Hello,
I’m trying to setup PIA on my pfsense router.
I created a CA and a user Cert.
But when i create a client on openVPN it starts to push all my traffic though the VPN.
The setup i want is that just the traffic of 2 server go through the VPN.
But it still have to be able the connect to 3 webpages 2 on port 80 and one on port 5050
Could some one help me. I tried to follow Wendels guides (part 2, part 3). But i just can not get the traffic separated, all goes over the VPN or none at all.
You can make firewall rules to send traffic over different gateways, look in the advanced section of the firewall rules. If you’ve configured the VPN to be the default gateway then you must have any rules which use a different gateway above the rule which allows all traffic over the default gateway as rules are processed top to bottom on first match.
To send individual websites over a different gateway you can create an alias in the alias section for the domain name and then use that alias in the firewall rule. it’s not 100% reliable but it seems to work most of the time.
so I should move all the PIA rules in the nat-outbound down and group them belowe all the default gatway rules.
And also in the rules-lan section.
recap:
firewall-NAT-outbound:
- default rules
- PAI rules
firewall-rules-LAN:
- default
- Vlan
- PIA
And to the block rules come before or after the allow rules?
Yeah i’m a total firewall noob 
The outbound nat rules don’t matter, the order anyway.
It depends what you’re trying to do. Post some screenshots, that will make it easier.
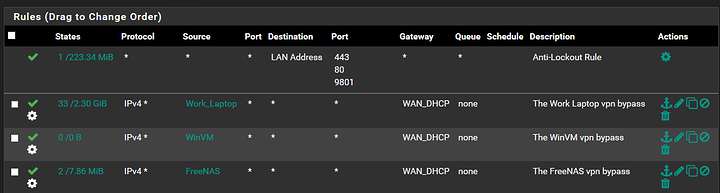
So, all your bypass rules should be on the LAN tab under Firewall>Rules. If you have specific hardware that you want to bypass the VPN completely, then set those up with static ips and an aliases. See the rules I have set for some of my hardware below.
I have a hard time to believe i have to give all my devices a static ip to route the traffic over default gateway.
With the rules like belowe i still get that all the traffic is router over the VPN.
Also if i disable “DO NOT VPN TUNNEL RULE”
still all traffic goes over the VPN.
if have setup my rules like this:
Outbound
Lan rules
The guide that PIA provides on their website assumes that all traffic should go through the VPN by default and you must select which devices and/or ip ranges that you wish to route outside of it. I would think that the guide that @wendell did is based on the same assumption but it’s been awhile since I watched it and I setup mine a couple years before that video.
The PIA guide has you duplicate all the WAN outbound NAT rules and then assign the new rules to the openVPN interface. So, all the traffic leaving the system is translated for the WAN and VPN by default (this doesn’t determine which interface the traffic leaves). You might try setting up the PIA outbound NAT to only translate the sources that you want instead. There are probably many different ways that it could be accomplished but I would think using policy routing with fire rules would be better though.
You would need to setup static ip’s for your 2 servers outside the range of ip addresses that all your other LAN devices use. Then setup an aliases that covers the ip address range for that segment of the network, then put a rule like the ones I pasted in to route all that traffic through the WAN gateway at the top of the list.
I selectively route things outside my PIA and I’m not a network professional so I can’t say that will work without testing it myself. I have setup bypass rules for specific hardware, ports, and address ranges. You can tell that any one rule is working by keeping an eye on the “States” column. You will see the number of states and the amount of data traffic that the rule has processed.
If you want those ports to be open even through the vpn then you’ll have to connect to one of PIA’s servers that allows port forwarding.
I don’t know what those aliases contain for the bottom rules but for Internet access you need atleast one rule with a destination of any. Put an allow any to any rule at the bottom with whatever you want your default gateway to be and then above that have specific rules for any traffic you don’t want using that gateway.
If you don’t want the VPN to be the default gateway then you need to check the ‘don’t pull routes’ box in the VPN client setup. Then you will have to make firewall rules which will specify which traffic to send where, and these rules will have to be above any rules which match the traffic, like the any to any rule.
Also, right at the top you have a rule which is sending all traffic over the default gateway, except the traffic to the other vlan, that’s making any other rules you have for Internet destinations useless.
You also have source address from different subnets, the only valid sources are addresses on that interface, so in this case only the IPs of devices on the LAN.
It can be tricky to warp your head around but this try to remember that rules are processed top to bottom and the first match applies only. And that the source has to be on the interface you’re making the rule for and the destination have to be on a different interface or pfsense itself.
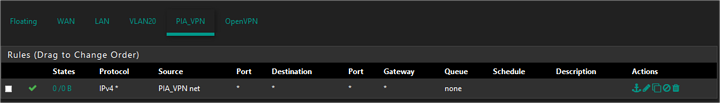
I checked the box and setp the rules up like this.
outbound
Lan rules
PIA_VPN
Don’t know if i’ve done it the rightway but it seems to work 
Delete the allow rule on the PIA interface, you don’t want to allow any traffic in on an Internet facing interface.
I don’t know what’s in that PIA alias but I doubt you need both those rules. If the alias is for local hosts then get rid of the second rule that has the alias as the destination. If its both local and Internet then make separate aliases.
You still have rules with source addresses in a different subnet, you should delete those or move them to the interface for that subnet.
Hey this is all set, yes? If not, let me know.