No. I live a non live notifications life is the life. I disconnect regularly. I dont always live attached.
Someone thinks that I have notifications for things.
I did not say you lol
I need to go “back to school” on this…lol My books are proving not as useful as I’d hoped lol
Try looking online for CCNA resources. If you want the certification, buy the courses. CCNA is in more high demand only because of brand recognition and they arguably offer some more advanced knowledge than CompTIA. They are Cisco specific most of the time (in some labs, you may do OSPF and LACP, which are open standards), but if you know one, you basically know them all, just a difference in terms and commands used.
Took a while to figure out how to mitigate the 53 DDoS.
Basically my situation was I could not stop the incoming flood traffic, well guess what …? iptables string-match rules can be used as a last resort. Keep in mind that string matching is resource-intensive and may slow down your network speed and your servers btw… however if you need to shut out an attack, this option is better than letting your server continue to answer the abusive queries to port 53
so the first thing I did was get a hex-dump of the packets I wished to block. tcpdumping them out
tcp6dump -c10 -pntxi eth0 not udp src port 53 and udp dst port 53
The option -c10 specifies that you only want to dump out 10 packets at a time from port 53 only looking at input.
I was seeing this bullshit
IP [05e9:3aa4:3230:86b9:0737:5c22:13ff:f2ad].59174 > [2600:3c04:0:0:f03c:92ff:fec6:2030].53: 92732+ [1au] ANY? . (28)
0x0000: 4500 0038 a48c 0000 f111 4e02 4509 64f2
0x0010: d857 54d3 e2f4 0035 0024 0000 aa3d 0100
0x0020: 0001 0000 0000 0001 0000 66ff 0432 1189
0x0030: 5348 0000 0000 0000
IP [05e9:3aa4:3230:86b9:0737:5c22:13ff:f2ad].16326 > [2600:3c04:0:0:f03c:92ff:fec6:2030].53: 92733+ [1au] ANY? . (28)
0x0000: 4500 0038 d50a 0000 f111 2220 636c 41f3
0x0010: d857 54d3 4700 0035 0024 0000 9f8b 0100
0x0020: 0001 0000 0000 0001 0000 66ff 0432 1189
0x0030: 5348 0000 0000 0000
Guess what theres a common conseutive set of bytes here… 0000 0001 0000 66ff 0432 1189 5348 0000 so the iptables rule, you want to remove all the spaces between bytes, and drop the results into a rule like this:
iptables -I INPUT -p udp -m string --hex-string "|0000000000066ff0432118953480000|" --algo bm --dport 53 -j DROP
BINGO Running this rule will immediately shut out all matching queries, preventing your server from wasting time and bandwidth trying to answer them.
The next steps were basic
Establish throttling:
iptables -A INPUT -p udp -m hashlimit --hashlimit-srcmask 24 --hashlimit-mode srcip --hashlimit-upto 120/m --hashlimit-burst 30 --hashlimit-name DNSTHROTTLE --dport 53 -j ACCEPT
iptables -A INPUT -p udp -m udp --dport 53 -j DROP
iptables -A INPUT -p udp -m string --hex-string "|00000000000103697363036f726700|" --algo bm --to 65535 --dport 53 -j DROP
iptables -A INPUT -p udp -m string --hex-string "|0000000000010472697065036e6574|" --algo bm --to 65535 --dport 53 -j DROP
iptables -I INPUT -p udp -m string --hex-string "|0000000000066ff0432118953480000|" --algo bm --dport 53 -j DROP
iptables -A INPUT -p udp --dport 53 -m string --from 50 --algo bm --hex-string '|0000FF0001|' -m recent --set --name dnsanyquery
iptables -A INPUT -p udp --dport 53 -m string --from 50 --algo bm --hex-string '|0000FF0001|' -m recent --name dnsanyquery --rcheck --seconds 60 --hitcount 4 -j DROP
Disclaimer: *You should always apply to INPUT before FORWARD or OUTPUT
Floods BTFOd
Specific series updated: Infrastructure Series -- Taking DNS One Step Further - Full DNS Server infrastructure - #2 by PhaseLockedLoop
Yeah, if fail2ban is not an option, the last resort is --limit rate and --limit-burst in iptables. But as you mentioned, it’s a little CPU demanding (like any QoS for that matter).
its not. I refuse to block any node from being allowed to access DNS. That to me is a failure of the open internet
AFAIK fail2ban can be set to temporary restrict access, in case of a DoS or DDoS attack. You can also set a higher threshold and legitimate clients will never get blocked, but bad actors and bots will.
links to material on it?
Last I checked it was super easy to evade
Don’t remember, I’ll have to search the web a lot. Not in the mood for it. 
I was looking at your updated network Diagram and curious what you do for Backups?
Currently I’m trying to work out my ZFS on Linux / Cockpit / Podman setup, trying not to use Truenas Scale as it has built-in telemetry and makes me dependent on iX Systems.
Also, did you consider setting up your Linodes as an Outbound Proxy to get around Packet Snooping and censorship, considering you already have a lot of the knowledge and code to set that up with load-balancing as well?
It’s been on my todo-list to get to full dual stack without the privacy concerns and I’ve come up with the plan to use an outbound proxy and my own DNS, for now on Linode and later maybe even on my own server if I can find affordable colocation.
As a person experienced in cryptography. I approve of this laymans look.
Its quite accurate even though its reduced
I use an Elliptic curve Diffie-Hellman and its equivalent to 16384 not 4096 so there will be no need to change my DHE exchange key like literally ever lol
Not to divert from the primary content of your post(s) / fantastic thread, however I am curious – are you still running this great device? I am currently on:
Android version: 12Android security update: October 5, 2021
Unfortunately, there will be no further security updates for November or beyond… one final update coming next year (Q1 2022). I’ve only glanced at LineageOS, haven’t tried it on any of my old devices, but we tend to rely on a number of Google services. As a former Google-fanboi (now recovering), this pains me to have to admit, but it’s been near impossible for me to replicate the convenience factor that comes from this marriage. Just curious where your head is at these days. I will continue using it for the foreseeable future, not sure I could convert to the in-screen fingerprint reader if it’s slow. That’s a deal breaker… same with the 4 XL, face unlock ONLY was another deal breaker. P5 was nice, but it’s hard to give up 1440p once you’re committed. Thanks for this great content, LOTS of wonderful stuff to go through.
Yes I am. Though I dont run Lineage OS.
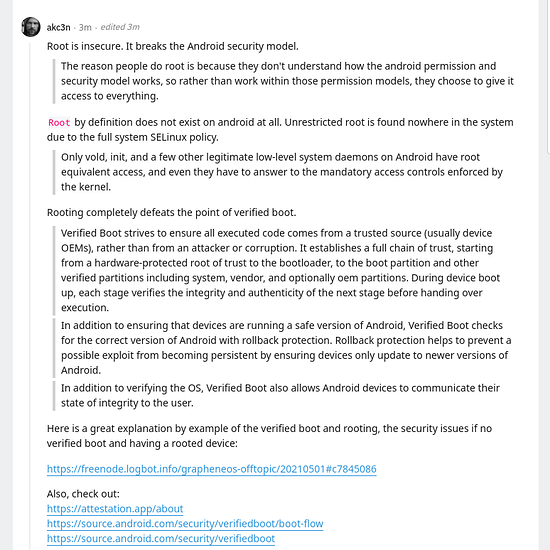
It inherently breaks the security model.
Graphene OS is on extended support for back patches stuff that needs to be done. I dont run GAPPS (Google APPlications Services Framework)
My upgrade path is to the Google 6 Pro upon anouncement and release of the 7. Staying a year behind google grants you a lot of convenience and also price discounts.
The author of graphene isnt a meme. I might call it meme OS to @SgtAwesomesauce but realistically its not. Numerous and I mean a LOT of security patches to android have come out of the graphene OS project. I suspect that is how he sustains the development because he grabs google bounties on occasion (small ones)
It is a testament to device support though. Google supported a 2017 phone to 2022. Nobody can argue with a 5 year support life cycle in the phone market.
Based!