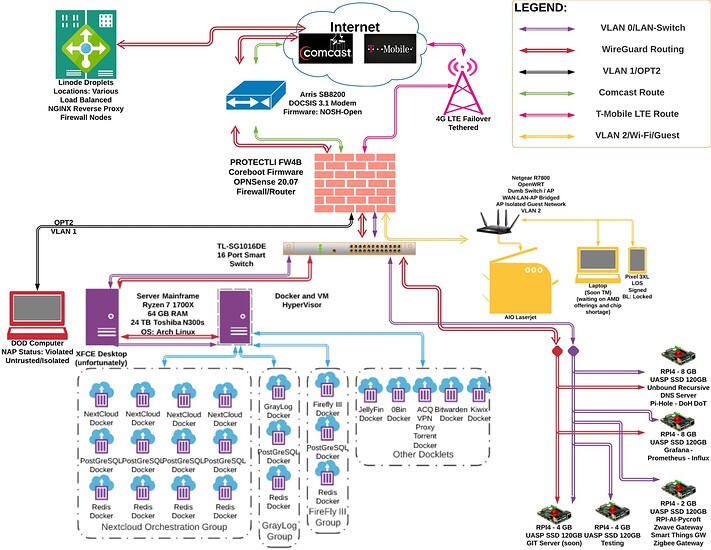
A vlan is a “virtual lan” and it’s a layer 2 concept (switching). If your switch has vlan support, you can configure a subnet (layer 3) for each vlan.
So, instead of having 1 subnet per router and switch ports, you can have multiple subnets on 1 switch and 1 router port. Imagine vlans as having another router port and another switch attached to it, but it’s virtual, happening on an already existing port.
Your switch has to support vlans, so after you look for your switch model and “vlan support” we can continue with that. Layer 2 is not that hard.
I probably shouldn’t throw out the layer 2 / 3 concepts at this point, just to avoid a bit of confusion, it’s not a lot of information, but it’s a bit hard to digest. For short though, IP packets get encapsulated in Ethernet frames (another packet basically, kind of like a box in a bigger box) and the Ethernet stuff talks locally using MAC addresses. So computer aa:aa:aa:bb:bb:bb will send the frame to router bb:bb:bb:cc:cc:cc. The router decapsulates the frame, reads the IP source and destination, looks at the routing table to see where it should send the packet next, re-encapsulated the IP packet into a new frame and sends it from MAC address (of the egress / outgoing port) bb:bb:bb:cc:cc:dd to another router (or straight to the target computer if it’s on the subnet on the other router port) with MAC address dd:dd:dd:ee:ee:ee.
When you connect 2 PCs via one Ethernet cable, this is called a broadcast domain. If you connect a PC to another PC via a switch, the broadcast domain expands to every switch port. A broadcast domain is stopped at the first (ingress / incoming) port of a router. VLANs encapsulate and restrict those broadcast domains, so the devices assigned to a VLAN can’t talk to another VLAN, even if they are on the same physical switch, unless they route traffic through the router and back to the other VLAN. Each VLAN has its own subnet.
Hope this was not too confusing. I tried to keep it short.
But, getting a bit muddy here, it is possible to have multiple subnets on a single switch / single vlan, just that you don’t get any security benefit for doing that. You can set 2 IP addresses on an interface and have certain MAC addresses get IPs from a certain subnet and the rest from another subnet, but even though it will be the same switch everything lies on, the different subnets will still have to go through the router, even though the hosts have the same broadcast (layer 2) domains. Yeah, I probably shouldn’t have mentioned this, but I took some time to write this, so I won’t let the comment go to waste. Ask for questions if anything is confusing and come back with the answer regarding vlan support on your switch.