s under status>OpenVPN.
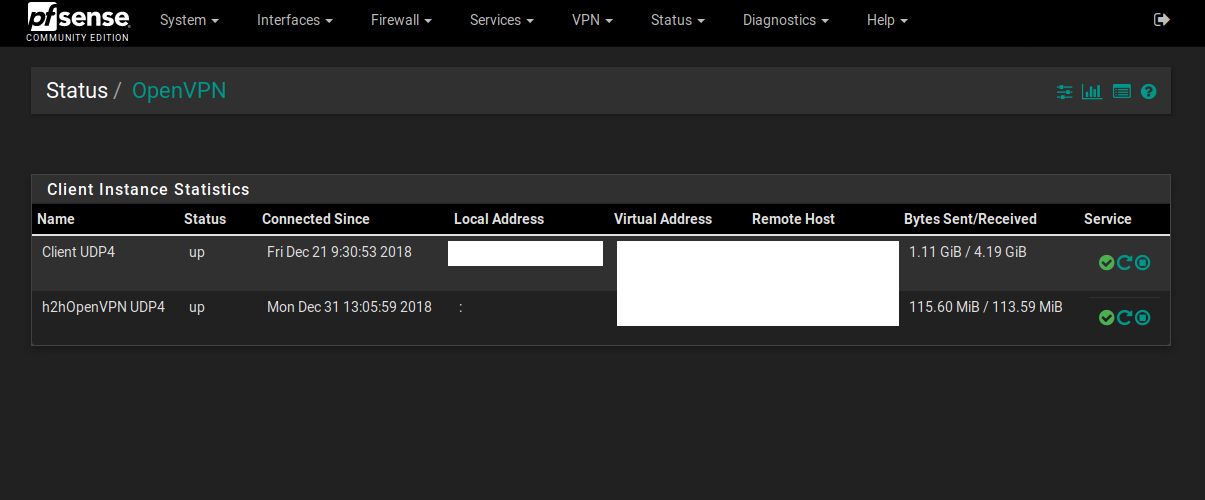
That page will show you a break down of servers and clients. On the servers it will show who is connected (if you are using users and psk’s it will show a common name for each user) and what their IP is.
As for clients it will show if and what it is connected to.
For each client and server there is also a Bytes Sent/Received value as well.
Not exactly, I’m trying to get my head around what the interface is for and what the fw-rules i set to it do.
Since all configured clients and servers have an interface I can assign I want to know what the OpenVPN interface is for, how do the rules I assign to it govern? Do they supersede the rules for the interfaces of OpenVPN clients and servers that I also have or the other way around? I could probably find out through trial and error but since it’s a matter of security I kind of want to know the theory
Here is from another pfsense, it only has two OpenVPN clients.
This is the status page
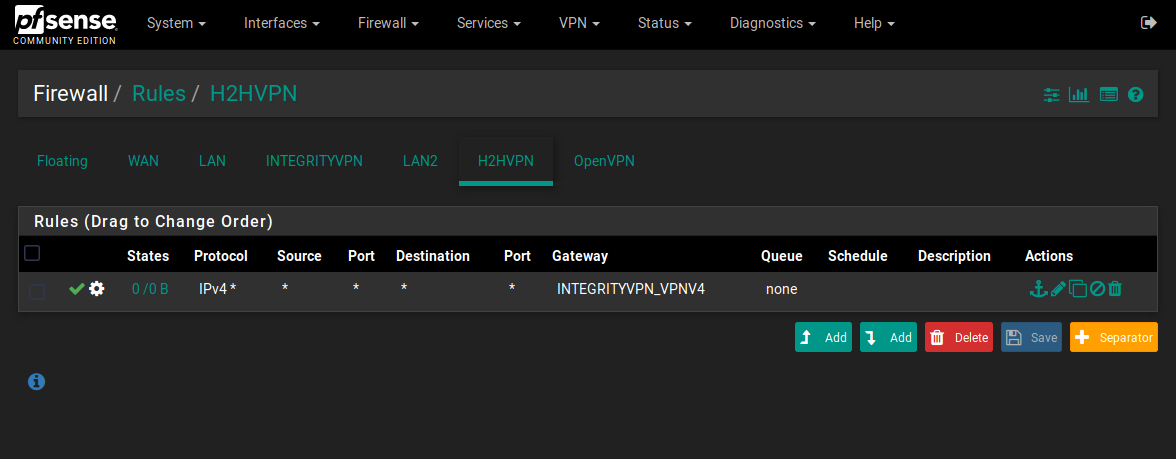
Ant this is the fw rules page, client on the status page is INTEGRITYVPN on the fw rules page. H2h is h2h from status but I also have the OpenVPN interface which I don’t really understand.
Ahhh, right. I’ve got you now. (I’ll add a bit of an explanation for anyone who comes across this in future)
Typically all the interfaces within PfSense with regards to the firewall act as traffic passing through and leaving via another interface.
So say you want to apply rules for traffic leaving LAN for WAN, you apply it to the LAN interface.
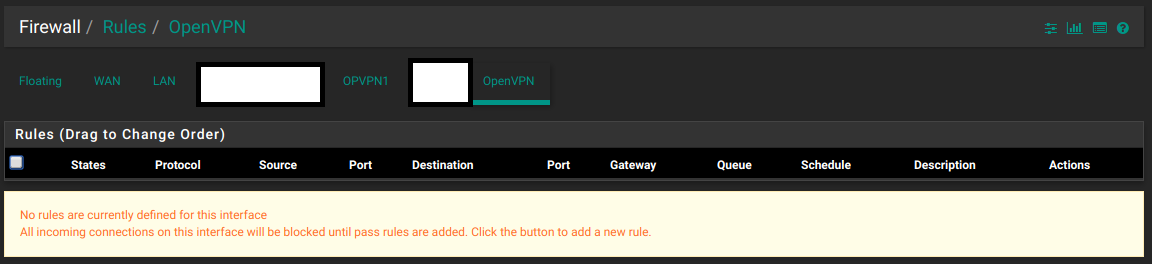
However, OpenVPN is not the same. All the traffic leaving ANY OpenVPN instance comes from the OpenVPN interface, not any specific interface you add for a particular server or client process.
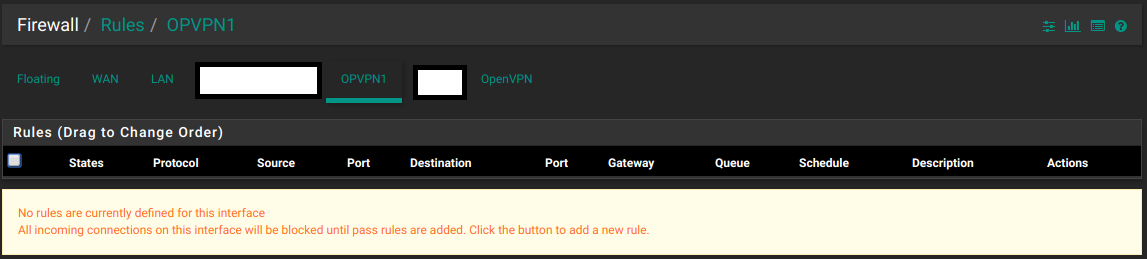
In the case of OpenVPN server running on PfSense, under interface assignments you get an OVPNS# interface. Any rules applied to this interface have no effect on anything. The only reason you’d assign and enable this interface is to allow firewall rules going INTO the OpenVPN process.
For example, with an OVPNS# interface assigned I can now manage traffic from my LAN into connected VPN clients. (Below I have allowed all ICMP and blocked everything else).
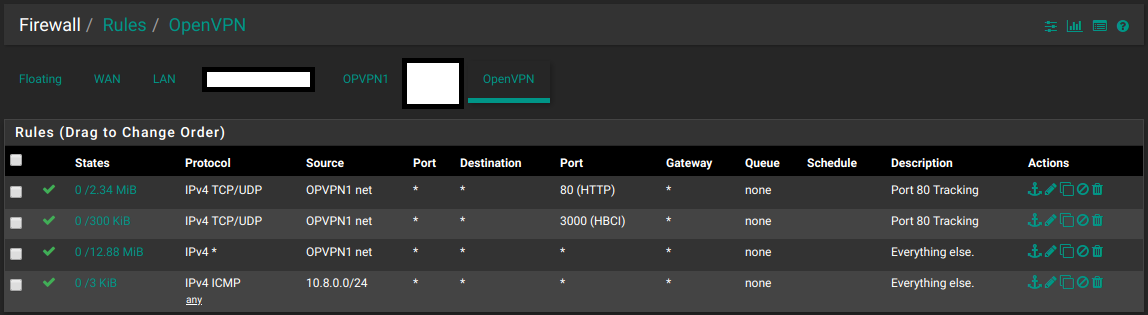
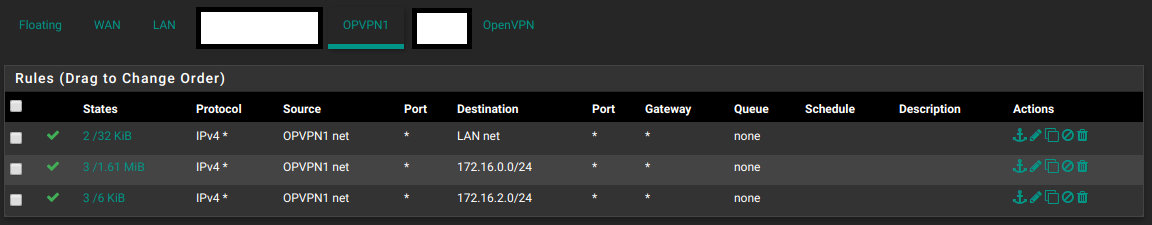
As for traffic coming from OpenVPN, you apply the rules to the OpenVPN interface. As you can see, you can still specify the source as one of the other interfaces. (or a CIDR notation in the case of the last one)
If you do not assign the interface, you can still add rules to the OpenVPN tab, but you can only do it via CIDR notation. (or aliases)
This all works whilst the server OPVPN# Firewall rules look like this:
This interface is only for software interfacing (as can be demonstrated by the interface assignments page)
Hope this helps.
You are mostly correct.
If you remove or disable all rules in OpenVPN interface, individual OVPN device interface rules take effect.
Not sure which is a better approach.
Upon further investigation, it seems they work hand in hand.
Where the OpenVPN interface is checked before the Connection Specific interface.
As with most Firewall rules, it checks until first match.
If you put a bunch of specific universal allow/deny rules in OpenVPN then connection specific rules in the dedicated interface that would not otherwise match the universal rules.
Ahhh right, well that would be why I never came across a situation where it worked for me.
From an organisation stand point, I would say putting the rules under specific interfaces would be the better approach. Because even though in my screenshot I only have a few demonstration rules, that could get messy quickly.
Just a quick test and indeed as @DeusQain says, Interface specific rules indeed kick in after the OpenVPN table.
The following setup also works where I have rules in the OVPN# firewall interface and nothing in the OpenVPN tab.
In my opinion, based off this new knowledge; I would say if you only have one server or client based OpenVPN process on your PfSense box, then putting rules in the OpenVPN tab will work. However, with multiple server instances I would use the specific interface as it just keeps it easier to organise.