I have pfSense fully configured on one interface, the LAN interface. It has Squid, Squidproxy, and a Captive Portal using FreeRADIUS authentication all running like a dream. I added a secondary nic, and configured it from the terminal (assigned the interface, set the ip). I then went into the GUI and configured Squid/Squidproxy and the captive portal on it. The only issue is, it has no internet access. I can ping the interface (154.154.1.1), but nothing past it. I really don’t know a whole lot about networking, this whole project has been a lot of trial and error, so I have no idea where to begin. I’ve been struggling with this for a few days now, and I figure it’s probably time for me to ask for help.
A few more details:
The third interface, OPT1, is connected to a Ubiquiti ap-ac-lite. I know that’s not the issue because I’ve used it just fine with the LAN network, and I can’t get an internet connection even if I plug my laptop directly into the OPT1 interface. DHCP seems to be working fine, I get assigned an IP from the correct range, etc etc.
One thing is I don’t know jacksquat about firewall rules. The rules that the firewall came with are still there, haven’t touched them, so any help with that would be MUCH appreciated as well.
Please let me know if there’s other info needed to diagnose this, I am at your mercy gents. And ladies.
Thanks in advance
The OPT interface will have no firewall rules by default, therefore it blocks everything. You need to make (at the least) an allow any to any rule (like the one that is default on the LAN interface) to get it working.
1 Like
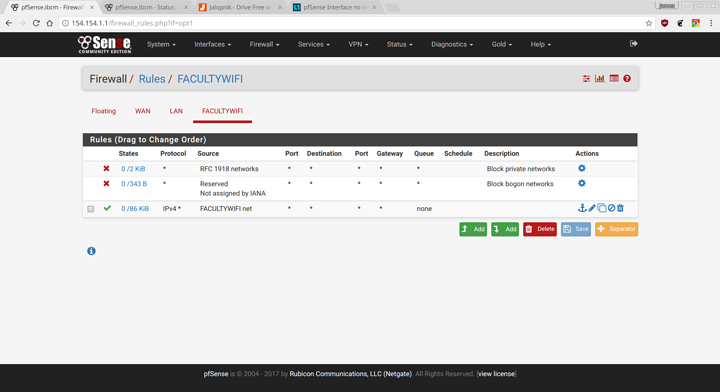
Does this look about right?
The allow rule is right, but you want to get rid of the other two, you do that in the interface settings. You only want to enable those on the WAN interface, you don’t want to block private networks on a private network.
1 Like
Perfect! Thanks brother. Quick question, are there any other rules I should have configured on the LAN & OPT1 interfaces?
1 Like
Depends what you want to do, as it is anything on those networks have access to anything on the internet or the other local network
Well, the LAN interface is for students, and the OPT1 is for faculty only Wifi access. I would guess that I don’t want students to be able to access stuff on the OPT1 interface. How would I set up that rule? Or better yet, do you know of a resource that explains the logic behind creating rules with the pfsense gui?
Keeping in mind that this is a minuscule christian college in Nairobi Kenya. There are 25 students and about 5 faculty.
The logic basically is that the rules are read from top to bottom and the action is applied on first match. So in your case on the LAN interface you want a rule above the allow any to any that blocks from any to facultynet. You might as well have a similar one on the faculty network blocking access to LAN too if there’s no need for access to the LAN network.
When you’re making firewall rules always be aware that you need access to the pfsense interface address, if you block that then you have to reset to factory settings in order to get back in to fix it, so double check before you hit apply. It’s always worth backing up your configuration before you start making rules just in case.
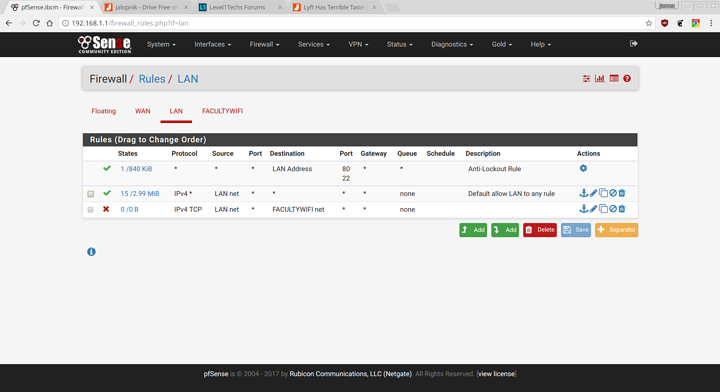
So something along these lines?
Yeah but you need the block rule above the allow rule otherwise it will still allow everything. The rules are matched from top to bottom so the allow any to any will always match and always allow, so you need to have the block rule above that.
You’re probably also going to want a rule to block from any to LAN address on ports 22, 80 and 443 so that the students can’t access the pfsense webui. Just make sure you have access from the other network so you can still log in.
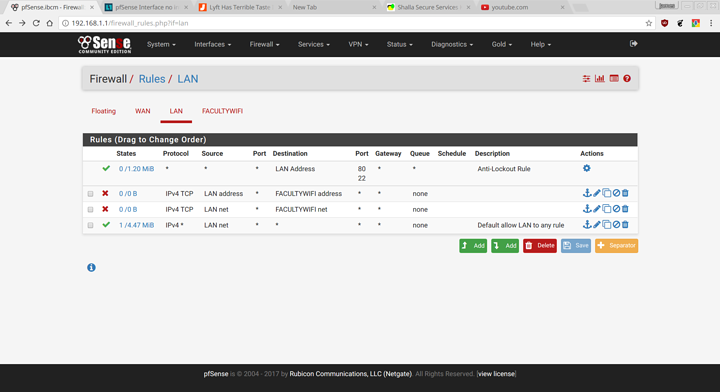
Ah gotcha. Ok here’s what I have:
I can still ping from LAN to OPT1 though, should I reboot?
If you’re happy that you can access the interface from the other network you can disable the default anti-lockout rule, the option for that is under system > advanced on the admin page.
Also you want to change it so that it’s only blocking port 22, 80, and 443, you need to access pfsense for things like DNS and DHCP still so you only want to block the ports used for SSH and the webui.
Also for the rule blocking access to faculty net you want to change the protocol from TCP to any otherwise you will still be able to access that network with UDP, ICMP, etc (which is why you can still ping it)
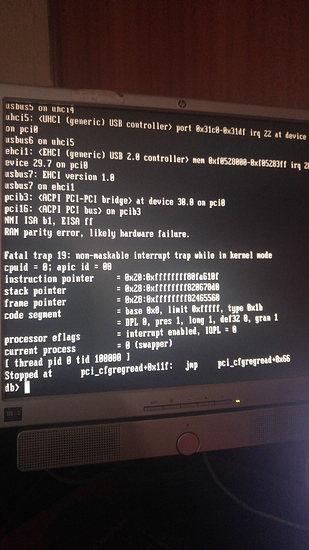
Yeah I don’t know. What happens when you reboot it?
RAM parity error, apparently. I’m pulling sticks right now.
Boots fine with one 2GB stick. I’m going to blame mismatched RAM purchased used at a small computer shop in an alley in Nairobi. And also dust.
Took all four sticks out, added one at a time back into the system. Now all four are back in and everything is peachy. No idea.