I probably have places in Las Vegas we could use
I like the Navy. I do not want them to not like me.
I also like my life.
San Clemente is not going to happen.
Real talk bro, I think we just need to find a long 200+ mile link that we can easily get LOS to.
Still up against alot. More frequent better quality links will transmit better and more reliably and faster despite more links that stuff that is at the edge of its capability
Also its very difficult to do that. Like realize we are up against physics and the curvature of the earth here too. You should do a bit more ham study on the physics questions and the esoteric modes like ionospheric bounce etc and understand why they happen and how the fresnel zone works and stuff.
We can model the links but even if our model said its perfect. We could go out there and find no signal you know. Thats why I say lots of learning to do and studying and evaluating and testing haha
Im down when the funds and time is right though. Obviously not right this second in winter ![]()
that’s totally fair.
reflecting signals against the sky (or rather clouds)?
Also
It can be done on only some frequencies and only temporarily. Air currents and layers are ephemeral
Get on TS tonight. we will chat about the physics and the topics here
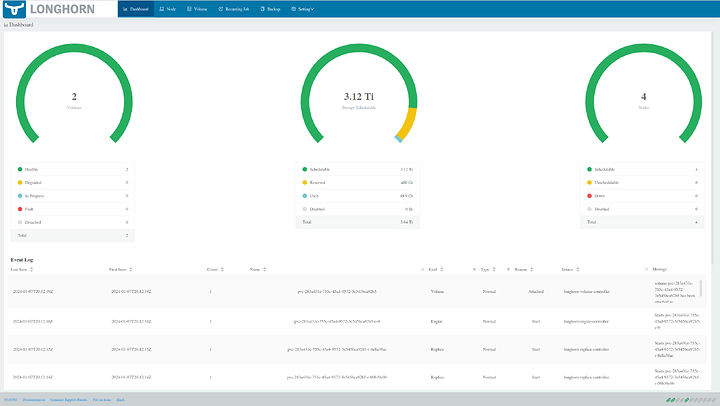
Okay longhorn here we go
Ansible Prep
preplonghorn-nordrljos.yml
- name: Prepare cluster for longhorn storage
hosts: "nordrljos"
become: yes
tasks:
- name: Push Apt Sources
template: src=../templates/sources.list dest=/etc/apt/sources.list
- name: Update Cache
apt:
update_cache: 'yes'
- name: Update nfs-common package to latest version
apt:
name: "nfs-common"
state: latest
- name: Update open-iscsi package to latest version
apt:
name: "open-iscsi"
state: latest
- name: Enable service open-iscsi and ensure it is not masked
systemd_service:
name: "open-iscsi"
enabled: true
masked: no
- name: Make sure open-iscsi service unit is running
systemd_service:
state: started
name: "open-iscsi"
Create basic auth secret
USER=<USERNAME_HERE>; PASSWORD=<PASSWORD_HERE>; echo "${USER}:$(openssl passwd -stdin -apr1 <<< ${PASSWORD})" >> auth
Kubectl store secret
kubectl -n longhorn-system create secret generic basic-auth --from-file=auth
basic bitch ingress
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: longhorn-ingress
namespace: longhorn-system
annotations:
# type of authentication
nginx.ingress.kubernetes.io/auth-type: basic
# prevent the controller from redirecting (308) to HTTPS
nginx.ingress.kubernetes.io/ssl-redirect: 'false'
# name of the secret that contains the user/password definitions
nginx.ingress.kubernetes.io/auth-secret: basic-auth
# message to display with an appropriate context why the authentication is required
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required '
# custom max body size for file uploading like backing image uploading
nginx.ingress.kubernetes.io/proxy-body-size: 10000m
spec:
rules:
- http:
paths:
- pathType: Prefix
path: "/"
backend:
service:
name: longhorn-frontend
port:
number: 80
Apply ingress
kubectl -n longhorn-system apply -f longhorn-ingress.yml
get svc
kubectl -n longhorn-system get svc
hopefully profit?
TODO: Ansiblize the entire process
So that didnt go well. For some reason kube says I have a no valid ingress class for longhorn ![]()
Fixed the name space issue. Longhorn is up
Grafana is up too
Also note to self
openssl rand -hex 32 > /etc/zfs/zkeyFiles.d/nextcloud && zfs create -o encryption=aes-256-gcm -o keyformat=hex -o keylocation=file:///etc/zfs/zkeyFiles.d/nextcloud OnePoint21GigaWatts/nextcloud
The next step is ssl for internal.tld.net … Going to need to allow list my LE account but I have no idea how to find the cert-manager kube instances account id
What watch is this? I think I wanted to sport smart watches but everything sucks in one or multiple ways that I gave up.
Also is it always on OLED?
Fossil Gen 6 Gunmetal
Gonna check it out now. At least its a brand I can sort of buy locally.
It seems that it is still not for me. The Asteroid OS page for this particular watch isnt complete yet and I dknt know how repairable it is. Sad to say that most of the newer watches with nice features in their list are held by glue (instead of screws and gaskets).
No thread highjack but i work in SD a few days once a month, would be cool to meet.
@SgtAwesomesauce and @PhaseLockedLoop how about a baby step and do a meshtastic ‘gateway’ mqtt broker and make a lvl1 channel? It would get around range issues albeit not as off grid and private as desired (can always make other channels only be LoRa only) but i believe when a node gets into radio range it would still work. Meaning it works over the Internet for long distance, but say either of you visits the south bay you would also have direct LoRa connection (if my nodes added to that channel)
Thats a tough drive for me to make atm
Id prefer it fully off grid haha. AES-256 over the internet has been solved
I’d be down for an SD meetup aswell
Yeah id be down for it just not in the near term. Lots of stuff on the calendar
I’d be down, hit a brewery one day? Won’t have time in January, but Feb should be openish.