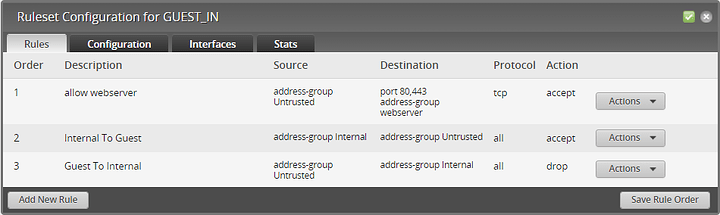
I’m trying to block untrusted networks from my internal network with two exceptions:
- Any device on the untrusted network can hit my public webserver on Internal.
- Any device on Internal can manage any device on Untrusted.
I applied this to the IN direction on all Untrusted interfaces with a default of AcceptAll.
Half of it works as expected. The untrusted clients can hit the webserver (after fixing the hairpin NAT issue). But why can’t Internal connect to Untrusted? If I remove the third drop-all rule, then traffic flows both ways.
I only have policies on WAN (IN, LOCAL) and Untrusted (IN, LOCAL) interfaces. There isn’t a policy defined on the Internal interface.