We care about privacy here on this forum. Though we lack a simple way to harden firefox without going through a complicated series of steps.
Well @MisteryAngel first mentioned it. So instead of making some elaborate guide how about we start with something called user.js. Its located in /home/USRNAME/.mozilla/random.default.
This is a very easy way to set preferences before you even start firefox. I have gone ahead and donated my user.js to the cause. Remember how you used to have to set all those in about:config . Yeah lets just skip over that and batch set it by creating a file.
If you are going to copy my user.js DO NOT do it while firefox is open. Close firefox, create the file, open firefox. The settings should all be good to go!
User.js commented (no comments in actual file)
// Heimdallr -- Added -- Privacy Enhanced
// Disable Telemetry
user_pref("browser.urlbar.trimURLs","false");
user_pref("browser.newtabpage.activity-stream.feeds.telemetry browser.newtabpage.activity-stream.telemetry","false");
user_pref("browser.pingcentre.telemetry","false");
user_pref("devtools.onboarding.telemetry-logged","false");
user_pref("media.wmf.deblacklisting-for-telemetry-in-gpu-process","false");
user_pref("toolkit.telemetry.archive.enabled","false");
user_pref("toolkit.telemetry.bhrping.enabled","false");
user_pref("toolkit.telemetry.firstshutdownping.enabled","false");
user_pref("toolkit.telemetry.hybridcontent.enabled","false");
user_pref("toolkit.telemetry.newprofileping.enabled","false");
user_pref("toolkit.telemetry.unified","false");
user_pref("toolkit.telemetry.updateping.enabled","false");
user_pref("toolkit.telemetry.shutdownpingsender.enabled","false");
// Disable Plugin Scanning
user_pref("plugin.scan.plid.all","false");
// Disable Geolocation
user_pref("geo.enabled","false");
// Disable all disk caching PERIOD
user_pref("browser.cache.disk.enable","false");
user_pref("browser.cache.disk_cache_ssl","false");
user_pref("browser.cache.memory.enable","false");
user_pref("browser.cache.offline.enable","false");
user_pref("browser.cache.insecure.enable","false");
// Disable formfill
user_pref("browser.formfill.enable","false");
// Disable Zero Round Trip Time Resumption
user_pref("security.tls.enable_0rtt_data","false");
// Use only TLS 1.2 and 1.3
user_pref("security.tls.version.min","3");
// Disable Triple DES cipher
user_pref("security.ssl3.rsa_des_ede3_sha","false");
// Use strongest cipher
user_pref("security.ssl3.dhe_rsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_gcm_sha256", false);
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_gcm_sha256", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_sha", false);
user_pref("security.ssl3.rsa_aes_128_sha", false);
// Evade Finger printing
user_pref("privacy.resistfingerprinting","true");
// Disable the HORRIBLE webRTC
user_pref("media.peerconnection.enabled","false");
// Disable Prefetching
user_pref("network.dns.disablePrefetch","true");
user_pref("network.prefetch-next","false");
// Disable Referrer Headers (WHY is this is a thing)
user_pref("network.http.sendRefererHeader","0");
// Disable direct GPU access (WEBGL)
user_pref("webgl.disabled","true");
// Disable battery life check
user_pref("dom.battery.enabled","false");
// Disable session identifier
user_pref("security.ssl.disable_session_identifiers","true")
// Make requests only to site being visited
user_pref("privacy.firstparty.isolate","true")
// Disable auth fast starts
user_pref("security.ssl.enable_false_start","false")
// Disable new tab privacy concerns
user_pref("accessibility.force_disabled", 1);
user_pref("browser.newtabpage.activity-stream.asrouter.userprefs.cfr.addons", false);
user_pref("browser.newtabpage.activity-stream.asrouter.userprefs.cfr.features", false);
user_pref("browser.newtabpage.activity-stream.feeds.section.highlights", false);
user_pref("browser.newtabpage.activity-stream.feeds.section.topstories", false);
user_pref("browser.newtabpage.activity-stream.feeds.section.topstories.rec.impressions", "{\"50465\":1576448311544,\"50504\":1576448311544,\"50513\":1576448311544}");
user_pref("browser.newtabpage.activity-stream.feeds.section.topstories.spoc.impressions", "{\"2323\":[1576448311615,1576448311641,1576448317243]}");
user_pref("browser.newtabpage.activity-stream.feeds.snippets", false);
user_pref("browser.newtabpage.activity-stream.feeds.topsites", false);
user_pref("browser.newtabpage.activity-stream.impressionId", "{bc349b2a-4696-4afa-bf4f-48d1fd919fe0}");
user_pref("browser.newtabpage.activity-stream.improvesearch.topSiteSearchShortcuts.havePinned", "google,amazon");
user_pref("browser.newtabpage.activity-stream.prerender", false);
user_pref("browser.newtabpage.activity-stream.section.highlights.includeBookmarks", false);
user_pref("browser.newtabpage.activity-stream.section.highlights.includeDownloads", false);
user_pref("browser.newtabpage.activity-stream.section.highlights.includePocket", false);
user_pref("browser.newtabpage.activity-stream.section.highlights.includeVisited", false);
user_pref("browser.newtabpage.activity-stream.showSearch", false);
user_pref("browser.newtabpage.activity-stream.showSponsored", false);
user_pref("browser.newtabpage.enabled", false);
user_pref("browser.newtabpage.storageVersion", 1);
// Disable spell check and enable clear on shutdown
user_pref("layout.spellcheckDefault", 0);
user_pref("network.cookie.cookieBehavior", 4);
user_pref("network.cookie.lifetimePolicy", 2);
user_pref("network.http.speculative-parallel-limit", 0);
user_pref("network.trr.mode", 2);
user_pref("pdfjs.enabledCache.state", true);
user_pref("pdfjs.migrationVersion", 2);
// Correct Permissions
user_pref("permissions.default.camera", 2);
user_pref("permissions.default.desktop-notification", 2);
user_pref("permissions.default.geo", 2);
user_pref("permissions.default.microphone", 2);
// Enable privacy sanitization and disable PDF full page
user_pref("plugin.disable_full_page_plugin_for_types", "application/pdf");
user_pref("pref.privacy.disable_button.cookie_exceptions", false);
user_pref("privacy.clearOnShutdown.downloads", false);
user_pref("privacy.clearOnShutdown.formdata", false);
user_pref("privacy.clearOnShutdown.history", false);
user_pref("privacy.clearOnShutdown.offlineApps", true);
user_pref("privacy.clearOnShutdown.sessions", false);
user_pref("privacy.clearOnShutdown.siteSettings", true);
user_pref("privacy.donottrackheader.enabled", true);
user_pref("privacy.history.custom", true);
user_pref("privacy.sanitize.pending", "[]");
user_pref("privacy.sanitize.sanitizeOnShutdown", true);
user_pref("privacy.trackingprotection.cryptomining.enabled", true);
user_pref("privacy.trackingprotection.enabled", true);
user_pref("privacy.trackingprotection.fingerprinting.enabled", true);
user_pref("toolkit.telemetry.reportingpolicy.firstRun", false);
user_pref("trailhead.firstrun.didSeeAboutWelcome", true);
Android Users Location:
You will find it in internal storage. You should not need root to modify it. If you do, you are in the wrong location.
/data/data/org.mozilla.firefox/files/mozilla/xxxxxxxx.default/
Simple as that create the user.js there and if it doesnt set, modify prefs.js after force closing firefox and put it in there. That should make sure the values stick! Also if this isnt the case like on a hardened lineage OS or graphene OS… See this guide to do so:
https://github.com/ghacksuserjs/ghacks-user.js/wiki/1.6-Firefox-Android
This will disable a WHOLE ton of features one largely doesnt need to browse the web. It does remove convenience but it doesnt BREAK the web.
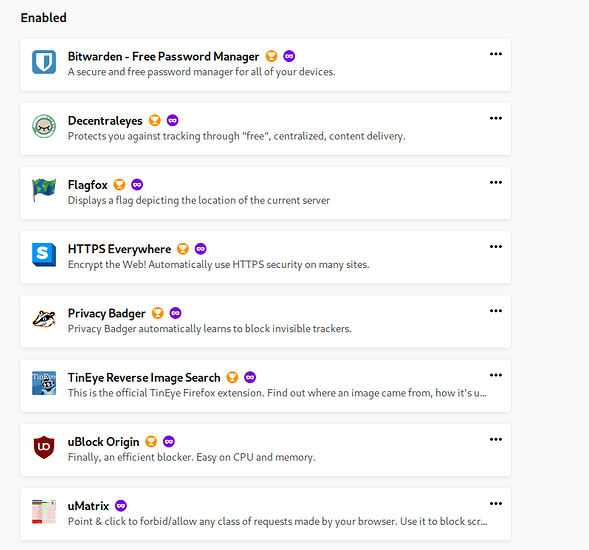
Extensions I have running:
Configure them as you want but this is what I have found works for me and doesnt out right break the web. Excluding uMatrix (YMMV configure as you go).
Decentraleyes:
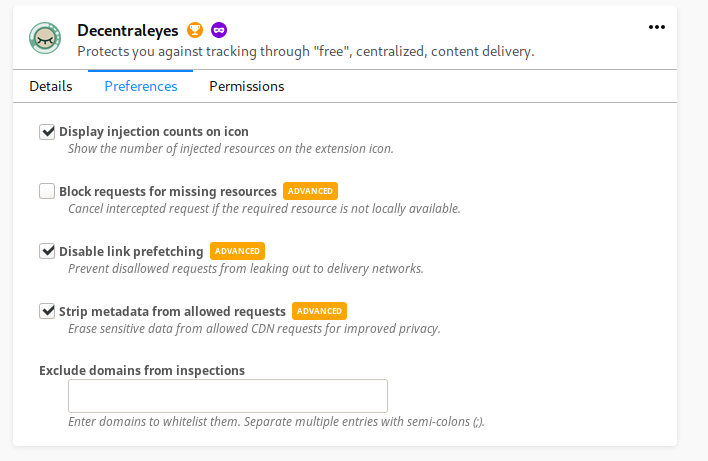
Blocking requests for non locals breaks all streaming services.
HTTPS Everywhere is good on defaults
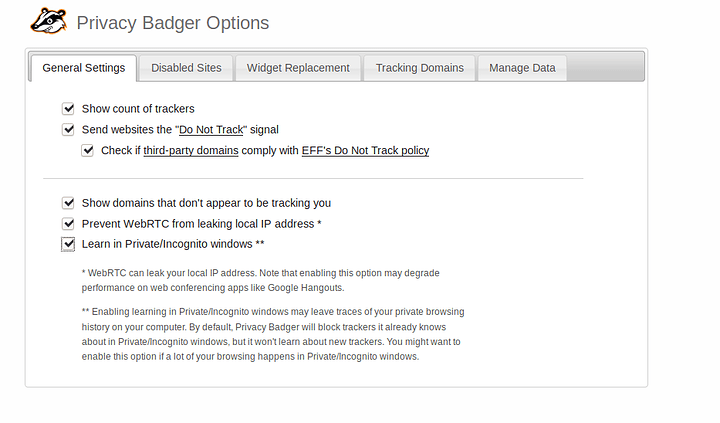
Privacy Badger
I would recommend checking the lower three options
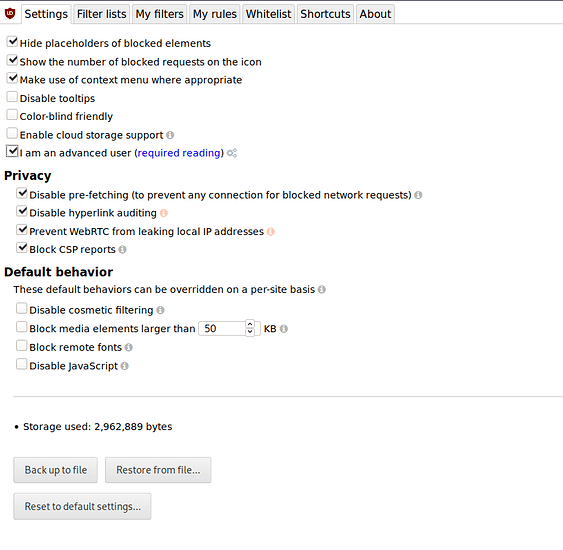
uBlock
Dont enable block remote fonts. I know theres a fingerprinting chance but for the love of god it breaks too much stuff
Filters, I just enable all of them except languages and countries I dont visit websites of. Im down to hear others. If there are filters missing from the lists you think are useful, please dont hesitate to throw them in below
FlagFox and TinyEye are great and pose no real risk.
Other than that this is all I do. You dont need much more. Also you can set all of these on android as well. Same way
Proof it took
about:support
See user.js section and modified values