I want to learn more about networking but I don’t want to affect the rest of my family. I primarily want to mess around with pfsense. I currently have one ISP AT&T router that connects to the ONT.
So from what I have gathered I need to use my router as a bridge, cascade or IP passthrough. Although I don’t understand the differences between these terms or if they are all referring to the same thing.
What would be the best way for me to set up a separate network to learn on, use daily, that is separate from the other network? Are there also any limitations that I should be aware of using this configuration?
Without multiple public IP addresses, you can’t have a completely separate network (at least not one with internet access). “Bridge mode” is usually the term you want to use when you talk to the ISP to bypass all routing functions and only use the ISP device as a modem.
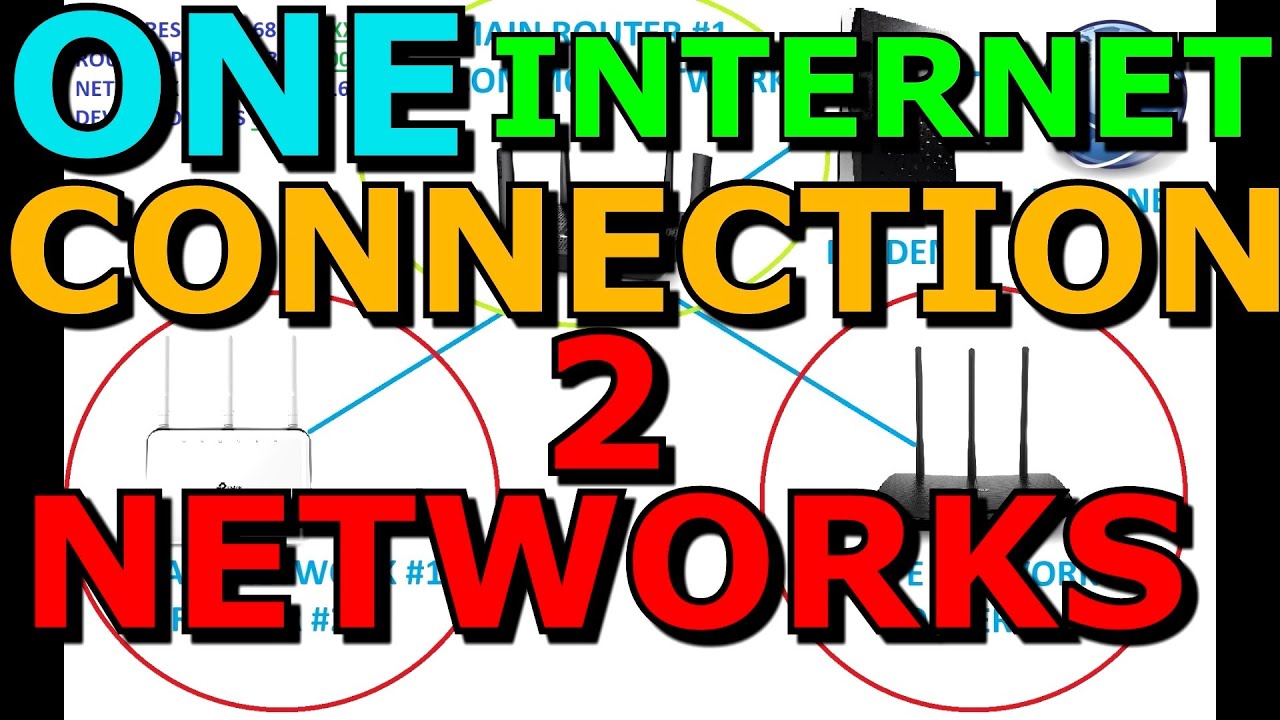
@12_stevo While I don’t know as much about networking as @oO.o, I know a little about the subject. I came across a video on Youtube last night, I think it will accomplish your goal. This video tells you how to set up two private networks and share one internet connection between them. The way this is accomplished is by using three separate networks, two of the networks will be set up to only see its own traffic and the network that passes the internet. Neither private network will be able to see the other’s traffic. As I understand how networking works, @oO.o is correct, 12_stevo can’t have a truly separate network without multiple public IP addresses, but there is a way to accomplish 12_stevo goal by following the instructions in the video I saw lat night.
I will be setting up the same project as you, if you are interested in knowing what equipment I am purchasing, just let me know?
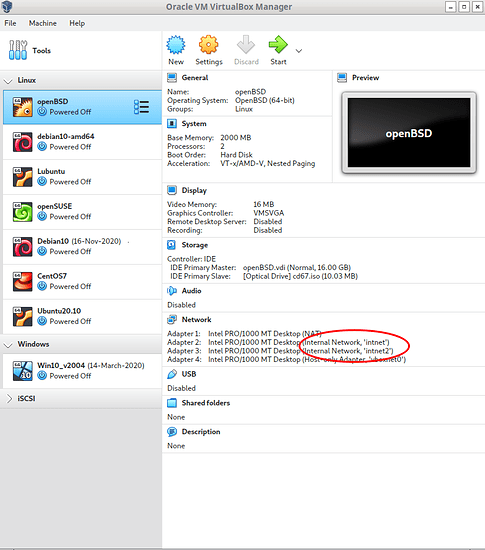
VirtualBox is a very good option. You can install pfSense on a multi-NIC VM which will serve as router for your local network. Then assign one of those interfaces as ‘Internal Network’. You can then create additional VMs that belong to that network.
You can experiment with ip forwarding, access control, run a web service, dns resolver etc.
Here’s one of my test network. I use openBSD as gateway, dns resolver, firewall etc for 2 isolated subnets.
Here’s how to have the ability to experiment with pfSense while at the same time completely avoiding any family acceptance problems, using a technique called double NAT:
-
Assuming you have an Ethernet port available, whether via a switch plugged into your ISP’s equipment or an extra LAN port on your ISP’s equipment.
-
Assuming the setup with your ISP uses NAT (Network Address Translation) which is a pretty safe bet. NAT takes the public IP address assigned by the ISP to their equipment in your home and translates that into a range of private addresses that are used by the devices on your home network.
-
Leave your existing ISP equipment exactly as it is. This means no worries about family approval factor.
-
Specifically, do not put it into bridge mode.
-
Bridge mode disables it’s routing ability and you don’t want to do that.
-
Instead, you will run your pfSense router within your home network, rather than as the router that connects your network to the Internet. That way your family is never dependent on you having a functioning configuration on your pfSense device.
-
Use a device with at least two Ethernet ports for your pfSense router. The WAN port on your pfSense router will plug into an available LAN Ethernet port on your ISP’s equipment or a switch that you have plugged into your ISP’s equipment. So the pfSense router is just another device on the family network.
-
The other side of your pfSense router, the LAN side, is where your “lab” is.
-
In terms of your pfSense experimentation, your “lab” for testing is from the LAN side of your pfSense router in the “lab” ACROSS the router to the WAN side on the family network, and vice versa.
-
Like the other devices on your home network, your pfSense router will get a private IP address via NAT from your ISP’s equipment. This will be it’s WAN address.
-
Then your pfSense router will NAT the private address it received again (thus… double NAT) and give out its own set of private IP addresses to the devices on its LAN side, in your ‘lab.”
-
Double NAT is normally frowned upon. Some Internet services won’t work across a double NAT.
-
With the original configuration of the ISP’s equipment remaining unchanged, your family won’t have problems because of what you’re doing.
-
If you watch any of the Lawrence Systems videos about pfSense on YouTube, this is how he has it setup up for his demos. The only difference is that he is running it virtualized on a server.
I had to double NAT my whole network when I first built my pfSense router because the Intel Ethernet card I was using wouldn’t get an IP address via DHCP from my ISP. But it had no problem getting an IP address via DHCP from either of my other two routers.
In four months I didn’t encounter anything that had a problem with it.
YMMV
That is most likely because the ISP DHCP server has reserved a lease of the MAC address of the WAN interface of your ISP supplied router.
Go to Interfaces -> WAN and set the MAC address of the WAN interface to be the same as ISP supplied router. Then reboot the pfsense box.
Or you could be missing a VLAN tagging.
The LAN and WAN interfaces of routers can have different MAC addresses so keep that in mind.
Plug the ISP WAN port into the LAN of your pfsense box and get the WAN MAC through ARP.
A MAC address is for layer 2 switching and it gets removed after layer 3 IP routing. Which is how some routers have the same MAC for WAN and LAN but some don’t. (To preserve the MAC address they have been assigned for their vendor ID.)
To add to this. Just make sure to not use the same subnet on the Pfsense box as what’s on the ISP router. And don’t enable blocking of private subnets on the WAN. And you’re golden 
I host my own Minecraft server on one of my computers. How would this work with double NAT? Will it just work like normal if both the ports are open on both routers?
I was thinking along those lines but I tried three other routers I had and they all worked without a problem. I didn’t even have to reset the cable modem for them to get recognized. And when I did reset the cable modem, they were recognized. They hadn’t been used with that ISP before, so it couldn’t even be that it had retained their MAC address.
I tried copying the MAC address and that didn’t help. I even had my ISP reset everything on their end and the problem with that Ethernet card continued.
One rainy day when I don’t have anything else to do, I’ll stick it back in and see if I can solve the mystery.🤷
@QuietStealth, from the information you provided in your last post, I get the impression you are having trouble getting the Pfsense setup to work correctly. I am still learning how Pfsense works, but I have gotten my Netgate appliance and house router to communicate. The house router (an Asus router) does, in fact, forward the internet connection to my Netgate device. All I did to get my Asus router to communicate with my Netgate SG-5100 appliance was install all the equipment I purchased for my network, made sure all cables were plug into their correct ports, made sure all equipment was getting power, and turned on the Netgate appliance. As soon as the Netgate appliance finished botting up, I had internet access for my network. I didn’t have to input a Mac address or access Pfsense’s web interface. The Netgate appliance just set up its self. Maybe if you shared more information about the routers you are using, I could figure out why you are having trouble setting up a Pfsense router. By the way, yesterday I set up a Pi-Hole VM to work with my Netgate SG-5100 appliance; The Pi-Hole is so effective my Internet television won’t show my IPTV service without the Pi-Hole running.
No problem with pfSense itself. It’s been working great.
I’m pretty sure the problem I have is with my ISP. I’ve tried three different 4 port Intel server NICs. With all of them, I can’t reliably get a WAN IP address via DHCP from my ISP. One of them was fine for four months. Then I had brown out and it would no longer get a WAN IP address. The other two could never reliably get and hold a WAN address. All three are server grade Intel NICs.
Neither any of the three, if I plug in another router in between my cable modem the pfSense router, so pfSense box is running double NAT, the same three Ethernet NICs have no problem at all getting a WAN address in pfSense.
This is with a bone stock pfSense instal.
My next step is to put the NICs into a different motherboard and see if that helps.