Hello all,
I’ve been diving into the realm of Homelab’s and I have been severely lacking in my networking design/skills. I have a “draft” of a design that I am trying to create but as you can see there are a few pieces missing that I could use some assistance with. Just a few dots need to be connected.
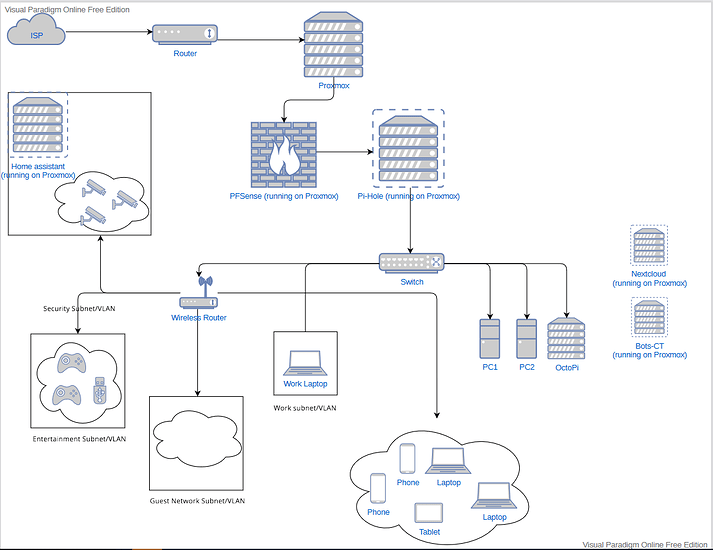
Draft 1:
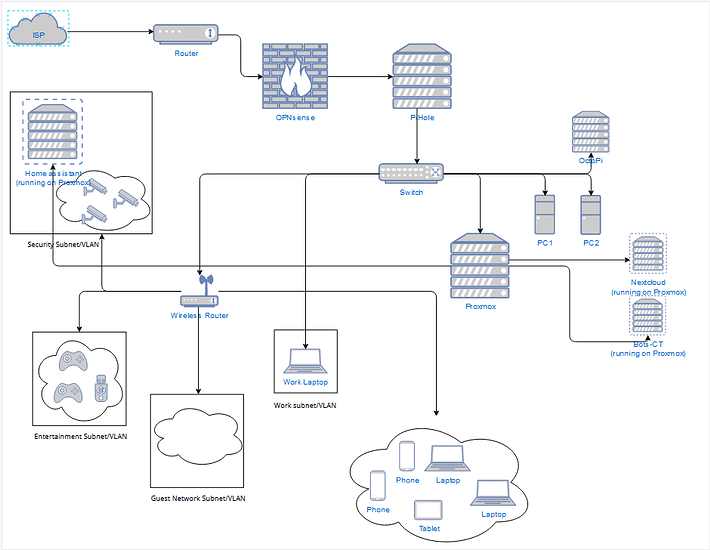
The parts I’m having issues with are getting the Proxmox VM’s on the same subnet/VLAN’s as the different subnet/VLANS listed out (personal, security, entertainment, etc).
So Proxmox will be running the following VM’s/CT’s:
- PFSense or OPNSense → (This might move to a physical machine if needed)
- Pihole-CT → (This might move to a physical machine if needed as well)
- Bot-CT
- Nextcloud
- Homeassistant
I’m looking to have PFSense & Pi-Hole be the firewall/DNS for the downstream networks. I am not sure if that requires them to be ahead of the switch or if they can be behind the switch. (I’m not sure which way would work the best. I am still learning).
Then I wanted to try and group the following:
(I’m not sure if I should create separate VLANS or create separate subnets so as a placeholder I’m using VLAN/subnet, I understand they are different and it could require some other configuration changes but this is a draft plan for now)
- Home Assistant with the security cameras in the
Security(subnet/VLAN) - Nextcloud, bots, with Desktop 1/2 and the wireless network containing the phones, laptops and tablet. This would be the
Personal(subnet/VLAN) (I think I would need another AP/Wireless router to tie this together with the wired connections) - Proxmox web console would also be in a separate VLAN/Subnet to keep access limited.
- Game consoles, and smart tv’s would be in the
Entertainment VLAN/Subnet
If more hardware is required, I can make the additional purchases to achieve my goal. I am really just looking to create isolated groups for better overall security and groupings.
Would it be better to have the firewall on a separate machine, as well as Pi-Hole ? Then put the Proxmox machine downstream from the switch to then manage the different VLANs/Subnets?
Draft 2: