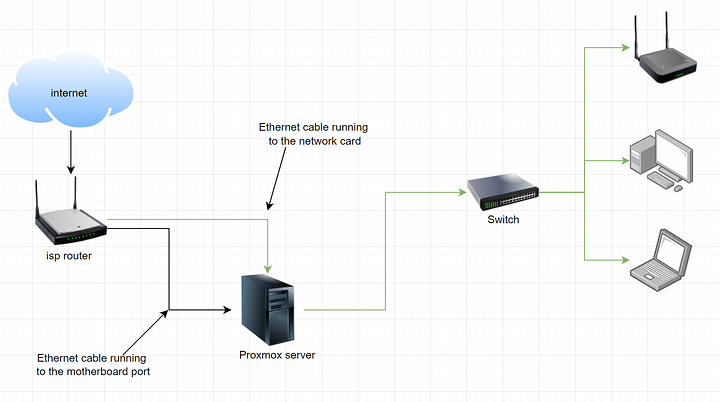
IMO, the easiest option would be to passthrough your PCI-E quad port NIC to your pfSense VM. Make one port the WAN, then use the other 3 for separate VLANs, or even all of them in LACP or balance-alb if your switch doesn’t support LACP.
If you switch is managed and supports port bonding, aka link aggregation (LAgg), then you’re gold.
Wow, a 5 port switch. Ok, not sure if VLANs are even worth doing on such a device.
Nah, simplest way to configure this would be to make 1 LAN on port 2 and connect that to the switch, then on the Proxmox side, create a virtual NIC in the pfSense VM. In pfSense, set that virtual NIC as OPT1 (probably name it proxmox) and set another subnet in there. Then you get away with 3 ports free, 2 from the NIC, 1 from the motherboard.
On the virtual NIC in proxmox, don’t give any IP to the port, assign one in pfSense instead. Then in proxmox, bridge that virtual NIC with its internal network.
The alternative to this would be to just ignore the virtual NIC and set another LAN on port 3 of the PCI-E NIC and connect that port to the motherboard port, then bridge the motherboard port to your VMs like you normally would (all except pfSense). If you aren’t using VLANs, there is no disadvantage to this, but if you do, you will be limited to gigabit speeds between VMs in different VLANs, as opposed to using a virtual NIC with potentially higher throughput.
If you want to set VLANs on your switch. as you have 5 ports, I would suggest you just do 2 LANs, one on port 2, one on port 3 or 4 and set the switch ports to mode-access on different VLANs. Then send the switch port to your router / AP for one WiFi VLAN / LAN and the other to your wired devices. However, this complicates the setup a lot, and if you don’t have any wireless devices that you don’t trust, you are better off just doing 1 LAN and not using VLANs at all on the switch, only because it gives you the advantage of local switching, instead of having to go to the router and then come back to the devices you want to reach, like say if you are transferring photos from your phone to your PC via WiFi.
Anyway, let me know if my ramble wasn’t clear enough, tonight I don’t feel like I can words well.

![]()