Tonight, I tried OpenWRT w/ Tailscale on a spare Raspberry Pi and even set up a pfSense server on a spare SuperMicro server board, but I’ve run into multiple issues in both cases.
Adding the interface
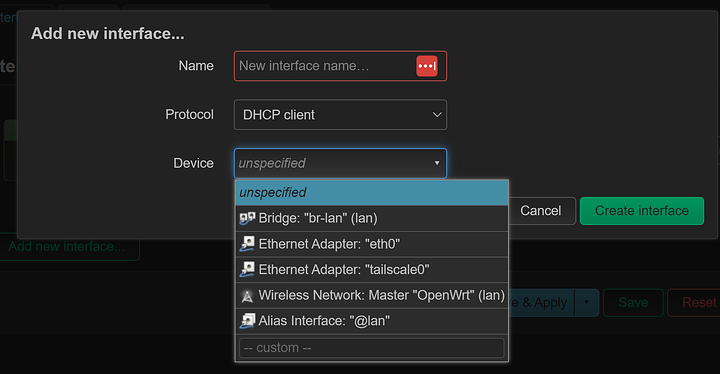
If I add the tailscale0 interface to OpenWRT, then it completely kills the Tailscale connection:
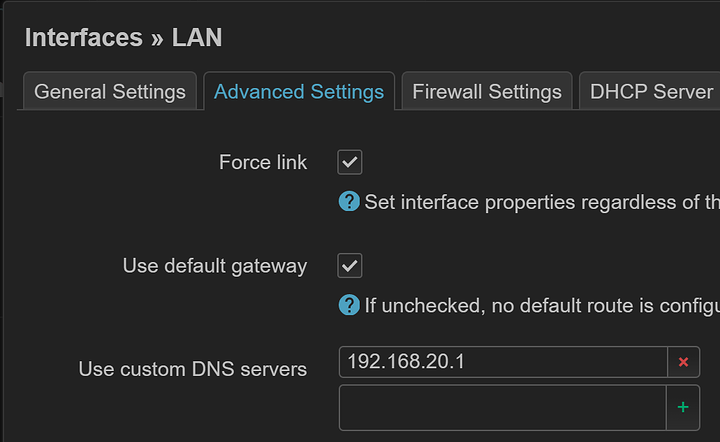
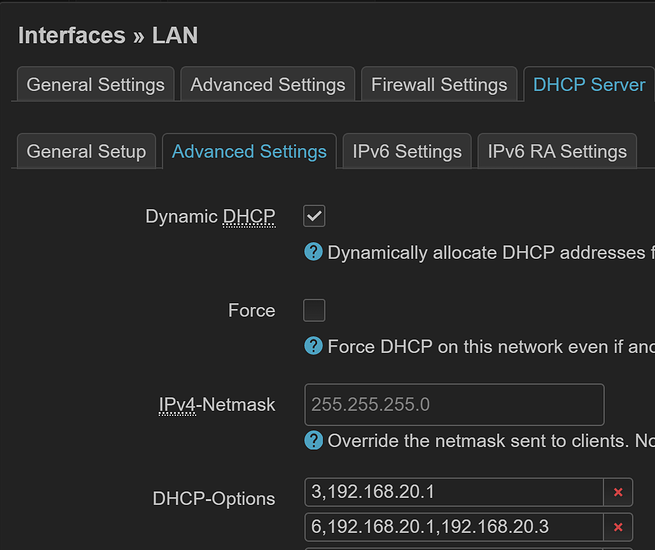
I’ve tried both “Unmanaged” and “DHCPv6 Client”.
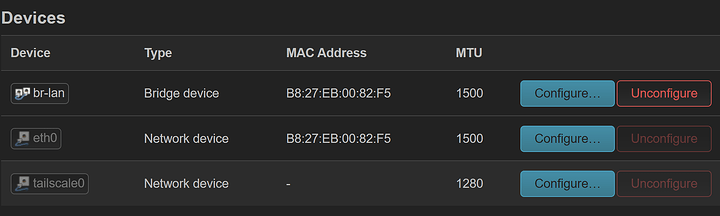
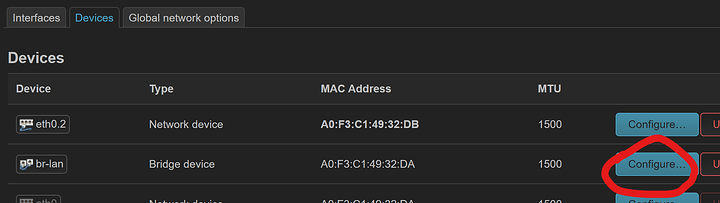
Narrowing it down, it seems like clicking “Configure” on the Devices screen is the cause:
I haven’t got it configured right now, but clicking “Configure” happens when you create an OpenWRT interface. I think OpenWRT tries to claim the interface and the Tailscale app loses access.
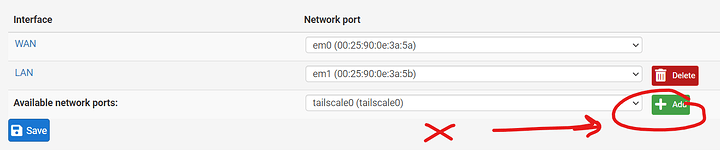
Surprisingly, the same thing happens in pfSense:
When adding the interface, Tailscale loses access.
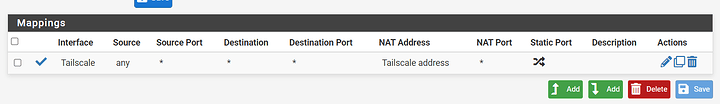
Route mappings
While it didn’t add these mappings automatically as it should’ve, I can setup Tailscale mappings for outbound traffic in pfSense:
OpenWRT won’t let me because it only lets you route between OpenWRT interfaces, not physical interfaces.
Connecting to an exit node
I tried doing --exit-node=REMOTE_EXIT_NODE_NAME in pfSense, and it took it, but nothing appears to work. When trying to grab my IP in the CLI, it’s the local public IP, not the exit node’s public IP.
pfSense seems to expect you only want to use the router as an exit node; not that you want to connect your entire network to another one for outbound traffic.
When running the same --exit-node=REMOTE_EXIT_NODE_NAME command in OpenWRT, it actually shows the exit node’s public IP! But since I can’t route any traffic, this is pretty much useless.
At this point, it makes me wanna go back to Raspbian and try to mess with iptables manually (yuck). I’m not skilled enough to do any of that though.
I haven’t configured any routing from LAN to Tailscale just yet, but I really need to figure out the --exit-node situation in pfSense before I do that.
If I could get routing in OpenWRT to use the virtual interface rather than the OpenWRT interface, I’d be set!