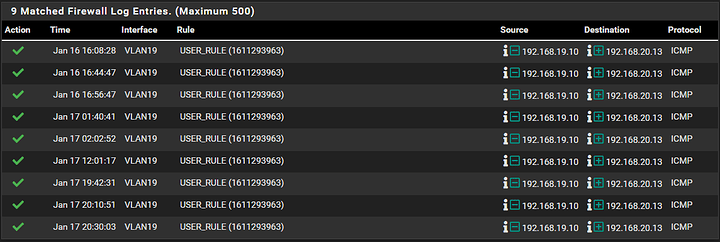
The .10 source ip address really doesn’t make any sense … are you doing something in the Outbound/NAT sections?
can you post a route print on the 192.168.20.13 machine?
can you run a packet capture while pinging from the gateway?
Sorry I was so tried last night I forgot to mention that when I did the packet cap I was running a ping test from a Windows system on VLAN 19 to the target system on VLAN 20.
The source system had an IP of 192.168.19.10
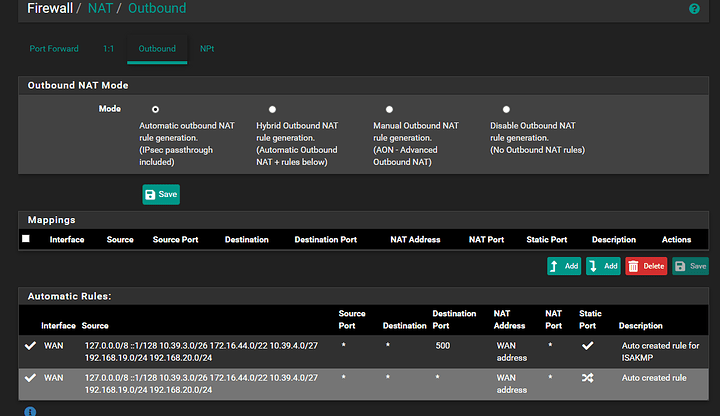
Nothing fancy or out of ordinary on outbound NAT. Everything there is standard NAT as created on install.
Let me try another packet cap
@MadMatt Just out of curiosity, are you able to ping between your VLANs? (Assuming you have it setup that way)
Yeah, the point of having pfsense in the middle of vlans is to be able to decide what goes through and what gets blocked
I have one internal VLAN that is allowed out to all other VLANS except GUEST, then have some other VLANS where incoming traffic to LAN and others is blocked , but I can temporarily enable ICMP to perform tests, then I have single rules (actually, one rule, to my MQTT server for IOT) to allow traffic in from untrusted local LANS
There’s 3 IPs you can try pinging from each of the two computers, whilst looking at ICMP packet traces.
e.g from 192.168.19.10 you can (or should be able to) ping:
192.168.19.1, 192.168.20.1, 192.168.20.13
… same from the other side.
So 192.168.19.10 (Windows host) can successfully ping:
19.1
20.1
but not 20.13
Ok so I guess my next question is how do I do a capture from the gateway, say 192.168.19.1 to both/either 192.168.20.1 and 20.13?
Ok so I can ping from VLAN 20 gateway to the VLAN 20 host (20.13) BUT I cant ping VLAN 20 host from anywhere else.
So with this and all the stuff posted above mean its the firewall?
I feel like if it was a switch issue we wouldnt even get this far. My original concern was the tagging of the VLANs but as we test further it seems less likely thats the issue, what do you guys think?
Might be helpful if you can post screenshots of Firewall → NAT → Outbound and Port Forward.
Do your hosts have the interface address of their respective VLANs set as their gateway?
Hey Dex, long time no see. Thanks for dropping in.
Yes, hosts on VLAN 19 has 19.1 as gateway.
Hosts on VLAN 20 has 20.1 as gateway.
So I had extra hardware to spin up another instance of pfsense and omited the pfsense box we were working with and setup everything as I did on the old one as far as configs go (Mainly just VLANs 19 and 20 with DHCP on each) and still no dice with pinging from one host to another.
So either Im missing a config on pfsense on both or its something with the switch.
Im all ears to any ideas. Thanks again for everyones help thus far.
Also just to confirm, the switch can be in Layer 2 mode for all this correct?
Thanks all I got it working, will update in the AM. Too tired atm
Yep, being able to ping 20.13 from gateway (20.1) across a switch means Ethernet/VLANs are fine.
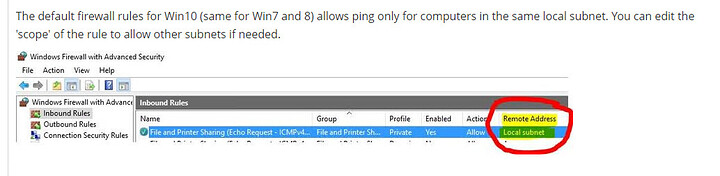
I’m betting it’s probably firewall on the 20.13 host that’s dropping ICMP from non local network.
Wireshark on Windows captures packets before firewall (same with tcpdump or tshark or Wireshark on other platforms).
And I think if you checked you’d be able to see ICMP echo requests coming out of the switch and into your Windows host (19.10 → 20.13).
You already did a packet capture on vlan20 on pfsense and that was fine, the only difference between packets from gateway and packets from 19.10 is the source address.
You nailed it, this is what got me. Posting in case someone comes across this post in the future.
If you want to change it, in Windows Firewall, see the screenshot below. Under Inbound Rules.
Thanks for everyone’s help, if theres anything I can do to pay yall back please LMK.