Browsing the modern web can be a pain between all the ads, trackers, popups, nagging and general garbage. This thread is to be bit of a brain dump / link dump, and comparison of browsers and configurations to maximize privacy, security, and control. Mostly focused on browsers and browser configuration, but I may meander into OS’s and FOSS alternatives.
While Tor is a cool piece of tech and a great tool, generally it’s not very practical for normal every day browsing. This is because a lot of sites simply refuse to work when detecting that its been accessed through TOR, maybe your ISP/country tries to block it, and it’s generally slower to load regular clear web.
There’s a new kid on the block called Mullvad browser that looks interesting. It seems to come with pretty sensible defaults and is marketed as “Tor Browser without the Tor Network”. There are also many privacy focused forks like PaleMoon, WaterFox, and LibreWolf, but I have not experimented with them much and this first post will be focused on stock Firefox to get an understanding of what’s under the hood.
Brave is a good alternative to Chrome, but again this first post will be focused on Firefox because Chrome has too much market share and google is destroying the web.
VPN’s while useful are simply moving trust from ISP to VPN provider, and will be outside the scope of this thread. Also goal here is not evasion of state-sponsored actors or extreme paranoia, but making the web a little more bearable to navigate and to take back control.
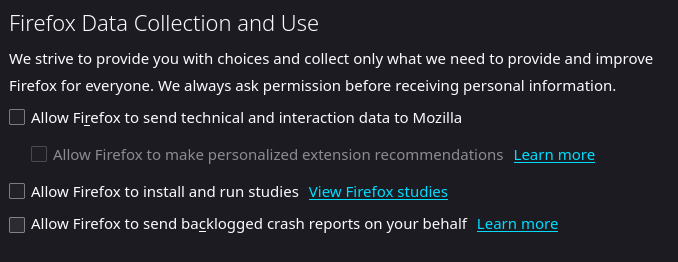
A very simple setup is to just install uBlock Origin with Firefox. This is an easy win and when setting up Grandma’s computer I simply do this and call it a day. However, Mozilla has been adding more telemetry over the years and injecting homepage Ads via proprietary services such as Pocket. As well as Opt-In by default experiments/studies that in some case has violated user privacy, and DOES NOT NOTIFY THE USER when being tested.
Goto: about:preferences#privacy > Firefox Data Collection and Use > UNCHECK: ‘Allow Firefox to install and run studies’
Do Not Track signal (consider this setting to be useless when many sites do not respect this flag). EDIT: Leave this flag OFF as it can be a unique signal used to fingerprint as pointed out by @LiKenun (thanks)
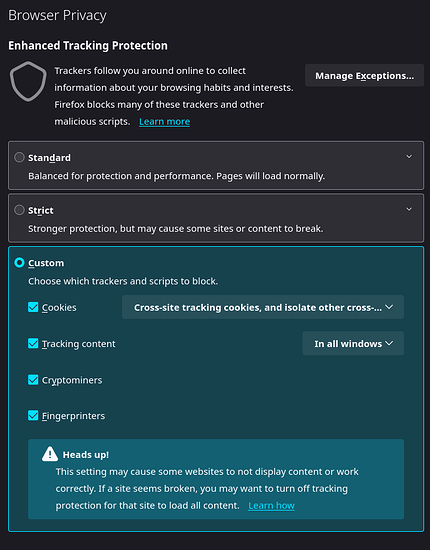
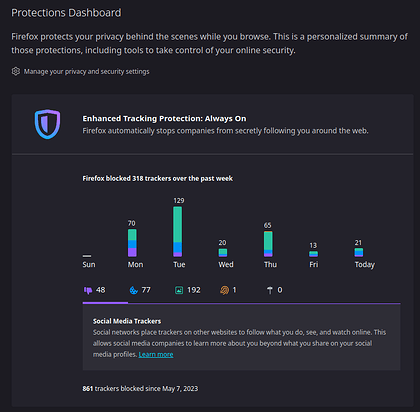
Firefox has some built-in ‘Enhanced Tracking Protection’. You can view it’s performance via about:protections
While there are built in settings for some of this stuff, it’s not complete and many settings are abstracted away from the user. Enter about:config
Disable and hide Pocket:
extensions.pocket.showHome = false
browser.newtabpage.activity-stream.section.highlights.includePocket = false
browser.newtabpage.activity-stream.discoverystream.sendToPocket.enabled = false
browser.newtabpage.activity-stream.discoverystream.saveToPocketCard.enabled = false
extensions.pocket.refresh.emailButton.enabled = false (default)
extensions.pocket.api = blank
extensions.pocket.site = blank
extensions.pocket.bffApi = blank
extensions.pocket.oAuthConsumerKey = blank
extensions.pocket.oAuthConsumerKeyBff = blank
Disable Studies/Experiments:
extensions.experiments.enabled = false (default)
app.shield.optoutstudies.enabled = false
Slightly confusing wording, you might expect true to opt-out but in this case it refers to the ‘Allow Firefox to install and run studies’ check box itself. see: app.sheild.optoutstudies.enabled · Issue #386 · pyllyukko/user.js · GitHub
Do NOT send ‘Do Not Track’ header:
privacy.donottrackheader.enabled = false (default)
Enable tracking protection (Security/Tracking protection - MozillaWiki):
privacy.fingerprintingProtection = true
privacy.socialtracking.block_cookies.enabled = true (default)
privacy.trackingprotection.enabled = true
privacy.trackingprotection.fingerprinting.enabled = true (default)
privacy.trackingprotection.cryptomining.enabled = true (default)
HTTPS only:
dom.security.https_only_mode_ever_enabled = true
Disable Geolocation (If you require Geolocation, consider changing provider to one that respects the user):
geo.enabled = false
geo.provider.use_geoclue = false
geo.provider.network.url = blank
Disable prefetch. Link prefetching is a browser mechanism, which utilizes browser idle time to download or prefetch documents that the user might visit in the near future:
network.prefetch-next = false
network.predictor.enable-prefetch = false (default)
network.dns.disablePrefetch = true
network.dns.disablePrefetchFromHTTPS = true (default)
Disable Browser.send pings:
This attribute contains one or more URIs to “ping” (send a POST request to) when the user clicks the link. The attribute would be useful for letting websites track visitors’ clicks. Used to default on, seems to default off now.
browser.send_pings = false (default)
Display the “raw” punycode version of internationalized domain names. Help protect from ‘character spoofing’ with fancy unicode eg: аррӏе.com → аррӏе.com
see: IDN homograph attacks Phishing with Unicode Domains - Xudong Zheng
network.IDN_show_punycode = true
Disable sites reading battery level:
dom.battery.enabled = false
Disable Telemetry (take note of the ever growing size of this list…):
browser.newtabpage.activity-stream.feeds.telemetry = false
browser.newtabpage.activity-stream.telemetry = false
browser.newtabpage.activity-stream.telemetry.structuredIngestion.endpoint = blank
browser.newtabpage.activity-stream.telemetry.ut.events = false (default)
browser.ping-centre.telemetry = false
browser.search.serpEventTelemetry.enabled = false (default)
browser.urlbar.eventTelemetry.enabled = false (default)
dom.security.unexpected_system_load_telemetry_enabled = false
network.trr.confirmation_telemetry_enabled = false
security.app_menu.recordEventTelemetry = false
security.certerrors.recordEventTelemetry = false
security.identitypopup.recordEventTelemetry = false
security.protectionspopup.recordEventTelemetry = false
toolkit.telemetry.archive.enabled = false
toolkit.telemetry.bhrPing.enabled = false
toolkit.telemetry.cachedClientID = blank
toolkit.telemetry.dap_enabled = false (default)
toolkit.telemetry.dap_helper = blank
toolkit.telemetry.dap_leader = blank
toolkit.telemetry.enabled = false
toolkit.telemetry.firstShutdownPing.enabled = false
toolkit.telemetry.newProfilePing.enabled = false
toolkit.telemetry.pioneer-new-studies-available = false
toolkit.telemetry.server = blank
toolkit.telemetry.shutdownPingSender.backgroundtask.enabled = false (default)
toolkit.telemetry.shutdownPingSender.enabled = false
toolkit.telemetry.shutdownPingSender.enabledFirstSession = false (default)
toolkit.telemetry.testing.overrideProductsCheck = false (default)
toolkit.telemetry.unified = false
toolkit.telemetry.updatePing.enabled = false
Spoof HTTP referer (send the target URL as the referrer):
network.http.referer.spoofSource = true
NOTE: You can disable referer header via …header = 0, however this breaks too many sites to be practical. Recommend leave default 2 and turn spoof on. Security/Referrer - MozillaWiki
network.http.sendRefererHeader =
0 = never send the header
1 = send the header only when clicking on links and similar elements
2 = (default) send on all requests (e.g. images, links, etc.)
Diable WebRTC. Websockets can leak IP when using a VPN:
network.http.http2.websockets = false
NOTE: these settings may be overwritten when firefox updates, so keep an eye on it from time to time. (Blanking out api URL’s and API keys is probably overkill but I personally like to nuke them and don’t trust these setting not to flip back on during an update, or if I miss one it’s sink-holed to nowhere…)
See: Category:Security and privacy-related preferences - MozillaZine Knowledge Base
And: Category:Preferences - MozillaZine Knowledge Base
If you don’t want to manually adjust these settings, this is a great resource but it’s highly aggressive and breaks many sites: GitHub - pyllyukko/user.js: user.js -- Firefox configuration hardening
NOTE: There is sometimes a trade off between security/privacy and functionality. Some of these settings will break certain websites. See ‘relaxed’ version that may be more practical for your use-case.
Once you have your config setup how you like you can keep a copy of your user.js backed up and simply drop it in your profile folder across machines:
Windows: %APPDATA%\Mozilla\Firefox\Profiles\<profile folder>
Linux: ~/.mozilla/firefox/<profile folder>
Mac: ~/Library/Application Support/Firefox/Profiles/<profile folder>
~/Library/Mozilla/Firefox/Profiles/<profile folder>
Or visit about:profiles
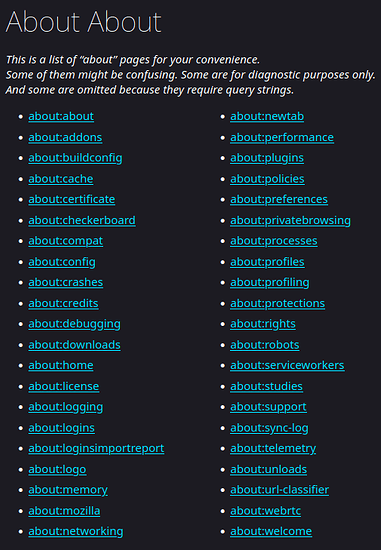
Many of you here are likely already familiar with about:config, but there are some other interesting built in about:things.
about:about
Master about. View most “about” pages, but even this is NOT all of them! “some are omitted because they require query strings”
about:profiles
Manage and view profiles. Features ‘Open directory’ button to link directly to profile storage.
about:studies
View active and completed studies/experiments. Do you want to know if you have already been part of, or are currently running any experiments (unbeknownst to you)?
about:telemetry
View Information collected by telemetry.
about:protections
Protection dashboard to view stats from ‘Enhanced Tracking Protection’.
about:networking
View and audit currently active connections.
Also see: Connections established on startup - Firefox - MozillaZine Knowledge Base
And: How to stop Firefox from making automatic connections | Firefox Help
about:processes
View currently running processes, memory and CPU usage. Modern browsers are multi-threaded (typically 1 thread per tab).
about:memory
Advanced memory profiler.
about:cache
Information about the Network Cache Storage Service.
about:webrtc
Web Real-Time Communications page. View and manage connections.
Privacy Enhancing Extensions
Beyond stock Firefox settings and into extension land!
Ublock Origin: block ads and tracking. widely regarded as the best blocker as some other adblockers are run by ad companies themselves or whitelist certain ads. do not confuse with non-Origin fork.
PrivacyBadger: algorithmic anti-tracking and anti “supercookies”.
HTTPSEverywhere: Force HTTPS, but now may be obsolete as there is a built in setting: about:preferences#privacy > Security > HTTPS-Only Mode > CHECK: ‘Enable HTTPS-Only Mode in all windows’
Decentraleyes: Local resource loading for common third-party Libraries (Google Hosted Libraries, Microsoft Ajax CDN, CDNJS (Cloudflare), jQuery CDN (MaxCDN), any many more), instead of downloading each visit.
NoScript: blacklist or whitelist every javascript resource. Enable only the necessary ones for site to function.
ResquestPolicy: similar to NoScript but more granular allowing you to whitelist/blacklist all cross-site requests down to every resource.
uMatrix: similar to RequestPolicy. maintained by same developer as uBlock Origin. block:
- cookies
- CSS-related resources (stylesheets and web fonts)
- images
- plugins
- scripts
- XHR (requests made by scripts)
- iFrames
If you like to get OCD with it you can hyper manage what is loaded and what is not via NoScript or ResquestPolicy/uMatrix. However in my experience after a couple years of manually whitelisting just enough things to get basic stuff to load I found this to be not so practical long-term. I still like these tools but the mental overhead is draining and the focus here is pragmatism over paranoia.
Mobile Browsers
iOS
Apple locks down webkit so all browsers are forced to use Safari under the hood so that even so it doesn’t matter what you use. It’s all Safari. There is no winning here. Jailbreaking/rooting is the only way around this, which comes with its own challenges and security implications.
Android
Firefox Mobile does support plugins like uBlock Origin and about:config settings such as dom.battery.enabled = false are relevant here (how about it’s none of your business what my battery level is creep…)
Brave is also available for Mobile.
Getting slightly off topic of browsers into into the OS itself, consider getting off OEM Android that came pre-installed on your phone because GFS (Google Services Framework) & GMS (Google Mobile Services) is a garbage that runs deep. GMS is known to report on you every 5-15 minutes and location services tracks whether you are standing or walking! edit: found source: https://digitalcontentnext.org/wp-content/uploads/2018/08/DCN-Google-Data-Collection-Paper.pdf
Consider alternative roms such as degoogled GrapheneOS, CalyxOS, LineageOS. XDA is a great resource here. Always pay attention to permissions and try to use websites instead of installing bloated unnecessary native apps where possible. Do you really need a dedicated app for XYZ, or will simply going to XYZ’s website suffice? It’s easier to sandbox a webapp as many native apps comes with unnecessary permissions and more aggressive and invasive tracking techniques.
Linux phones are on the horizon!
HTTP GET tracking
Another gotcha is tracking garbage shoved into the GET portion of URL’s.
The GET method is used to append additional data to a URL in the form of key-value pairs after the ? token. for example: example.com/form.php?key=value
This is used to encode what link you clicked or what your account ID is. eg:
- Amazon: .com/product-name/dp/XXXXXX/?blahblah (everything after ? is garbage)
- Spotify: ?SI=XXXXXXX&utm_source=copy-link (SI = Share ID)
Often if you use a website or apps Share feature, notice how it will inject an ID into the link you are about to send. I like to manually remove these before sending or using links.
Never save passwords in browser!
Autofill may be convenient but this is a common attack vector for stolen credentials as they are stored in your profiles folder in an EASILY DECRYPTED key4.db and logins.json format: Recovering important data from an old profile | Firefox Help
Lookup ‘browser credential stealer’ for plenty of examples. If you insist on using saved passwords, please use a ‘Master Password’.
Better yet just use a password manager such as KeepassXC.
Temporary Mail
Trying to download just one thing from some obscure forum you don’t actually want to make an account for? Try a temporary mail service. They run in your browser and are deleted after a few minutes.
PiHole
If you have a spare machine or raspberry-pi sitting around, why not consider turning it into a PiHole?
Ad services are often leveraged to distribute malware. Not to mention a waste of space and time so I feel absolutely zero guilt in blocking them.
References & Resources
Browser Comparison: https://privacytests.org
Privacy Guide tools: https://www.privacyguides.org/en/tools/#desktop-web-browsers
Fingerprint testing:
1: https://panopticlick.eff.org
2: https://browserleaks.com
3: https://amiunique.org
4: https://www.deviceinfo.me
NOTE: some of these settings and plugins will actually make you MORE UNIQUE in terms of Fingerprinting. There is a trade off between privacy and uniqueness. Evaluate for your self what you care about.
Web Assembly Test: https://wasm-feature-detect.surma.technology/
Also see BeEf (Browser Exploitation Framework) if you’re interested in exploring/exploiting this stuff in your own environment:
Feedback and corrections welcome. Share your experience and opinions on browsers, alternative forks, settings, and extensions.