Google Transparency Report now considers Looking Glass homepage as “containing harmful programs”
Hope this can get resolved
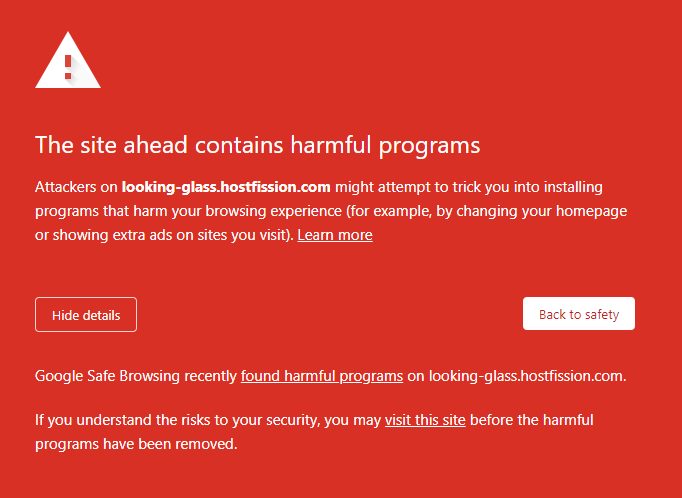
Google Transparency Report now considers Looking Glass homepage as “containing harmful programs”
Hope this can get resolved

I get the same, searching looking glass from Firefox with DDG, or from the direct link from the project page.
I trust the project, so don’t mind.
I guess new users may be put off.
shouting at @gnif on the off chance he is not aware. But I am not worried
Thanks but yes I am aware. Google through their stupidity have not just blocked the subdomain but also my primary domain name. I have been forced to purchace a domain for LG to get it away from my primary domain.
FWIW: The site is flagged on the host binary on the downloads page, which is a false positive. I have been contacted by a LG user at MSFT who is looking into why it’s getting flagged.
Hi, I just noticed the flagging as well. While the Google warning is phrased as if this is about PUA, the AV false positives are about trojan characteristics.
Someone on IRC told me that you have since discussed this more on Discourse (a service I am not going to use - they prohibit its use with alternative/open source clients), and that
[…] what seems to be triggering is service.c as it is using elevated access and keyboard/mouse hooks (typical of keyloggers etc.)
This person also told me that you have succeeded at getting whitelisted by AVG and Avast (and that it took much effort).
Still, many of the other FP’s remain (being a new user on L1T forums, I am unable to link to them, but you can search the binary checksums on VirusTotal dot com and Hybrid-Analysis dot com websites, as well as site listings at URLVoid dot com):
dba3c11aec119f6bab63f2baacc6b316e9bdd3208067fba808b169294058f05f
3eb537c2d76a2a94a26b42d50cb9cbf021e07814ec867e575a29f7881c49549a
I just contacted the Google Safe Browsing team about this, requesting a manual review of looking-glass dot io (hope that’s ok):
We are aware of several FP reports for downloads hosted at this site:
[VirusTotal URLs, same as above]Presumably, those are what triggered this site to be listed by you. We believe, however, even after repeat review, that NONE of the binaries hosted are malicious, or have been modified by a third party. Source code is available for further analysis: [@gnif’s LookingGlass Git repository at GitHub ]
Please kindly review the listing, since we believe it must be incorrect. If you can provide more information on what triggered the listing, or how we can prevent it from happening in the future, please notify us. The software developer, and website host, [@gnif’s real name was here], can be contacted as indicated at [hostfission dot com contact form] (see also links on page footer for more options).
Thanks for the support mate however at this point the only real solution is to code sign the binaries… I have ordered a singing cert however it will be a while before it arrives. At this point there is little more that we can do about this.
If this issue persists for too long I will start putting the host binaries inside password protected zip files where the password is posted along side it. This will prevent google’s automated virus scanner from being able to scan these files.
Sure, code signing will help, so will whitelisting with the relevant AV and ‘website reputation’ data providers. The current website reputation false positives may or may not go away after you start code signing releases. Which is why I also requested whitelisting the site at Fortinet, Bitdefender and Scumware.
Thank you kindly, it is appreciated. The larger issue is the vendors just keep whitelisting based on checksum and we do bleeding edge builds, sometimes several per day. These will have new checksums and will not get whitelisted.
You’re very welcome. And while we’re at it, thank you very much for developing and maintaining this software, and making its source code available under a nice license, too.
On the topic, in my experience, at least some of the ‘threat intelligence data providers’ will list based on multiple factors (if still too few, and moreover, too few which actually make sense to make them useful).
For now Fortinet has removed the site blacklisting. I assume this is also a fully automated process upon receipt of a manual submission challenging new listings, with a manual review taking place next week.
You’re most welcome. I would be chasing down all the AV vendors if time permitted, dealing with AVG/Avast the last week really took the drive out of me 
Just as a by the way, this is Discourse. It is the forum software the powers these forums.
That’s what I meant to write, Discord (not Discourse) - thanks for pointing this out, @Zibob, for offering a correction, @Netboy3, and sorry for the confusion. 
I just reviewed the URL blacklists.
Google’s manual review seems to have taken place (record last updated today), but instead of removing it, they just updated the listing categories. Their preferred approach to report false positives is through their webmaster / developer tools (which is free but requires a Google account). Since Google Safe Browsing is the most relevant of the remaining listings I would recommend registering for it and requesting de-listing there again.
This will still be needed (for the URL blacklists) after you start code signing the binaries (so could as well do it now).
Done dozens of times… Yesterday I put passwords on all the archives to try to to stop this. To make matters worse though google have decided that hostfission.com (my domain) is harmful yet again simply because I have 301 redirects from looking-glass.hostfission.com to the new site.
Hmm. Does this mean that including a build of the ivshmem driver in the windows host installer is a possibility now?
I just hit you up on PayPal to contribute for the .io purchase.
I haven’t used LG yet, but appreciate all the work just the same!