listen here u lil shit

Yeah in the end I pay attention to the software quality opposed to the project politics although one can often sour the other one for me. I do however take a more strict stance on closed software, it’s just that the license of specific OSS is usually not that important to me.
On another note, how will you use your Jellyfin? Is it just something you will manually put stuff on or will you auto feed it from, say a reciever card?
I dont have cable so I will be manually curating what I want in there. Preferable full 6ch audio stuff and good quality stuff. Probably going to get the transcoding to be a one and done. Where it transcodes once and doesnt need to waste CPU again
Hard drive space is cheap
● cloudflared.service - Argo Tunnel
Loaded: loaded (/etc/systemd/system/cloudflared.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2020-12-18 00:47:12 GMT; 3s ago
Main PID: 1166 (cloudflared)
Tasks: 9 (limit: 4309)
CGroup: /system.slice/cloudflared.service
└─1166 /usr/local/bin/cloudflared --config /etc/cloudflared/config.yml --no-autoupdate --origincert /etc/cloudflared/cert.pem
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] GOOS: linux, GOVersion: go1.15.5, GoArch: arm64
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Environment variables map[config:/etc/cloudflared/config.yml no-autoupdate:true origincert:/etc/cloudflared/cert.pem proxy-dns:true p
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Adding DNS upstream - url: https://9.9.9.9/dns-query
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Adding DNS upstream - url: https://149.112.112.112/dns-query
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Adding DNS upstream - url: https://dns.quad9.net/dns-query
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Adding DNS upstream - url: https://[2620:fe::fe]/dns-query
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Adding DNS upstream - url: https://[2620:fe::fe:9]/dns-query
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Starting DNS over HTTPS proxy server on: dns://localhost:5053
Dec 18 00:47:12 baldr.yggdrasil cloudflared[1166]: INFO[2020-12-18T00:47:12Z] Starting metrics server on 127.0.0.1:39473/metrics
Dec 18 00:47:12 baldr.yggdrasil systemd[1]: Started Argo Tunnel.
DNS over HTTPS with cloudflared client. LOL jacked your config. I dont want to use yall but thanks for the program!
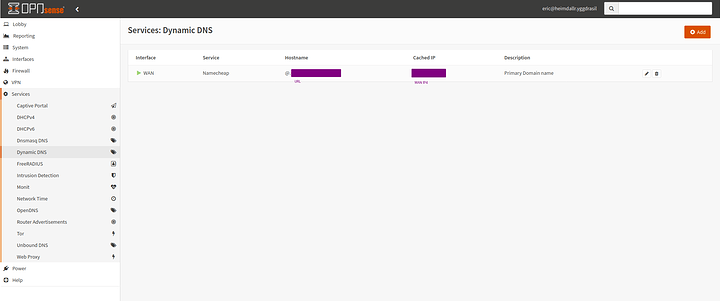
Hey guys I am back. Pressing forward with my deployment of stuff. I have been working on DynDNS as of late.
My progress is slow and I am learning along the way to make sure I do things as correctly as possible the first time.
Pretty basic easy setup in OPNSense services. Its important to realize that when you have all unique IPv6 address (especially if static like in my case) you will use dynDNS to config IPv4 only in the firewall and configure the IPv6 on your DynDNS advanced records area.
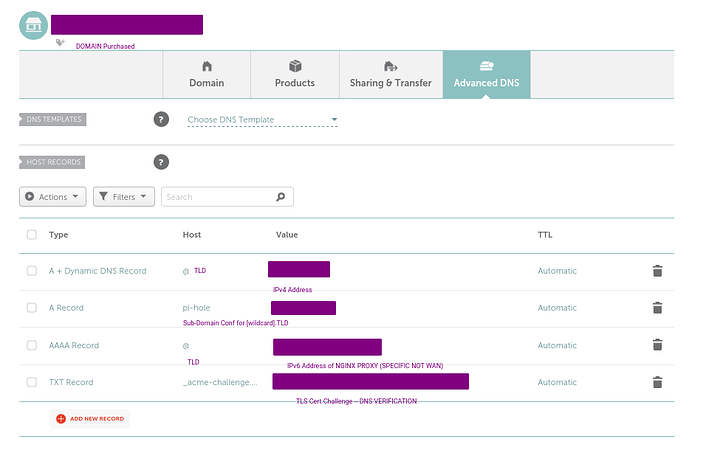
So I am using name cheap as my preferred provider. Why… Well its cheap LOL
As you can see its fairly routine and simple. It took me some time and assistance to get it working but the essence is that @ is all domains and if you want say pi-hole.domain.tld you want ti add it manually so that it propagates.
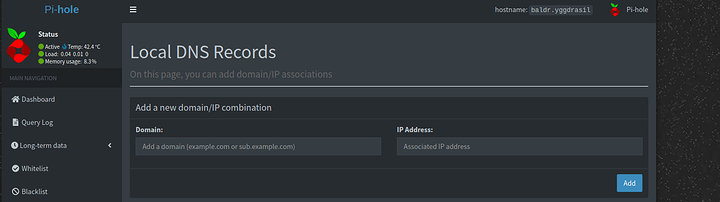
If you have a pi-hole its important to add this to your local DNS records as follows
Adding its address and IP for internal redirect. This is good since it will be cached locally in case you have an external DNS failure.
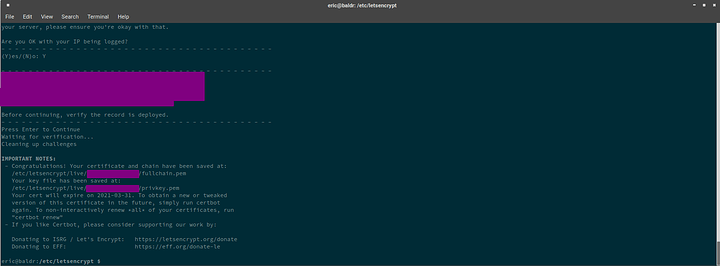
More to come later. Working on TLS as we speak
Dont be a galaxy brain. When deploying… dont deploy text to _acme-challenge.URL.TLD deploy it to simply _acme-challenge.
Thats what it looks like when you dont galaxy brainlet your configuration
Mr. I forgot to open port 443, one shall not forget to open port 443.
@Novasty you know how cockpit auto updates the system. Is there a way to alias it to do so for tumbleweed
sudo zypper up doesn’t update the system when in tumbleweed. Sudo zypper dup does
Mr. I forgot to add a semi-colon for the nth time.
fuck off  I havent had my coffee with bourbon creme yet… LMAO
I havent had my coffee with bourbon creme yet… LMAO
god dammit. I hate those bugs. I get them in C too… ill forget it and be like why is this fucking crashing you stupid piece of $hit… oh… im the stupid piece of $hit
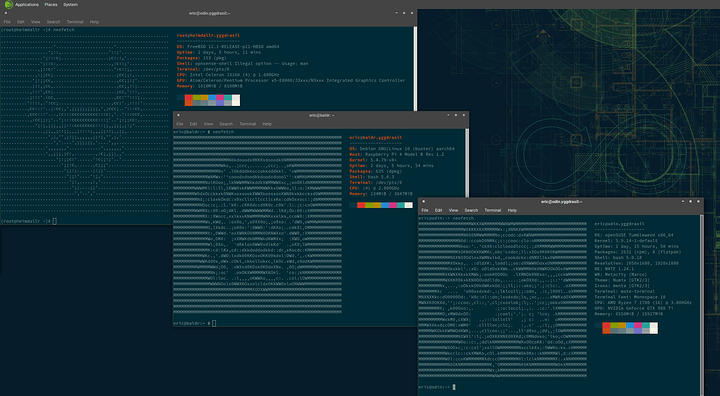
Conglomerated into various infrastructure series. This is post clean up. Nothing to see here
All of this work preps me for the final step. A large ZFS Raid-Zed2 Pool and a Nextcloud+JellyFin going up soon ™!
Asking for a friend: Does anybody know if the cloudflared DDOS protection is worth it on a home deal?
Just because I enjoy trolling the fuck out of you and I know you have this weird OCD about it.
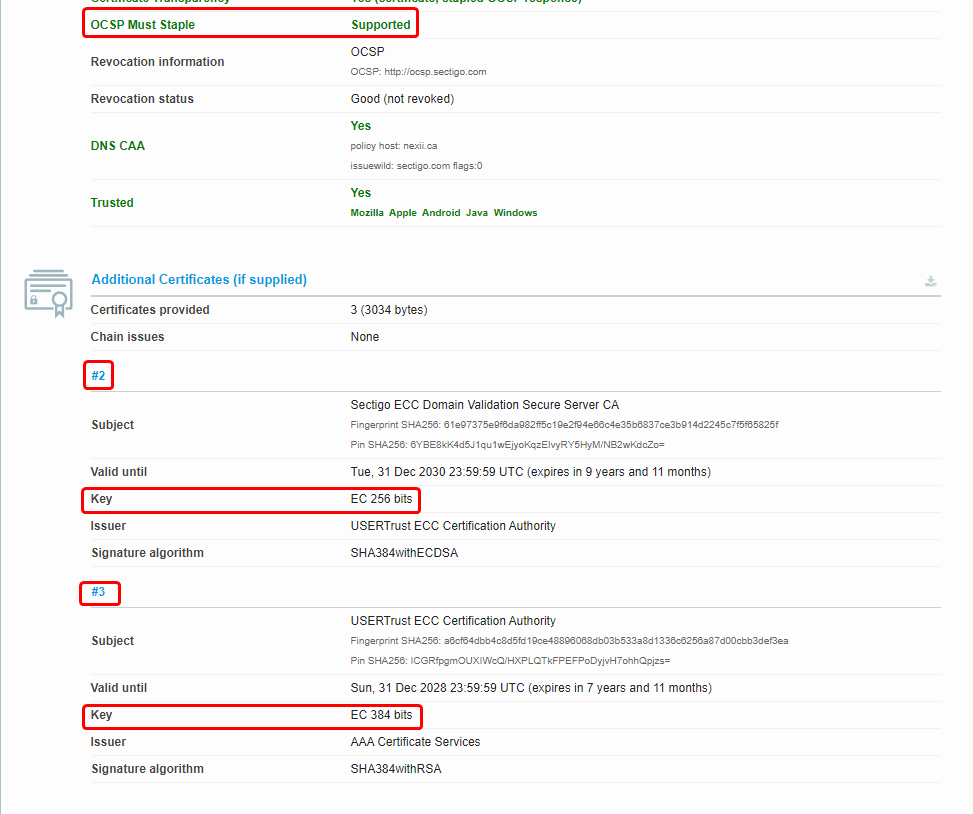
EDIT: I turned off OCSP Must Staple because it broke things for me.
It broke my cockpit page  I’m not doing it again
I’m not doing it again
You had your certs reissued for EC huh?
All I know is I finally got an A+ lol
only because I found out the CA has EC roots.
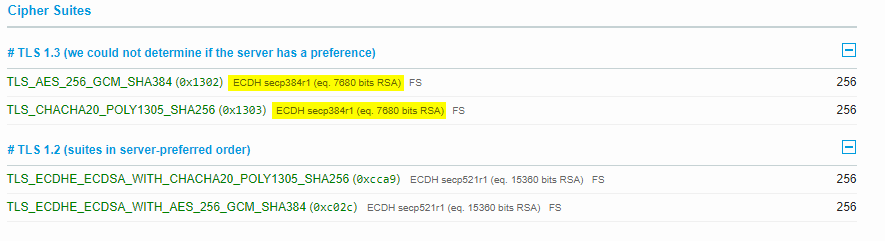
Lame sauce. I think I have to wait on that for letsencrypt. I wanted to move over to all EC. (More efficient keys)