Maybe its just me, but i totally lost track at this really.
It looks like a pretty mess to me.
When they put it like that, bit of a glaring security hole really.
with what i have seen its just a blazing dumpster fire. intel is adding fuel to there dumpster fire by the truck load. and AMD seems to be putting there fire out with a squirt gun but it is going out.
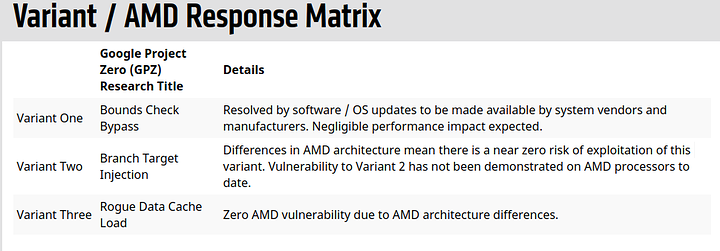
AMD seem to be playing it close to there chest. Looking at their response. Only variant two is the near zero thing i’ve seen tossed around on the web. Everyone’s like we want zero!
But if it “aint broke dont fix it” kind of applies when they cant find a hack that would affect them. Not to say over the next year everyone and their code monkey won’t be looking for holes. Then they can address it.
in all honesty the hole is there its just damn hard to hit and get right. they know how to do it and they know that if others in the wild could easily do it with out knowing the secret sauce that AMD knows then they would have to address it. but as it stands they “think” they are in the clear as it would technically be a variant 2 b for it to hit them where it hurts.
In security, there is no such thing as “near zero”. You are either vulnerable or you are not. This “near zero” talk is just corporate BS from AMD and is not getting them any friends.

I would say it has a huge impact when getting hit but it is very unlikely to get hit. So “near zero” risk in total is inaccurate, but for describing the likelyhood of an attack, it is okay.
Sure, there are grades in Hell after all. Until there is a proper Severity Rating (CVSS etc) this “near zero” is just corporate BS from AMD.
Mark Papermaster clarified this week that they are vulnerable to Spectre, finally and end to the corporate BS.
That’s what they said from the start tho. Just that it is very unlikely. That’s all they ever said with the “near zero”. They didn’t say they were immune.
Sorry, but this stance really makes no sense whatsoever. Categorical differences in likelihood and severity do matter, and throwing away all information in favor of a unidimensional yes/no assessment is much more misleading when it comes to ‘security’ than is talking about ‘near-zero’ wrt threats. Your stance comes down to saying that leaving all the doors to Fort Knox unlocked is equally as insecure “from a security standpoint” as is leaving Fort Knox unprotected against robbery via transporters.
I am very happy that the rig I built a few months ago is AMD!
I’m with @Pholostan on this, it is a yes or no thing. AMD can then clarify how extremely unlikely it is to be burned by this in length afterwards but they should be upfront about it’s existence first. It is nowhere near the level of BS Intel has put out but still.
I agree 100% computers are either 0 or 1. It is there or it isn’t.
Then what is the problem with AMD’s original press release that it needed amendation?
They said from the start “non-zero”, i.e., “one”, using ‘you either win or lose the lottery, so it’s 50/50 every time you buy a ticket’-logic.
The implication that it isn’t a problem. As an example: “near zero” (actual AMD quote) and
sounds about equal but implies very different things.
That is not upfront, that is PR.
My Sandybridge-E now bluescreens offten.
Clock_Watchdog_timeout
Near Zero = I Dont Know.
Not a definate no, but not a proven yes.
And could be both.
works then doesn’t the next time. like an intermittent fault
From a BIOS update? I guess that is more a windows thing?
Yep Windows update, had SNAFU it