TLDR
Learning about safely hosting dynamic sites, don’t know crap so don’t take this as a guide.
Disclaimer
I have hacked together some tools for internal use, but I’m not a professional developer or server administrator, so don’t take this as a guide, I’m just documenting some of my experiences with DIY hosting in a dangerous, not in the safety of my home/work network environment. Along the way I’ll ask community for input about my thought process and what I may be missing. You are free to poke, criticize, break or ruin any of the publicly listed resources/choices. It’s going to be a while, lot’s to learn along the way, but I’ll try and keep the post up to date.
Resources
Server
It’s a nanode instance in Frankfurt, DE data center, with the following IPs:
- 172.105.247.84
- 2a01:7e01::f03c:93ff:fe37:184d
Domains
Still thinking about it, will probably go one by one.
Repos
TODO, I have to take git crash course.
Major tech
- Ubuntu 20.04 LTS (I know, I know - it should be arch or alpine, maybe later)
- Nginx as the web server
- PHP - PHP attracts bad “programmers” so there we go
- MySQL / maybe SQLite for the database needs
- WordPress because it’s popular
- Laravel because I found it easy to use for my internal tools hackery
- Tailwind CSS because my style and design brain parts had to be surgically removed when I jammed a crayon up my nose as a two year old child
The spark
Some time ago I started playing with Linode and found it to be really interesting. Fast forward few months and I felt comfortable hosting static websites for friends and family and their small businesses. Nginx and Linux server underneath kept themselves up to date, and there was no problems serving static .css and .html assets. I’ve learned about using ssh key pairs to keep intruders out, limiting ssh access to my home IPs, getting SSL certificates with Let’s Encrypt, setting some security headers, and so on.
The plan
Few days ago I decided to boot up a second VM and register a couple of dirt cheap ~1$ domains and host them all using different solutions. One will be WordPress, one Laravel, one vanilla PHP, and one static as before. Basically I want a honeypot to play with and get better insight into how are the bad guys probing things for vulnerabilities so I can implement some poor man’s defense strategies for the real thing. Eventually, I’m planing on converting the static sites into something more maintainable and capable of self-service content updates.
Stage one
Get the server up and running, install required software and generate ssh key pairs. Setup some basic firewall rules and limit ssh access to home network IPs.
Server has been provisioned and I’ve run some basic configuration:
- Login via ssh
- Update, upgrade and reboot
- Generate ed25519 key pair on my laptop
- Copy it over to the server
- Create configuration on the laptop to connect to it using one-line ssh command
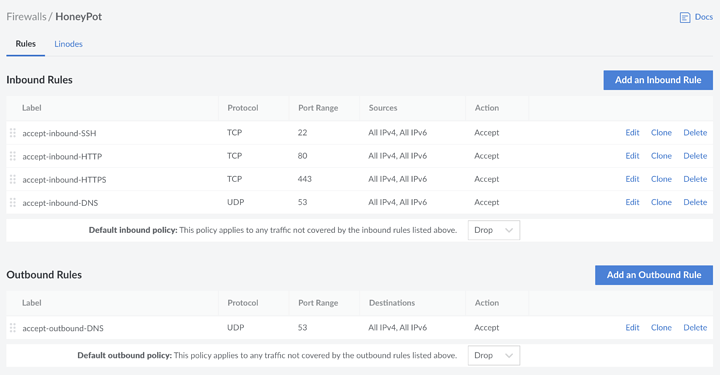
- Set firewall on the server to allow HTTP, HTTPS traffic from anywhere, allow SSH only from my home IP
- Set Linode firewall to allow HTTP, HTTPS, SSH, DNS traffic, just to prevent sending emails or anything similar in case it gets hacked. Linode DNS template is setting protocol to TCP which doesn’t work so changed it to UDP
Commands
#login
ssh [email protected]
#update, upgrade, reboot
apt-update && apt-upgrade
reboot
#generate keys on laptop
ssh-keygen -t ed25519 -f .ssh/linode-honeypot
#copy keys over to server
ssh-copy-id -i .ssh/linode-honeypot [email protected]
#create/edit .ssh/config
vim ./ssh/config
#add configuration to it
Host honeypot
HostName 172.105.247.84
IdentityFile ~/.ssh/linode-honeypot
User root
#set firewall to deny by default and add exceptions
ufw default deny
ufw allow http
ufw allow https
ufw allow from HOME-IP to any port 22 proto tcp
ufw enable
#use Linode control panel to add firewall that can't be changed if the server is hacked, set it to allow HTTP, HTTPS, SSH and DNS (see screenshot bellow)
#install nginx
apt install nginx
#create index.html file with some basic HTML, set permissions, ownership and then delete default index file
vim /var/www/html/index.html
chown www-data:www-data /var/www/html/index.html
chmod 644 /var/www/html/index.html
rm /var/www/html/index.nginx.debian.html
- Change ssh config not to allow password authentication
Commands
#open configuration file, change PasswordAuthentication from yes to no and restart ssh service
vim /etc/ssh/sshd_config
#PasswordAuthentication no
service ssh restart
Stage two
Register a domain, get a virtual host up, get SSL certificates and build a semi-convincing website with chosen $tech = [‘Static’, ‘Vanilla PHP’, ‘WordPress’, ‘Laravel’]. Rinse and repeat.
Stage three
Observe. Look what people and/or bots are doing, learn and document your observations.
Stage four
?
Stage five
Profit.