I had my parents test it on their Roku. Took forever to figure out OpenWRT, but here’s what I did.
I have Tailscale configured with public DNS**. That’s important if you want to do this yourself the way I did.
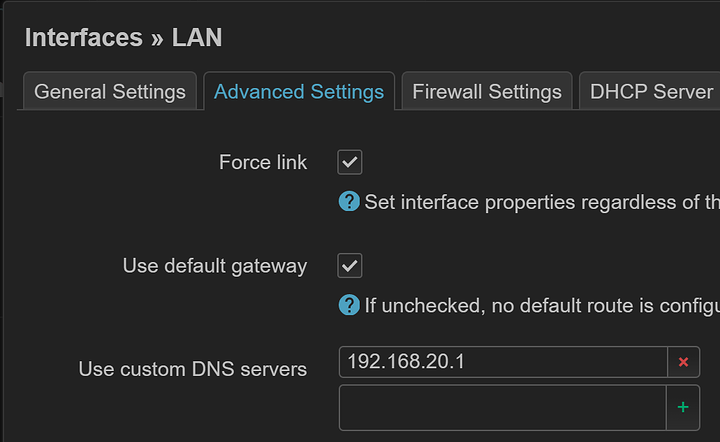
Step 1 - Reconfigure Gateway on their Network
Their router is currently OpenWRT, not yet UniFi, so this is what I did.
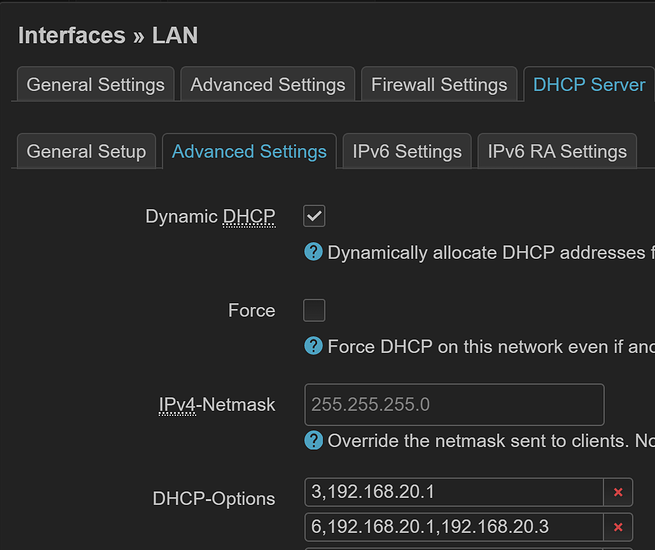
Update /etc/config/dhcp:
config host
option name 'nas'
option ip '192.168.20.144'
option mac 'D0:50:99:C2:B7:0E'
config host
option name 'RokuUltra'
option ip '192.168.20.142'
option mac 'AC:AE:19:FC:21:A4'
option dns '1'
option tag 'gateway_to_my_network'
config tag 'gateway_to_my_network'
list dhcp_option '3,192.168.20.144' # Gateway address
list dhcp_option '6,100.100.100.100' # Tailscale's DNS server
After changing that config, run these commands:
uci commit dhcp
/etc/init.d/dnsmasq restart
After I did that, they had to unplug and plugin Ethernet on the Roku, so it could pull the correct IP information.
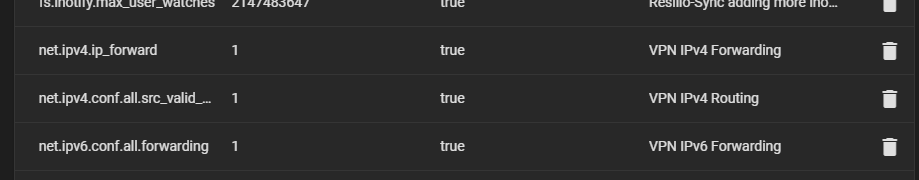
At this point, all traffic is routed through the NAS which as IP forwarding enabled:
Step 2 - Setup Exit Node on NAS in their network
I needed to both connect to the exit node in the Docker container, and I needed to route all incoming traffic to Tailscale as well.
This box does not need to be a subnet router. I wasn’t able to test that situation.
Access the Tailscale Docker container’s shell and run:
tailscale set --exit-node=MY_NETWORK_NODE_NAME --exit-node-allow-lan-access
Change MY_NETWORK_NODE_NAME to the name of the exit node.
Then go to TrueNAS’s shell and run this:
sudo iptables -t nat -A POSTROUTING -o tailscale0 -j MASQUERADE
This sets all incoming traffic to pass traffic through to tailscale0 using NAT, so all IPs appear as though they’re they NAS’s Tailscale IP.
Done!
And that’s it! Once those steps are done, you can circumvent Netflix’s one-house policy ![]() .
.
This was a fun project.