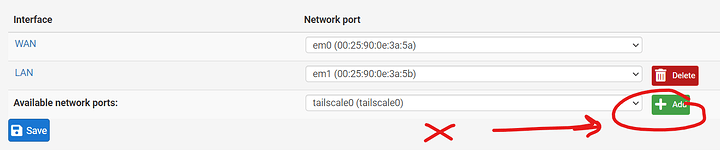
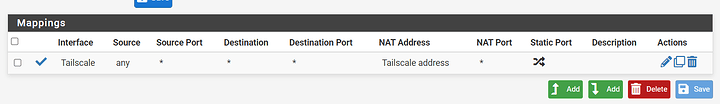
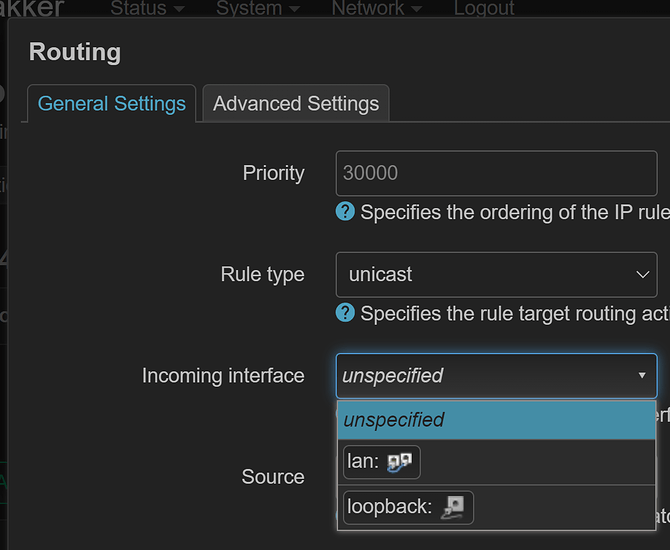
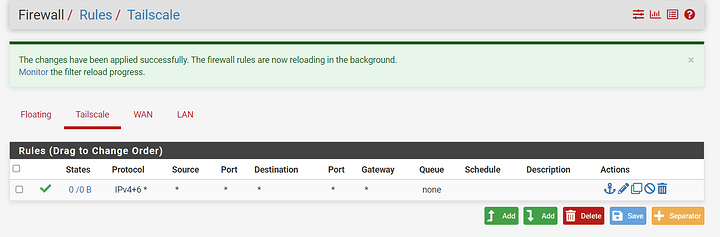
Solution: [SOLVED] Tailscale subnet router limited to only some devices? - #22 by Sawtaytoes
I want to set up a Tailscale subnet routed VPN at my parent’s house which targets only certain devices, so they can send all traffic through to my home network. These devices cannot install Tailscale clients.
By the time I implement this, they will have a UniFi router (same as I have), so there are gonna be some limitations.
I have no clue where to start.
- Any device subnetted on the Tailscale network needs to change its gateway to the Tailscale device.
- Somehow, this Tailscale host is either passing out IPs or routing between local IPs and the Tailscale network.
- I might need VLANs to ensure DHCP works properly from those devices to the Tailscale device. The UniFi router can handle DHCP on VLANs and even assign a custom gateway (pretty sure).
- To get VLANs working, I think I need managed switches. They have 1 managed switch, but they’d need more. Thankfully, I have a couple spare managed switches, but if I give them my spares, I won’t have any when I need them
 .
. - I’m not if if the Tailscale device would need 1 or 2 NICs. Can it be both on the VLAN and the main network’s subnet at the same time? That would simplify things.
- I’d need to assign specific devices to the VPN or to a different subnet. This is actually really easy to do in UniFi.
I already have Tailscale running in TrueNAS both at my house and theirs, but neither is an Exit node, and both are setup to add a separate NIC to the host. As far as I understand, Exit node functionality isn’t available when adding a Tailscale NIC.
Potential Tailscale router hardware I have lying around:
- Raspberry Pi 3 Model B. I have a PoE adapter as well as a USB Ethernet adapter.
- SuperMicro X7SPA-H w/ RAM, a PSU, and a USB drive. The CPU is integrated. This has two 1Gb NICs.
If I can’t use TrueNAS’s Tailscale for this, my idea is to use one of these configurations with the Raspberry Pi or SuperMicro board, whichever makes the most sense:
- pfSense
- OpenWRT
- Raspbian Lite (CLI-only)
With this hardware and the need to target only specific devices, how can I get this setup?
Lastly, I’m not familiar with Tailscale enough to know how devices on my parents’ network can use the Internet as if their public IP is at my house. Do I also need a Tailscale exit node at my house?