The encryption is all done on-disk for OPAL. There is a shadow MBR that may contain an authentication app, as well a multiple zones w/different keys.
So, as far as I was able to understand, if the TPM chip is enabled on the BIOS I will have hardware level encryption for the nvme disk.
A TPM can act as a hardware password (it can also monitor the boot process, and only unlock secrets if it proceeds as expected.)
But a TPM is not a requirement of OPAL itself.
Bitlocker is actually pretty versitile, it can use a text password on opal, or software encryption on top of secureboot. It’s not neccessarily doing the same thing in all cases.
I could also user dm-crypt the encrypt the disk on a software level as well, to have an extra level of security.
The thing about OPAL is, once the drive is unlocked, it’s unlocked until power is removed. If an attacker can pull the drive without killing power, or chainboot into another OS, they get the data in the plain.
Also you have to trust the hardware vendor to get it right the first time (honesly who ever wants to update the firmware of a disk with live data). Also many self-encrypting drives are out there with some level of vulnerability due to improper implementations.
And with dm-crypt it is possible to steal keys via a kernel exploit. This dual layer may prevent some attacks, but not really needed for basic data protection and compliance.
It’s also possible to link your dm-crypt setup to the TPM.
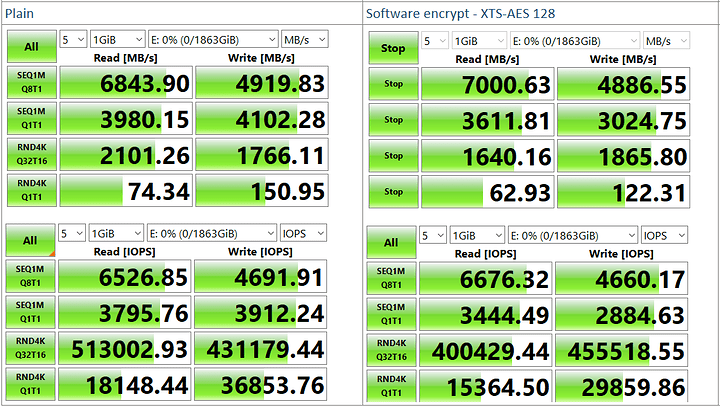
Will any of these setups have any impact on the disk I/O’s performance?
If I encrypt the 970 Pro with dm-crypt, will I be using it’s built in OPAL 2.0 hardware encryption?
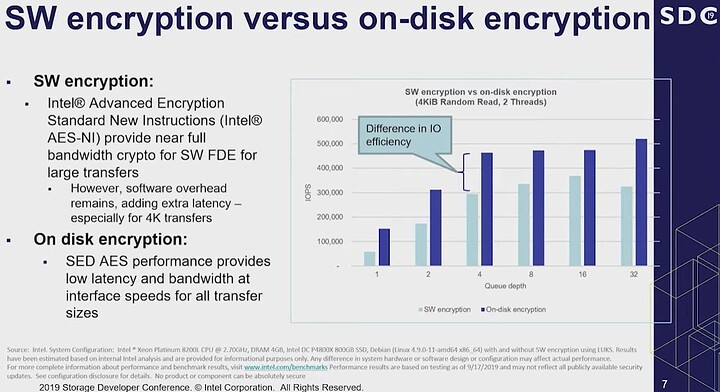
OPAL 2 has no impact on disk performance, as I am lead to believe these drives are always encrypting anyways as a good mix of bits in the cells helps improve performance. Additionally it makes secure-erase compliance trivial and quick.
However dm-crypt does not leverage OPAL at all. The disk controller never sees data in the clear. The nice thing is you don’t have to trust the hardware vendor to get it right and the defualt config works the same was on every system
DM-crypt with AES on modern x86_64 hase very little practical performance impact. The processors have acceleration so there’s not a bottleneck outside high-end workstations, though battery life may be slightly worse if you are hitting the disk a lot.
But not everyone likes AES, and the software option does give you more flexibility.
Personally I’d use on dm-crypt for laptops, and for extra security or convenience to lean on a well tested hardware token rather than on the drive.