Hello everyone,
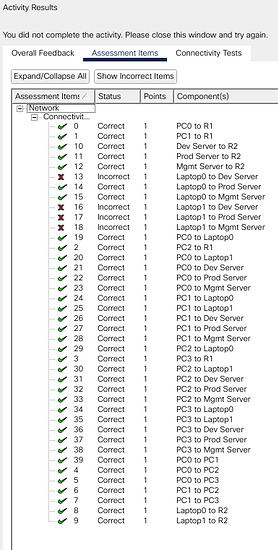
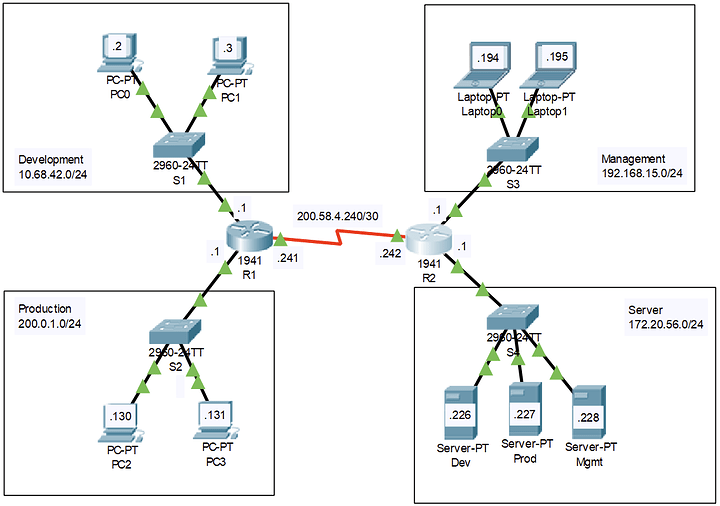
I am currently in my Network Security and Firewalls class at my local college and am working in a Cisco environment (More specifically Packet Tracer 8.0). I believe I have successfully cleared the Packet Tracer activity I was given but PT doesn’t seem to acknowledge this for some reason. When I check the activity it tells me that I have not met 4 objective items and fail 3 connectivity checks.

However, when I perform pings between these devices to verify the connections manually they are correct. (example: I can’t ping anything on the 172 network with Laptop1 even though PT tells me that it is successfully pinging) If anyone has any suggestions or wants to double check my work here are my running configs on the routers.
Packet Tracer (Just delete the .txt at the end) Access List Activity 3.pka.txt (561.9 KB)
Router #1
Current configuration : 992 bytes
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
hostname Router
no ip cef
no ipv6 cef
license udi pid CISCO1941/K9 sn FTX1524VC0B-
spanning-tree mode pvst
interface GigabitEthernet0/0
ip address 10.68.42.1 255.0.0.0
ip access-group PC0Rule in
duplex auto
speed auto
interface GigabitEthernet0/1
ip address 200.0.1.1 255.255.255.0
duplex auto
speed auto
interface Serial0/0/0
ip address 200.58.4.241 255.255.255.252
clock rate 2000000
interface Serial0/0/1
no ip address
clock rate 2000000
shutdown
interface Vlan1
no ip address
shutdown
ip classless
ip route 172.20.56.0 255.255.255.0 200.58.4.242
ip route 192.168.15.0 255.255.255.0 200.58.4.242
ip flow-export version 9
ip access-list standard PC0Rule
deny host 10.68.42.2
permit any
no cdp run
line con 0
line aux 0
line vty 0 4
login
end
Router #2
Current configuration : 1079 bytes
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
hostname Router
no ip cef
no ipv6 cef
license udi pid CISCO1941/K9 sn FTX1524AHM3-
spanning-tree mode pvst
interface GigabitEthernet0/0
ip address 192.168.15.1 255.255.255.0
ip access-group ManagementACL out
duplex auto
speed auto
interface GigabitEthernet0/1
ip address 172.20.56.1 255.255.0.0
ip access-group ServerACL out
duplex auto
speed auto
interface Serial0/0/0
ip address 200.58.4.242 255.255.255.252
interface Serial0/0/1
no ip address
clock rate 2000000
shutdown
interface Vlan1
no ip address
shutdown
ip classless
ip route 200.0.1.0 255.255.255.0 200.58.4.240
ip flow-export version 9
ip access-list standard ServerACL
permit host 200.0.1.131
permit host 192.168.15.194
ip access-list standard ManagementACL
permit host 200.0.1.130
permit 172.20.0.0 0.0.255.255
no cdp run
line con 0
line aux 0
line vty 0 4
login
end
Thanks for the help and if you want to check my config in Packet Tracer here is a config script to set up the routers the same way I did so that way you can follow my process.
iOS Script.txt (1.0 KB)
##Access List 3 Router Configurations
##R1 Config Script
enable
conf t
interface g0/0
ip address 10.68.42.1 255.0.0.0
no shut
interface g0/1
ip address 200.0.1.1 255.255.255.0
no shut
interface s0/0/0
ip address 200.58.4.241 255.255.255.252
no shut
exit
ip route 172.20.56.0 255.255.255.0 200.58.4.242
ip route 192.168.15.0 255.255.255.0 200.58.4.242
ip access-list standard PC0Rule
deny 10.68.42.2 0.0.0.0
permit any
exit
interface g0/0
ip access-group PC0Rule in
##R2 Config Script
enable
conf t
interface g0/0
ip address 192.168.15.1 255.255.255.0
no shut
interface g0/1
ip address 172.20.56.1 255.255.0.0
no shut
interface s0/0/0
ip address 200.58.4.242 255.255.255.252
no shut
exit
ip route 200.0.1.0 255.255.255.0 200.58.4.241
ip access-list standard ManagementACL
Permit 200.0.1.130 0.0.0.0
Permit 172.20.0.0 0.0.255.255
exit
ip access-list standard ServerACL
Permit 200.0.1.131 0.0.0.0
Permit 192.168.15.194 0.0.0.0
exit
interface g0/0
ip access-group ManagementACL out
interface g0/1
ip access-group ServerACL out