Preface:
I’m wanting to learn more about security operations (am currently a system and network admin, got Sec+ a few months ago).
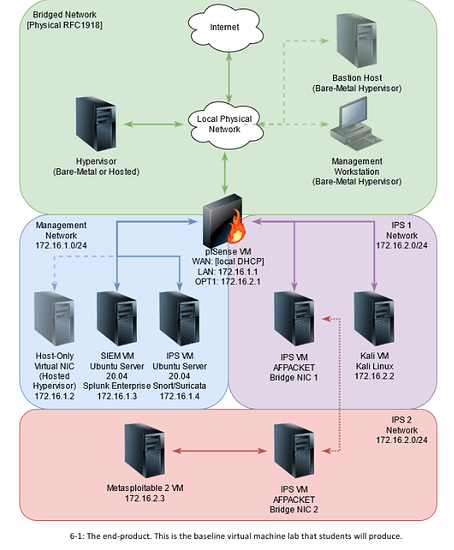
I found this network diagram in a book, and was wondering if all the SEIM and IDS recommendations are still the standard for home lab use.
I’m mainly planning on looking at the logs when attacking VMs from VulnHub (and/or OffSec Proving Grounds (I know about HackTheBox, but I don’t really like their hand-holding approach. I want something more of a real-world pentesting senario)).
Long term, I’m planning to use these for practicing for OSCP and transitioning into a more security focused position.
Let me know if you think this is a wise direction for my goal.
Thank for for your time!
1 Like
A SIEM is really two parts, one that collects logs, and one that analyses logs. For the first Elastic Search (in an ELK stack) is pretty standard, and most products are built on this. However the hard bit is having a good dashboard that allows you to analyze and report on your data. The second one is mainly something you’ll find in expensive enterprise products, especially when you start talking about threat feeds and TLS decryption.
Personally I’ve looked at Security Onion before, but it’s more of an IDS itself. It’s decently easy to install and has many tools included, including ELK for monitoring and analysing the IDS data. So I’d suggest giving that a go.
Splunk is a paid product, but IIRC there is a free version for under a certain log volume. I think Graylog might be another option.
1 Like
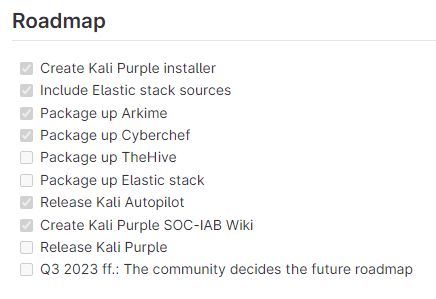
Update - something to keep an eye on:
Kali Purple - SOC In a Box
Kali Linux / kali-purple / Documentation · GitLab
Current Status: