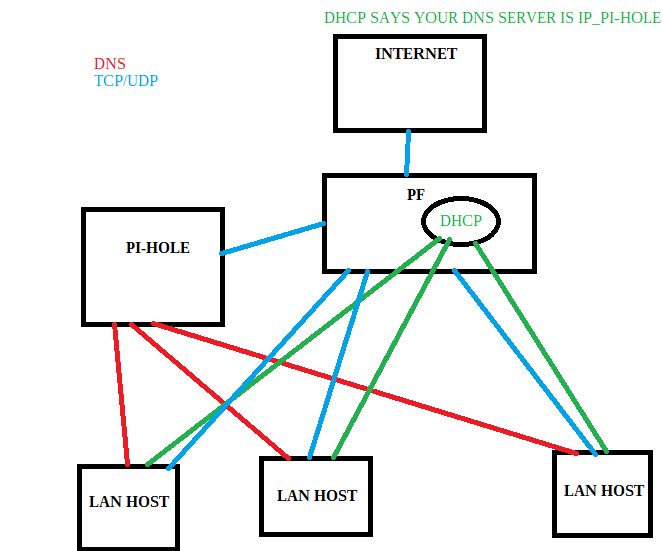
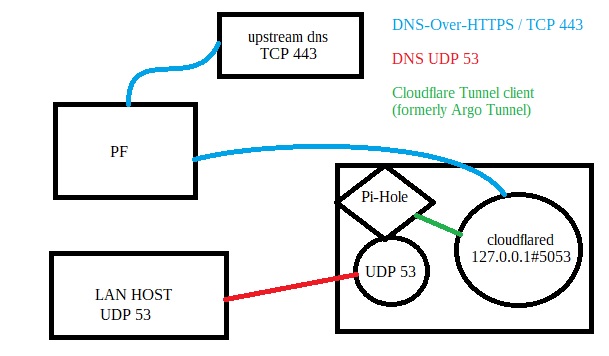
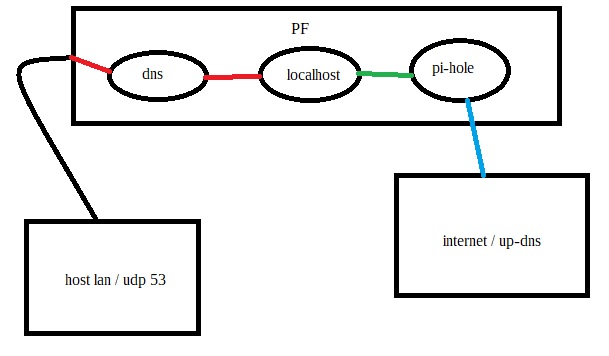
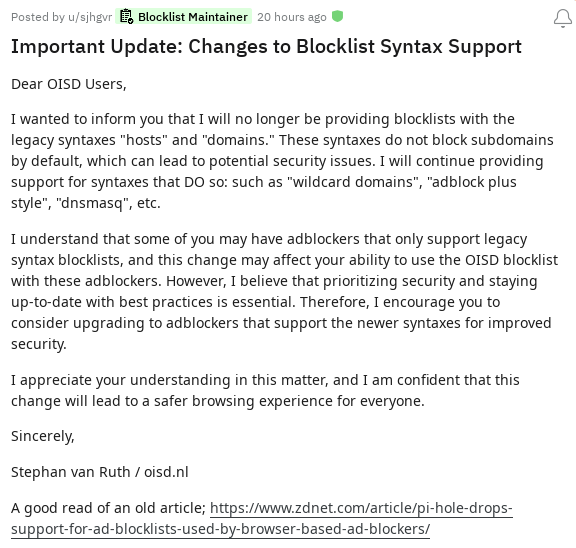
Generally speaking, PF should have no say in what pi-hole does and what it logs. Putting the pi-hole separately on a different IP and forcing the LAN hosts to use the host with the pi-hole and PF is out of the question.
All logs that can be collected here will be collected. And no special configuration on the PF side is needed.
All dns query traffic shouldn’t even brush up against a PF host.
Do you want to see something unusual in these logs? Pi-hole will only log dns queries and nothing else… Let PF log the rest of the situation in the network.
Above is a typical simple scheme of this solution.
My router has dhcp which tells hosts on lan your dns servers are xxx.xxx.xxx.xxx and xxx.xxx.xxx.xxx(pihole’s).
On the router I have completely blocked traffic for UDP 53 and I do not answer dns queries … that’s what dedicated dns servers (pihole) are for.
Hosts in the LAN have the settings that their dns servers are these specific piholes and they do not try to ask elsewhere, and even if they wanted to, I block them anyway 53.
My pi-holes use both Quad9 and Cloudflare for upstream DNS over HTTPS. As a result, all dns request traffic from LAN goes to updns encrypted. Of course still udp 53 locally.
In this model, pfsense or any other software has nothing to say. Router/Firewall never gets this traffic. All they know and see is DHCP broadcasting these specific dns(pi-hole) addresses and nothing else.
The actual traffic is between the hosts and the pi-hole machine.
However, as for the router itself and its local dns queries against the upstream. I also force my local pi-hole for the WAN interface. And in the pi-hole logs I can see the requests of the router itself, if there are any dns requests.
The end result is that whatever within my lan does a dns query, including the main router that has a WAN port to the world, I will see in the pi-hole logs that this particular IP has asked for this domain.
So in this configuration there should be no problem with log content in pi-hole. And pfsense itself and dhcp on it should absolutely not affect anything. ![]()
I don’t see a problem here… I must have missed something. ![]()