Not sure if i like Nvidea to get their grubby little fingers in to this honey pot, not that they’l try some gpp shit or something. You know cause transparency for gamers
That is new, isn’t it? It’s slow, like really sloooowwww, but …
Called NetSpectre by the team of Graz University engineers who discovered it, the weakness is a network-based version of the Spectre Variant 1 (bounds check bypass, CVE-2017-5753) flaw first publicised earlier this year.
Slow = doesn’t matter so much, but yeah, just reading about Netspectre now.
This will be interesting. Need to insert random jitter into the network it seems 
Despite Google’s own Project Zero being part of the discovery team for the Meltdown and Spectre vulnerabilities, Google itself wasn’t notified until 45 days after the initial report was sent to Intel, AMD and ARM.
Turns out when it comes to communication they all suck equally.
it just keeps coming out left right and centre.
Those seem to be new things and not part of the spectre or even spectre NG family.
Would you mind making a new topic about it?
Done 
oh intel 
(yes, another link re: the above).
So glad i went AMD this time.
It’s probably been said to death in this thread already and I will pretend I read all that and concur:
These are entire classes of bugs that just started being discovered. Don’t expect it to end any time soon. These systems are fundamentally flawed in principle. And they’re going to keep making them that way, because they don’t have a choice right now.
Well, in this case it was an intel optimisation decision: access resource prior to checking access rights (sure, it’s faster, but incredibly stupid and short sighted IMHO and proving to be so now).
AMD didn’t do that. Yes, spectre is across the board, but these meltdown style attacks (such as Meltdown, Foreshadow, etc.) are intel specific.
edit:
Foreshadow is directly related to the same root cause as meltdown…
I’m guessing the would rather have the optimization in hardware and disable it in software to satisfy the customers who are more worried about performance than security. It probably is an unattractive task to re-implement everything they’ve been building on top of this foundation for the past checks tree rings scratch that, I guess they may have bit that bullet already 
From the Ars article:
Longer term, Intel promises to fix the issue in hardware. Cascade Lake processors, due to ship later this year, will not suffer the L1TF (or Meltdown) issues at all, suggesting that the new processors will change how they handle the permission checks to prevent speculative execution from running ahead of permissions checks.
Will be interested to see how this impacts their “IPC advantage” vs. AMD.
AMD never did this stuff, and sure, its an optimisation… but at the cost of “doing it wrong”…
edit:
already the 2700x and 8700k are pretty close in terms of IPC, its just clocks now…
Intel is now issuing a gag order to their CUSTOMERS from posting performance numbers before and after microcode updates in their microcode updater 'terms of service."
Oh. My. God.
Linus Torvalds would take this to court. (And HE BETTER) Heck, remove/takedown the damn intel-microcode packages in protest. Out of anyone, he WILL publish the numbers anyways, cause Intel’s damage control to Meltdown has been a disaster so far.
Lol they think they can tell the internet not to do something.
First thread with the results gets pinned
So I should download the phoronix test suite and do something about this?
Is the 8750H affect by this?
The list of CPUs not affected is shorter.
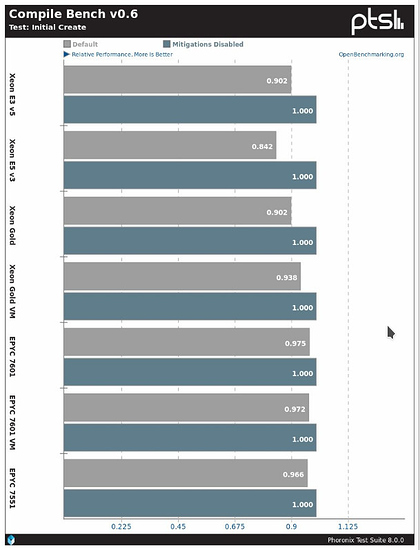
https://www.phoronix.com/scan.php?page=article&item=linux-419-mitigations&num=2
So it would seem that all the patches can make a significant difference in performance in some workloads on Intel CPUs. On one of the benchmarks there is a 21% difference!
It will be interesting to see how all of this pans out in the years come, for both Intel and AMD.
My speculation is that Intel will take a small hit in the consumer space, and potentially a major hit in the enterprise. I think those speccing new systems for enterprise will at least now consider AMD over intel, due not only to security vulnerabilities, but to cost and performance as well.
Hopefully Intel fixes this in architecture sooner rather than later. This is no easy task. Competition is good for the market, and I want that to continue.
That’s the thing. Who trusts first gen tech…Intel is fucking up time and time again fixing this in software. Who will trust the hardware fix ?