Mr. I forgot to open port 443, one shall not forget to open port 443.
@Novasty you know how cockpit auto updates the system. Is there a way to alias it to do so for tumbleweed
sudo zypper up doesn’t update the system when in tumbleweed. Sudo zypper dup does
Mr. I forgot to add a semi-colon for the nth time.
fuck off  I havent had my coffee with bourbon creme yet… LMAO
I havent had my coffee with bourbon creme yet… LMAO
god dammit. I hate those bugs. I get them in C too… ill forget it and be like why is this fucking crashing you stupid piece of $hit… oh… im the stupid piece of $hit
Conglomerated into various infrastructure series. This is post clean up. Nothing to see here
All of this work preps me for the final step. A large ZFS Raid-Zed2 Pool and a Nextcloud+JellyFin going up soon ™!
Asking for a friend: Does anybody know if the cloudflared DDOS protection is worth it on a home deal?
Just because I enjoy trolling the fuck out of you and I know you have this weird OCD about it.
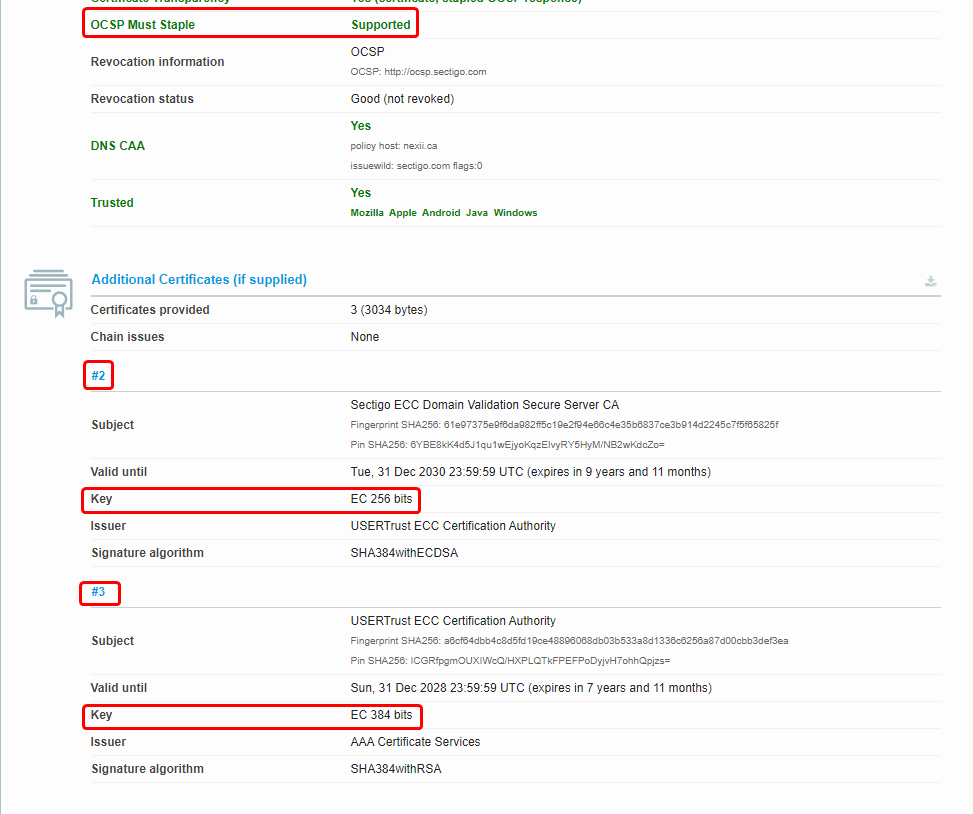
EDIT: I turned off OCSP Must Staple because it broke things for me.
It broke my cockpit page  I’m not doing it again
I’m not doing it again
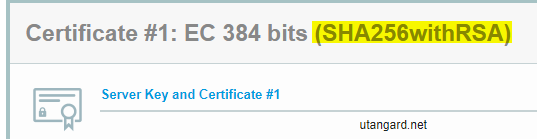
You had your certs reissued for EC huh?
All I know is I finally got an A+ lol
only because I found out the CA has EC roots.
Lame sauce. I think I have to wait on that for letsencrypt. I wanted to move over to all EC. (More efficient keys)
On another end to make you pull your hair out.
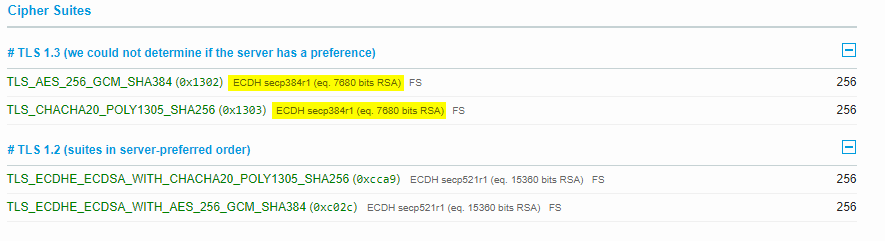
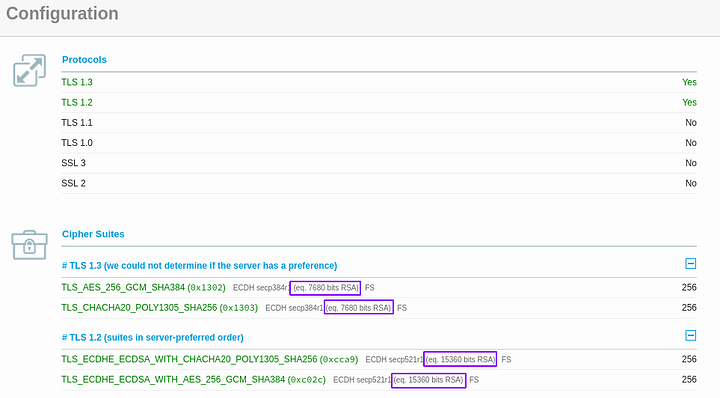
You can change the ecdh curve to be higher than what is shown by default.
REALLY EASILY, I’m never going to tell you though, just so you can agonize on how easy it is.
I know. Did you see mine? Its the same lol
You just have to specify what safe curves you want to use right?
Or did you dirty slap nginx around? I’m guessing it’s SSL because that’s how we got TLS1.3 doing what we would like it to do
I ahh see it, you’re mega post was too long, I probably scrolled past it while reading.
God why does this thread have a solution button I keep accidently pressing it.
Yeah it was long. I wanted to cover what I did in one post.
Its in the additional information section.
I see you too are a man of elliptic curves culture
That A+ was difficult ish to figure out. I kept getting stuck on A like wtf
@Novasty you know what’s strange?
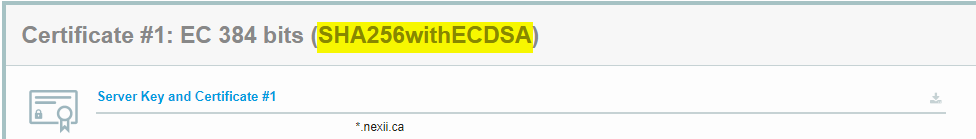
Last night we were talking about letsencrypt not doing CSR by themselves at SHA256 but you could self create higher. I did at 512 and the sign still ended up at 256 lol.
512 is more efficient on modern CPUs. I know we were both shocked
Weird that it lost my 512
Let’s Encypt is big gay. It wont do what I asked, I may purchase a cert.
You use namecheap right? Might as well stop being poor. Was a cool learning process lol!
To be fair beggers cant be choosers.
Im not buying one. Thats expensive for what I am using it for. Ill wait for letsencrypt to stop being gay