I have 2 Xbox Ones. The first one is just the regular Xbox One original model. The second one is the new Xbox one S (white).
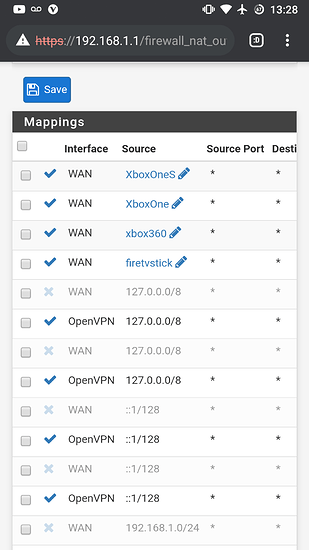
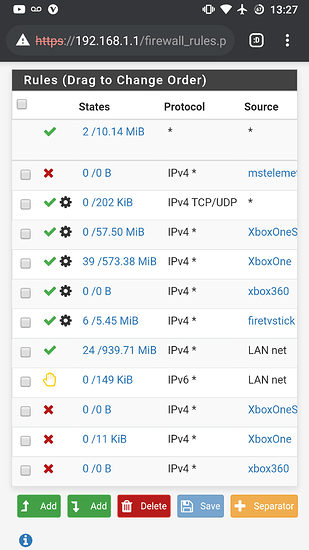
I run a very neatly configured pfsense firewall behind all of this, with both Xbox’s properly whitelisted from openvpn through their Mac ID’s, going through regular Comcast internet.
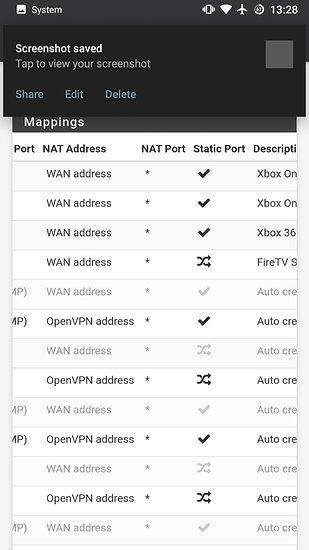
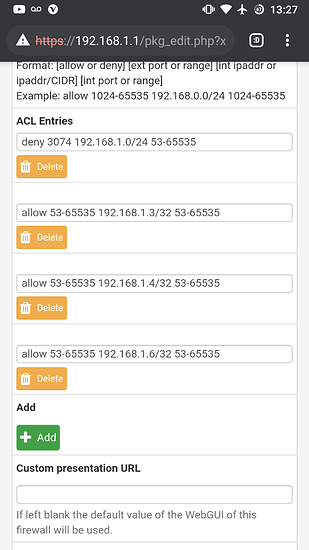
I’ve given both xbox’s unique static ip’s and static outbound ports as per the instructions on pfsense forums.
I’ve enabled natpnp, and upnp in pfsense upnp settings. I’ve created forwarded port range rules within upnp, 53-65535. Blocked port 3074 to prevent the 2 Xbox One’s from having conflicting ports.
The Xbox One S will sometimes work perfectly with an open port for an entire day. Other times it seems impossible to get it to open.
The original Xbox One always has an open port. Never had a problem with it.
The configuration is literally duplicated from one Xbox to another, with their Mac ID and internal IP the exceptions.
Am I missing something here? Did Microsoft change how the Xbox One S uses forwarded ports?
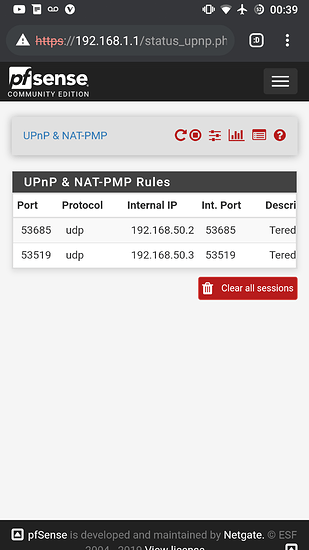
For the Xbox one S I even get a forwarded port on pfsense, going to status -> upnp. But the Xbox one s never aligns itself to that forwarded port. The Original Xbox one does.
Something is arie here with the Xbox One S and I want to get to the bottom of it.
Xbox One IP: 192.168.1.3
Xbox One S IP: 192.168.1.6
Thank you for your time