I ran proxmox for about a day a few years ago when I really REALLY didn’t know jack so I should run it again to give it a fair shake. How do you feel about a nested instance just to get a taste instead of bare metal?
I tried to spin up a CentOS7 minimal ISO I’ve used many times. Found some interesting results.
Basically I have to use a tag-team combo of XCP-ng Center and Xen Orchestra to get the CPU and storage settings right.
- edit, interesting, xcp-ng always puts a chunk of hypervisor local memory into the VM, I have not been able to delete it during setup. Xen Orchestra gets it right.
I want to rock opensource, but I think I need something more mature- I say this but I’m not gingerly walking over and rebooting my box with the ESXi disks- I want Xen to work, I’m liking a lot about it.
I will have to do some kind of tag-team setup between both GUIs just to make a simple VM lol, but still, what a day to be alive, this is free.
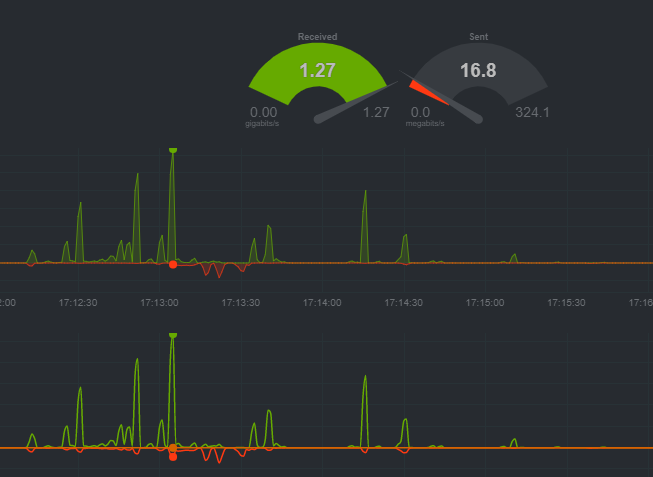
For fun I did an OBS screen capture of installing the same ISO on VMware workstation pro (i7 desktop, Samsung SSD) and on my type 1 (R710) with NFS as the storage. They were pretty much neck and neck. Workstation beat the type1, but narrowly. Pretty happy with that. I was really afraid of NFS but I guess its a concern only for legit datacenters. For home-labbers a twin 1G nic is probably enough to slum it, a quad better. I’ve been watching netdata on FreeNAS and there are small moments where it spikes to ~.60 to 1.27 gigabits but its very brief.
For those that want to get into this with spare parts, heck even a 1G connection should be fine, look at all the valley space vs. peaks. I’ll try to get another shot when I have the VM actually doing some work. I think something that graph won’t show is lag when I start to query from a DB on that VM. I’m going to have to feel it with the butt dyno as gear heads say- how the new build feels vs. when I had a similar build on SSDs on ESXi (local storage).
I couldn’t help it, this came to mind