Hi lads, thanks for the pfsense stuff!
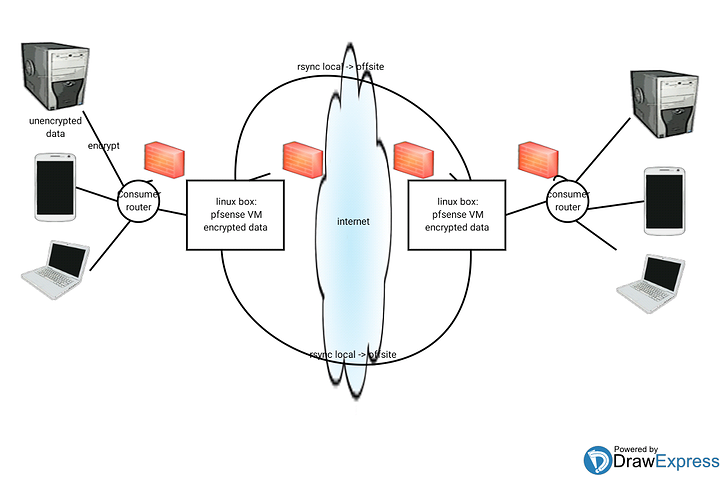
I’m Looking for some detail on how to set up a DMZ using pfsense. I need to set up some offsite backups. Here is my current idea:
(The amount of data is quite big and I don’t want to pay for cloudspace )
- Looking at Crashplan or Rsync to do the backup.
- Either program needs to open a port to the outside world.
- Planning to use Pfsense with OpenVPN to make sure the port is secure.
- Guessing best practice is to isolate the server opening the port from the local lan (on either or both sides) using a DMZ.
- Use data encryption as the data will reside in the DMZ.
Is this the best way ? If so, how do I set up the DMZ? If not is there a simpler way to do secure offsite backups ?
Additional question, what’s required on the hw side for the (old pc) server to be able to wake on vpn login or waking up at a certain time to not waste kwhs when not backing up?
Thanks!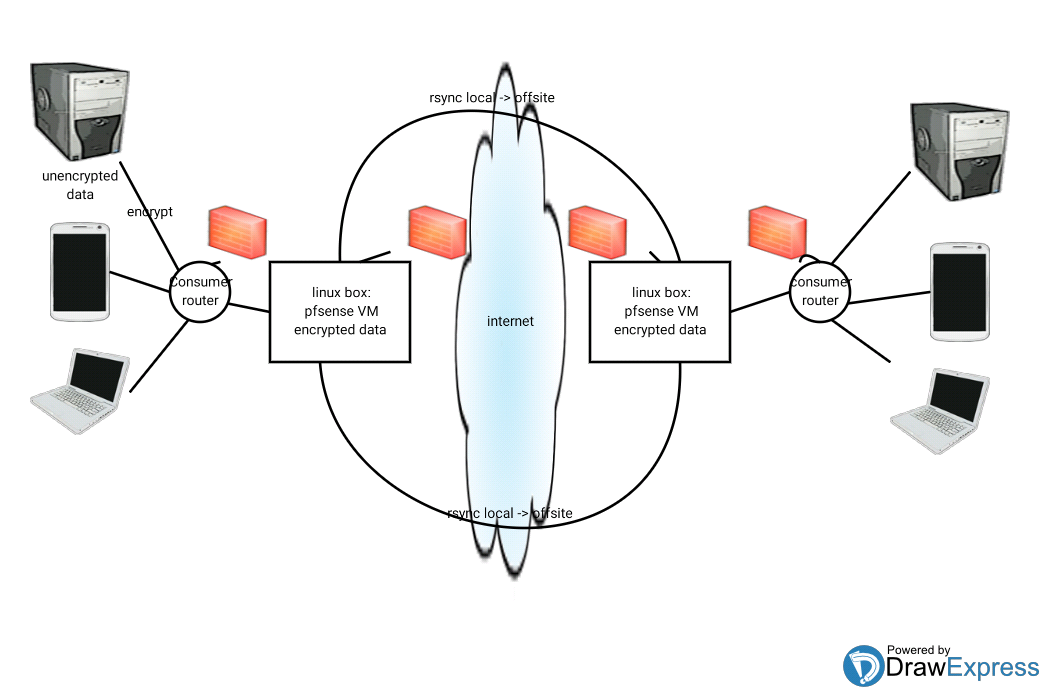
1 Like
A DMZ for incoing ports makes sense but for outgoing only an rsh tunnel might make more sense.
Hey, thx for the response.
I guess I need:
Site A Server in DMZ listening for requests to backup from Site B
Site B Server in DMZ listening for requests to backup from Site A
Or if I make sure they are done in the same time window I guess I could eliminate the second DMZ altogether. Site B could just assume that the VPN should be up at certain times and run the backup.
Or am I missing something? It seems to me I need to open at least 1 port for incoming.
If you're using a VPN to link the two sites then I wouldn't worry about the DMZ as neither backup server are exposed to the public internet. But if you want a DMZ network then you just need to add another network interface (or use VLANs if your hardware supports it) and make the appropriate firewall rules.
1 Like
Hmm.. The more i look into this, the more confused I get 
I do have 2 Linux boxes that I planned to stick between the internet and the local lans. One on each side with two interfaces. 1 interface to the internet directly (pfsense, virtual appliance), 1 interface to the current consumer router (to retain same security as before) and behind that local lan. That's assuming the local lan needs to dump encrypted data into the DMZ directly. Then the 2 linux boxes can offsite backup between each other using openvpn or just ssh perhaps.
How would you prevent the backup servers from being exposed ? At minimum they need a port opened which I guess means they ideally should be DMZed?
I also don't completely trust the other sites local lan so to cure my paranoia I'd like to avoid that the local lans get merged.
Thanks for the comments