just as a suggestion, I would get everything working the way you want it first and then configure it run automatically at boot. And I would start by getting the openvpn and nat to work properly and then add the filter table rules once you’ve got that working.
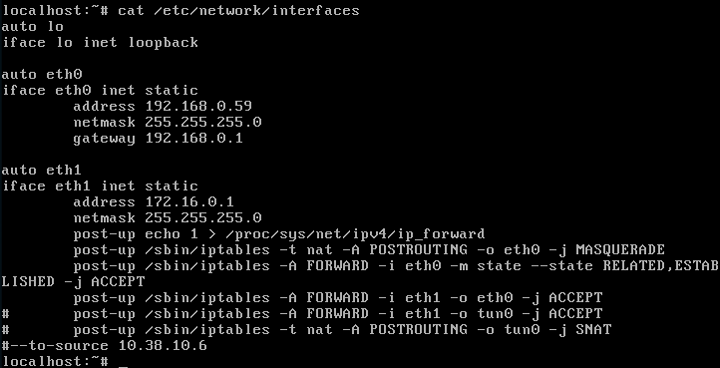
Ok, so my /etc/network/interfaces now looks like this:
My ./script.sh looks like this:
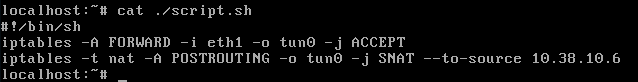
And after I run this:
I can’t access the internet from NAT’ed VM.
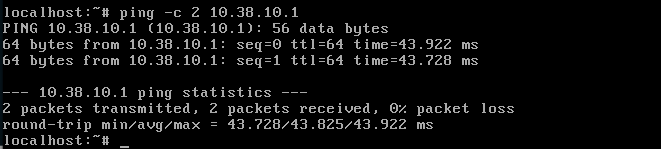
Can your ALG host ping PIA (ping -c 2 10.38.10.1) through the tun device after openvpn has initialized?
No.
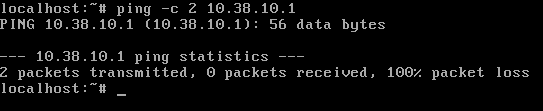
That’s not great. If that’s the case then your tunnel is not actually working. Will you just run
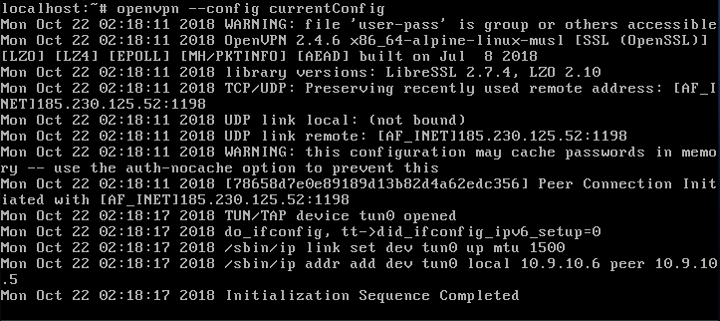
openvpn --config currentConfig
and post the output.
Oh no, you aren’t getting a static address local address, so --to-source (the address you had several tries ago) is definitely not going to work.
After you ran openvpn --config currentConfig, can you VM 1 or 2 ping 10.9.10.6?
Yes, I can.
Well then you are almost there, from this point manually SNAT (just use masquerade so we don’t have to worry about the address) the traffic from vm 1 & 2 so:
iptables -t nat -A POSTROUTING -s 172.16.0.0/24 -o tun -j MASQUERADE
and then allow forwarded traffic leaving tun0 though
iptables -A FORWARD -o tun0 -j ACCEPT
and your rule "FORWARD -i eth0 -o eth1 -m state --state RELATED,ESTABLISHED -j ACCEPT is suspect because it won’t allow the tun0 return traffic back to the VMs. Just delete to “-o eth1” part.
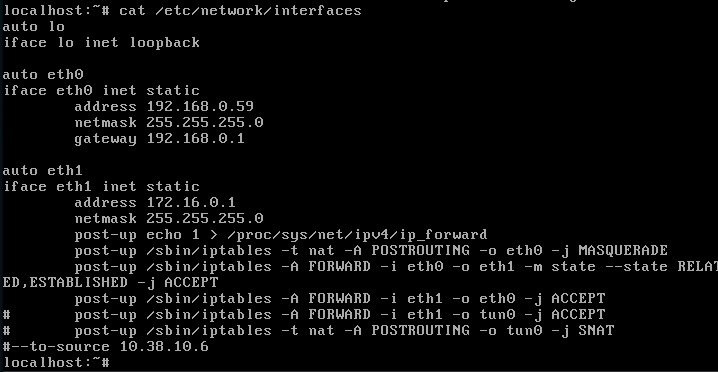
So this rule should look like this then, right?
FORWARD -i eth0 -o eth1No get rid of the “-o eth1” part, so it would look like:
FORWARD -i eth0 -m state --state RELATED,ESTABLISHED -j ACCEPTOk, so:
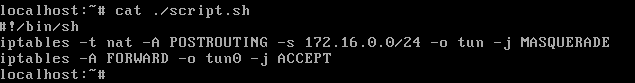

And now my VMs can’t access the outside world.
But I can ping 10.63.10.6
EDIT: changed tun to tun0 from screenshot of ./script.sh and it seems to work!
Thank you very much!! 
damn typos. Good deal.
Ok I see now. My bad I misunderstood the situation a bit.
I know this isn’t really what you need, but I thought maybe someone else would find this rule useful.
iptables -I FORWARD 1 -m mac --mac-source xx:xx:xx:xx:xx:xx -d yyy.yyy.yyy.yyy -j ACCEPT
iptables -I FORWARD 2 -m mac --mac-source xx:xx:xx:xx:xx:xx -j DROP
I basically use this rule on my router to restrict certain VM or NIC(xx:xx:xx:xx:xx:xx) to one IP address.(yyy.yyy.yyy.yyy) From that VM I connect to openvpn server that is on (yyy.yyy.yyy.yyy)